Exploring the effects of personal and situational factors on cyber aggression
Vol.18,No.3(2024)
Antisocial behaviour by social media users has escalated, which in turn has created various socio-psychological implications for users and society at large. However, there is a paucity of empirical research on the concept of cyber aggression inclination (CAI) and its personal and situational antecedents in the context of social media. This study explores and measures the CAI of general social media users and examines the personal and situational factors affecting CAI. Data was collected using an online survey resulting in a sample of respondents who are active social media users. A total of 101 responses were received of which 71 were complete. Primary data was analysed using Partial Least Squares-Structural Equation Modelling (PLS-SEM) to test eight hypotheses. Findings suggest perceived anonymity, impulsive use of social media and subjective norms are correlated with and CAI. We could not find any conclusive evidence to suggest a significant association exerted by prior aggression victimisation, social pressure, and perceived incident severity on CAI. This paper makes original contributions to the field of cyberpsychology where a more specific form of antisocial behaviour has been studied in social media settings.
cyber aggression; self-control; subjective norms; perceived anonymity; social networking sites
Hemamali Tennakoon
Brunel Business School, Brunel University London, Uxbridge, United Kingdom
Hemamali Tennakoon is a Senior Lecturer in Strategy and Management at Brunel Business School (BBS), Brunel University London. She received her PhD in Online Information Security, Privacy and Social Commerce from Kingston University, London. Her research has appeared in peer-reviewed journals including Computers in Human Behaviour, Information Technology & People, and International Journal of Human-Computer Studies. Hemamali is a Fellow of the British Computer Society. Her main research interests include cyberpsychology, digital anthropology, online privacy and security.
Lucy Betts
Department of Psychology, Nottingham Trent University, Nottingham, United Kingdom
Lucy Betts is Professor of Social Developmental Psychology at Nottingham Trent University. Her research interests are in social developmental psychology, focusing on cyberbullying experiences, perceptions of online risk and understand the distinction between bullying and banter.
Anil Chandrakumara
School of Business, Faculty of Business & Law, University of Wollongong, Wollongong, Australia
Anil Chandrakumara earned his PhD in International Organisational Behaviour (OB) and Management from the University of Sheffield (UK). His research work is published in several international journals such as the International Journal of Manpower, Employee Relations International Journal, Thunderbird International Business Review, Australian Accounting Review, International Journal of Management, Corporate Ownership and Control, International Employment Relation Review, and in proceedings of international conferences. His current teaching-research nexus includes international OB, Cross-cultural management, Global business strategy, Ethics, CSR, and Sustainability in institutional and global context.
George Saridakis
Business School, University of Kent, Canterbury, United Kingdom
George Saridakis is a Professor of Small Business and Entrepreneurship and the Head of the Department of Marketing, Entrepreneurship, and International Business (MEIB) at Kent University. He holds a Ph.D. in Economics from Essex University. His research has been presented at numerous conferences, and he is the recipient of many distinctions, honours, and prizes. He has published several journal articles, edited books, book chapters, and official reports. Additionally, he holds an honorary position at The University of the West Indies.
Chris Hand
Business School, Kingston University, London, United Kingdom
Chris Hand is Professor of Marketing at Kingston Business School. His research focuses on consumer behaviour and applications of quantitative methods to management issues. His research has appeared in journals including the Journal of Business Research, Information Technology & People, Behaviour & Information Technology and Economic and Industrial Democracy.
Abdel-Khalek, A. M. (2019). Religiosity and well-being. In V. Zeigler-Hill & T. K. Shackelford (Eds.), Encyclopedia of personality and individual differences (pp. 4407–4415). Springer. https://doi.org/10.1007/978-3-319-24612-3_2335
Abeyta, A. A., & Blake, E. N. (2020). The existential implications of individual differences in religious defensive and growth orientations: Fundamentalism, quest religiosity, and intrinsic/extrinsic religiosity. In K. E. Vail & C. Routledge (Eds.), The science of religion, spirituality, and existentialism (pp. 351–357). Academic Press. https://doi.org/10.1016/B978-0-12-817204-9.00025-1
Aderibigbe, N. A., & Ocholla, D. N. (2020). Insight into ethical cyber behaviour of undergraduate students at selected African universities. South African Journal of Information Management, 22(1), Article a1131. http://dx.doi.org/10.4102/sajim.v22i1.1131
Ajzen, I., & Fishbein, M. (1980). Understanding attitudes and predicting social behavior. Prentice-Hall. https://www.scienceopen.com/book?vid=c20c4174-d8dc-428d-b352-280b05eacdf7
Allen, J. J., Anderson, C. A., & Bushman, B. J. (2018). The general aggression model. Current Opinion in Psychology, 19, 75–80. https://doi.org/10.1016/j.copsyc.2017.03.034
Allison, K. R., & Bussey, K. (2016). Cyber-bystanding in context: A review of the literature on witnesses’ responses to cyberbullying. Children and Youth Services Review, 65, 183–194. https://doi.org/10.1016/j.childyouth.2016.03.026
Allport, G. W., & Ross, J. M. (1967). Personal religious orientation and prejudice. Journal of Personality and Social Psychology, 5(4), 432–443. https://doi.org/10.1037/h0021212
Álvarez-García, D., Barreiro-Collazo, A., Núñez, J. C., & Dobarro, A. (2016). Validity and reliability of the Cyber-aggression Questionnaire for Adolescents (CYBA). The European Journal of Psychology Applied to Legal Context, 8(2), 69–77. https://doi.org/10.1016/j.ejpal.2016.02.003
Anderson, C. A., & Bushman, B. J. (2002). Human aggression. Annual Review of Psychology, 53(1), 27–51. https://doi.org/10.1146/annurev.psych.53.100901.135231
Anderson, C. A., & Carnagey, N. L. (2004). Violent evil and the general aggression model. The social psychology of good and evil (pp. 168–192). The Guilford Press. https://psycnet.apa.org/record/2004-16379-008
Ang, R. P., Tan, K.-A., & Talib Mansor, A. (2011). Normative beliefs about aggression as a mediator of narcissistic exploitativeness and cyberbullying. Journal of Interpersonal Violence, 26(13), 2619–2634. https://doi.org/10.1177/0886260510388286
Arató, N., Zsido, A. N., Lénárd, K., & Lábadi, B. (2020). Cybervictimization and cyberbullying: The role of socio-emotional skills. Frontiers in Psychiatry, 11, Article 248. https://doi.org/10.3389/fpsyt.2020.00248
Awan, I., & Zempi, I. (2016). The affinity between online and offline anti-Muslim hate crime: Dynamics and impacts. Aggression and Violent Behaviour, 27, 1–8. https://doi.org/10.1016/j.avb.2016.02.001
Bagozzi, R. P., & Yi, Y. (2012). Specification, evaluation, and interpretation of structural equation models. Journal of the Academy of Marketing Science, 40, 8–34. https://doi.org/10.1007/s11747-011-0278-x
Baguley, T., Dunham, G., & Steer, O. (2022). Statistical modelling of vignette data in psychology. British Journal of Psychology, 113(4), 1143–1163. https://doi.org/10.1111/bjop.12577
Bandura, A. (1991). Social cognitive theory of self-regulation. Organizational Behaviour and Human Decision Processes, 50(2), 248–287. https://doi.org/10.1016/0749-5978(91)90022-L
Bandura, A., Ross, D., & Ross, S. A. (1963). Imitation of film-mediated aggressive models. The Journal of Abnormal and Social Psychology, 66(1), 3–11. https://doi.org/10.1037/h0048687
Barlett, C. P. (2019). Predicting cyberbullying: Research, theory, and intervention. Academic Press. https://psycnet.apa.org/record/2019-32176-000
Barlett, C. P. (2023). Cyberbullying as a learned behavior: Theoretical and applied implications. Children, 10(2), Article 325. https://doi.org/10.3390/children10020325
Barlett, C. P., & Gentile, D. A. (2012). Attacking others online: The formation of cyberbullying in late adolescence. Psychology of Popular Media Culture, 1(2), 123–135. https://doi.org/10.1037/a0028113
Barlett, C. P., Gentile, D. A., & Chew, C. (2016). Predicting cyberbullying from anonymity. Psychology of Popular Media Culture, 5(2), 171–180. https://doi.org/10.1037/ppm0000055
Barlett, C. P., Heath, J. B., Madison, C. S., DeWitt, C. C., & Kirkpatrick, S. M. (2020). You’re not anonymous online: The development and validation of a new cyberbullying intervention curriculum. Psychology of Popular Media, 9(2), 135–144. https://doi.org/10.1037/ppm0000226
Bastiaensens, S., Vandebosch, H., Poels, K., Van Cleemput, K., DeSmet, A., & De Bourdeaudhuij, I. (2014). Cyberbullying on social network sites. An experimental study into bystanders’ behavioural intentions to help the victim or reinforce the bully. Computers in Human Behavior, 31, 259–271. https://doi.org/10.1016/j.chb.2013.10.036
Bhargava, S., & Kaura, N. (2020). The effect of religiosity on gratitude and aggression among male and female undergraduate students. The International Journal of Indian Psychology, 8(2), 937–948. https://doi.org/10.25215/0802.111
Bleize, D. N. M., Tanis, M., Anschütz, D. J., & Buijzen, M. (2021). A social identity perspective on conformity to cyber aggression among early adolescents on WhatsApp. Social Development, 34(4), 941–956. https://doi.org/10.1111/sode.12511
Brewer, G., & Kerslake, J. (2015). Cyberbullying, self-esteem, empathy and loneliness. Computers in Human Behaviour, 48, 255–260. https://doi.org/10.1016/j.chb.2015.01.073
Brickman Bhutta, C. (2012). Not by the book: Facebook as a sampling frame. Sociological Methods and Research, 41(1), 57–88. https://doi.org/10.1177/0049124112440795
Bronfenbrenner, U. (1977). Toward an experimental ecology of human development. American Psychologist, 32(7), 513–531. https://doi.org/10.1037/0003-066X.32.7.513.
Bryant, F. B., & Smith, B. D. (2001). Refining the architecture of aggression: A measurement model for the Buss–Perry Aggression Questionnaire. Journal of Research in Personality, 35(2), 138–167. https://doi.org/10.1006/jrpe.2000.2302
Buhrmester, D., & Furman, W. (2008). The Network of Relationships Inventory: Relationship qualities version [Unpublished measure]. University of Texas at Dallas.
Bullo, A., & Schulz, P. J. (2022). Do peer and parental norms influence media content-induced cyber aggression? Computers in Human Behavior, 129, Article 107136. https://doi.org/10.1016/j.chb.2021.107136
Buss, A. H., & Perry, M. (1992). The Aggression Questionnaire. Journal of Personality and Social Psychology, 63(3), 452–459. https://doi.org/10.1037/0022-3514.63.3.452.
Butterfield, K. D., Trevin, L. K., & Weaver, G. R. (2000). Moral awareness in business organizations: Influences of issue-related and social context factors. Human Relations, 53(7), 981–1018. https://doi.org/10.1177/0018726700537004
Calvete, E., Orue, I., Estévez, A., Villardón, L., & Padilla, P. (2010). Cyberbullying in adolescents: Modalities and aggressors’ profile. Computers in Human Behaviour, 26(5), 1128–1135. https://doi.org/10.1016/j.chb.2010.03.017
Cantone, E., Piras, A. P., Vellante, M., Preti, A., Daníelsdóttir, S., D’Aloja, E., Lesinskiene, S., Angermeyer, M. C., Carta, M. G., & Bhugra, D. (2015). Interventions on bullying and cyberbullying in schools: A systematic review. Clinical practice and Epidemiology in Mental Health, 11(Suppl. 1, M4), 58–76. https://doi.org/10.2174/1745017901511010058
Caplan, S. E., & Turner, J. S. (2007). Bringing theory to research on computer-mediated comforting communication. Computers in Human Behaviour, 23(2), 985–998. https://doi.org/10.1016/j.chb.2005.08.003
Cappadocia, M. C., Pepler, D., Cummings, J. G., & Craig, W. (2012). Individual motivations and characteristics associated with bystander intervention during bullying episodes among children and youth. Canadian Journal of School Psychology, 27(3), 201–216. https://doi.org/10.1177/0829573512450567
Caravita, S. C. S., Di Blasio, P., & Salmivalli, C. (2010). Early adolescents’ participation in bullying: Is ToM involved? The Journal of Early Adolescence, 30(1), 138–170. https://doi.org/10.1177/0272431609342983
Card, N. A., Stucky, B. D., Sawalani, G. M., & Little, T. D. (2008). Direct and indirect aggression during childhood and adolescence: A meta-analytic review of gender differences, intercorrelations, and relations to maladjustment. Child Development, 79(5), 1185–1229. https://doi.org/10.1111/j.1467-8624.2008.01184.x
Carré, A., Stefaniak, N., D’Ambrosio, F., Bensalah, L., & Besche-Richard, C. (2013). The Basic Empathy Scale in Adults (BES-A): Factor structure of a revised form. Psychological Assessment, 25(3), 679–691. https://doi.org/10.1037/a0032297
Carrier, L. M., Spradlin, A., Bunce, J. P., & Rosen, L. D. (2015). Virtual empathy: Positive and negative impacts of going online upon empathy in young adults. Computers in Human Behavior, 52, 39–48. https://doi.org/10.1016/j.chb.2015.05.026
Chan, J., Ghose, A., & Seamans, R. (2016). The internet and racial hate crime: Offline spillovers from online access. MIS Quarterly, 40(2), 381–403. https://www.jstor.org/stable/26628911
Chan, T. K. H., Cheung, C. M. K., & Lee, Z. W. Y. (2021). Cyberbullying on social networking sites: A literature review and future research directions. Information & Management, 58(2), Article 103411. https://doi.org/10.1016/j.im.2020.103411
Chan, T. K. H., Cheung, C. M. K., & Wong, R. Y. M. (2019). Cyberbullying on social networking sites: The crime opportunity and affordance perspectives. Journal of Management Information Systems, 36(2), 574–609. https://doi.org/10.1080/07421222.2019.1599500
Chen, L. M., Cheng, W., & Ho, H.-C. (2015). Perceived severity of school bullying in elementary schools based on participants’ roles. Educational Psychology, 35(4), 484–496. https://doi.org/10.1080/01443410.2013.860220
Cheng, Y., Hung, A.-Y., & Decety, J. (2012). Dissociation between affective sharing and emotion understanding in juvenile psychopaths. Development and Psychopathology, 24(2), 623–636. https://doi.org/10.1017/S095457941200020X
Choi, J. Y., Lim, G. G., & Woo, M. N. (2016). A study on the anonymity perceptions impacting on posting malicious messages in online communities. PACIS 2016 Proceedings, Article 266. https://repository.hanyang.ac.kr/handle/20.500.11754/71910
Christopherson, K. M. (2007). The positive and negative implications of anonymity in internet social interactions: “On the internet, nobody knows you’re a dog”. Computers in Human Behavior, 23(6), 3038–3056. https://doi.org/10.1016/j.chb.2006.09.001
Cohen, J. (1988). Statistical power analysis for the behavioral sciences (2nd ed.). Lawrence Erlbaum Associates.
Cohen, D., & Strayer, J. (1996). Empathy in conduct-disordered and comparison youth. Developmental Psychology, 32(6), 988–998. https://doi.org/10.1037/0012-1649.32.6.988
Correa, D., Silva, L. A., Mondal, M., Benevenuto, F., & Gummadi, K. P. (2021). The many shades of anonymity: Characterizing anonymous social media content. Proceedings of the International AAAI Conference on Web and Social Media, 9(1), 71–80. https://doi.org/10.1609/icwsm.v9i1.14635
Cuff, B. M. P., Brown, S. J., Taylor, L., & Howat, D. J. (2016). Empathy: A review of the concept. Emotion Review, 8(2), 144–153. https://doi.org/10.1177/1754073914558466
Dang, J., & Liu, L. (2020). When peer norms work? Coherent groups facilitate normative influences on cyber aggression. Aggressive Behaviour, 559–569. https://doi.org/10.1002/ab.21920
Dempsey, A. G., Sulkowski, M. L., Dempsey, J., & Storch, E. A. (2011). Has cyber technology produced a new group of peer aggressors? Cyberpsychology, Behavior, and Social Networking, 14(5), 297–302. https://doi.org/10.1089/cyber.2010.0108
Densley, J., & Peterson, J. (2018). Group aggression. Current Opinion in Psychology, 19, 43–48. https://doi.org/10.1016/j.copsyc.2017.03.031
DeWall, C. N., Anderson, C. A., & Bushman, B. J. (2011). The general aggression model: Theoretical extensions to violence. Psychology of Violence, 1(3), 245–258. https://doi.org/10.1037/a0023842
DeWall, C. N., Anderson, C. A., & Bushman, B. J. (2012). Aggression. In H. Tennen, J. Suls, & I. B. Weiner (Eds.), Handbook of psychology (2nd ed., pp. 449–466). John Wiley & Sons.
DeWall, C. N., Baumeister, R. F., Stillman, T. F., & Gailliot, M. T. (2007). Violence restrained: Effects of self-regulation and its depletion on aggression. Journal of Experimental Social Psychology, 43(1), 62–76. https://doi.org/10.1016/j.jesp.2005.12.005
DeWall, C. N., & Chester, D. S. (2016). Taming the impulsive beast: Understanding the link between self-regulation and aggression. In R. Hirt, J. J. Clarkson, & L. Jia (Eds.), Self-regulation and ego control (pp. 165–181). Academic Press. https://doi.org/10.1016/B978-0-12-801850-7.00009-3
Diener, E. (1976). Effects of prior destructive behavior, anonymity, and group presence on deindividuation and aggression. Journal of Personality and Social Psychology, 33(5), 497–507. https://doi.org/10.1037/0022-3514.33.5.497
Dilmaç, B. (2009). Psychological needs as a predictor of cyber bullying: A preliminary report on college students. Educational Sciences: Theory and Practice, 9(3), 1307–1325. https://files.eric.ed.gov/fulltext/EJ858926.pdf
Doane, A. N., Pearson, M. R., & Kelley, M. L. (2014). Predictors of cyberbullying perpetration among college students: An application of the theory of reasoned action. Computers in Human Behavior, 36, 154–162. https://doi.org/10.1016/j.chb.2014.03.051
Dooley, J. J., Pyżalski, J., & Cross, D. (2009). Cyberbullying versus face-to-face bullying: A theoretical and conceptual review. Journal of Psychology, 217(4), 182–188. https://doi.org/10.1027/0044-3409.217.4.182
Dredge, R., Gleeson, J. F., & De la Piedad Garcia, X. (2014). Risk factors associated with impact severity of cyberbullying victimization: A qualitative study of adolescent online social networking. Cyberpsychology, Behavior, and Social Networking, 17(5), 287–291. https://doi.org/10.1089/cyber.2013.0541
Duarte, P. A. O., & Raposo, M. L. B. (2010). A PLS model to study brand preference: An application to the mobile phone market. In V. E. Vinzi, W. W. Chin, J. Henseler, & H. Wang (Eds.), Handbook of partial least squares: Concepts, methods and applications (pp. 449–485). Springer. https://doi.org/10.1007/978-3-540-32827-821
Duckworth, A. L., & Kern, M. L. (2011). A meta-analysis of the convergent validity of self-control measures. Journal of Research in Personality, 45(3), 259–268. https://doi.org/10.1016/j.jrp.2011.02.004
Eraslan, L., & Kukuoğlu, A. (2019). Social relations in virtual world and social media aggression. World Journal on Educational Technology: Current Issues, 11(2), 140–149. https://doi.org/10.18844/wjet.v11i2.4145
Evenden, J. L. (1999). Varieties of impulsivity. Psychopharmacology, 146(4), 348–361. https://doi.org/10.1007/PL00005481
Evolvi, G. (2018). Hate in a tweet: Exploring internet-based islamophobic discourses. Religions, 9(10), Article 307. https://doi.org/10.3390/rel9100307
Farrington, D. P., Loeber, R., Stallings, R., & Ttofi, M. M. (2011). Bullying perpetration and victimization as predictors of delinquency and depression in the Pittsburgh Youth Study. Journal Of Aggression, Conflict and Peace Research, 3(2), 74–81. https://doi.org/10.1108/17596591111132882
Ferreira, P. C., Veiga Simão, A. M., Pereira, N. S., Paulino, P., & Oliveira, S. (2020). Online verbal aggression, social relationships, and self-efficacy beliefs. New Media & Society, 23(5), 960–981. https://doi.org/10.1177/146144482090553
Festinger, L., Pepitone, A., & Newcomb, T. (1952). Some consequences of de-individuation in a group. Journal of Abnormal and Social Psychology, 47(2), 382–389. https://doi.org/10.1037/h0057906
Festl, R. (2016). Perpetrators on the internet: Analyzing individual and structural explanation factors of cyberbullying in school context. Computers in Human Behavior, 59, 237–248. https://doi.org/10.1016/j.chb.2016.02.017
Festl, R., Scharkow, M., & Quandt, T. (2015). The individual or the group: A multilevel analysis of cyberbullying in school classes. Human Communication Research, 41(4), 535–556. https://doi.org/10.1111/hcre.12056
Firoozabadi, A. (2020). The past victim, the future abuser. Archives of Iranian Medicine, 23(4), S6–S8. https://doi.org/10.34172/aim.2020.s2
Fishbein, M., & Ajzen, I. (1977). Belief, attitude, intention, and behavior: An introduction to theory and research. Philosophy and Rhetoric, 10(2), 130–132. https://philpapers.org/rec/FISBAI
Fraser, A. M., Padilla-Walker, L. M., Coyne, S. M., Nelson, L. J., & Stockdale, L. A. (2012). Associations between violent video gaming, empathic concern, and prosocial behavior toward strangers, friends, and family members. Journal of Youth and Adolescence, 41(5), 636–649. https://doi.org/10.1007/s10964-012-9742-2
Galen, B. R., & Underwood, M. K. (1997). A developmental investigation of social aggression among children. Developmental Psychology, 33(4), 589–600. https://doi.org/10.1037/0012-1649.33.4.589
Garandeau, C. F., Laninga-Wijnen, L., & Salmivalli, C. (2022). Effects of the KiVa anti-bullying program on affective and cognitive empathy in children and adolescents. Journal of Clinical Child & Adolescent Psychology, 51(4), 515–529. https://doi.org/10.1080/15374416.2020.1846541
Gavish, B., & Gerdes, J. H. (1998). Anonymous mechanisms in group decision support systems communication. Decision Support Systems, 23(4), 297–328. https://doi.org/10.1016/S0167-9236(98)00057-8
Gerhart, N., & Koohikamali, M. (2019). Social network migration and anonymity expectations: What anonymous social network apps offer. Computers in Human Behavior, 95, 101–113. https://doi.org/10.1016/j.chb.2019.01.030
Gilbert, F., & Daffern, M. (2011). Illuminating the relationship between personality disorder and violence: Contributions of the general aggression model. Psychology of Violence, 1(3), 230–244. https://doi.org/10.1037/a0024089
Gini, G. (2007). Who is blameworthy?: Social identity and inter-group bullying. School Psychology International, 28(1), 77–89. https://doi.org/10.1177/014303430707568
Gini, G., Albiero, P., Benelli, B., & Altoè, G. (2007). Does empathy predict adolescents’ bullying and defending behavior? Aggressive Behavior, 33(5), 467–476. https://doi.org/10.1002/ab.20204
Golec de Zavala, A., Cichocka, A., Orehek, E., & Abdollahi, A. (2012). Intrinsic religiosity reduces intergroup hostility under mortality salience. European Journal of Social Psychology, 42(4), 451–461. https://doi.org/10.1002/ejsp.1843
Gorsuch, R. L., & McPherson, S. E. (1989). Intrinsic/Extrinsic Measurement: I/E-Revised and Single-Item Scales. Journal for the Scientific Study of Religion, 28(3). https://doi.org/10.2307/1386745
Göritz, A. S., Singh, R. K., & Voggeser, B. J. (2012). Human behaviour on the WWW. In Z. Yan (Ed.), Encyclopaedia of cyber behaviour (pp. 117–131). IGI Global. https://doi.org/10.4018/978-1-4666-0315-8.ch010
Gottfredson, M. R., & Hirschi, T. (1990). A general theory of crime. Stanford University Press. https://doi.org/10.1515/9781503621794
Grasmick, H. G., Tittle, C. R., Bursik Jr, R. J., & Arneklev, B. J. (1993). Testing the core empirical implications of Gottfredson and Hirschi’s general theory of crime. Journal of Research in Crime and Delinquency, 30(1), 5–29. https://doi.org/10.1177/00224278930300010
Grigg, D. W. (2010). Cyber-aggression: Definition and concept of cyberbullying. Journal of Psychologists and Counsellors in Schools, 20(2), 143–156. https://doi.org/10.1375/ajgc.20.2.143
Grimes, M., & Marquardson, J. (2019). Quality matters: Evoking subjective norms and coping appraisals by system design to increase security intentions. Decision Support Systems, 119, 23–34. https://doi.org/10.1016/j.dss.2019.02.010
Gül, H., Fırat, S., Sertçelik, M., Gül, A., Gürel, Y., & Kılıç, B. G. (2019). Cyberbullying among a clinical adolescent sample in Turkey: Effects of problematic smartphone use, psychiatric symptoms, and emotion regulation difficulties. Psychiatry and Clinical Psychopharmacology, 29(4), 547–557. https://doi.org/10.1080/24750573.2018.1472923
Hair, J. F., Ringle, C. M., & Sarstedt, M. (2011). PLS-SEM: Indeed a silver bullet. Journal of Marketing Theory and Practice, 19(2), 139–151. https://doi.org/10.2753/MTP1069-6679190202
Hardy, S. A., Walker, L. J., Rackham, D. D., & Olsen, J. A. (2012). Religiosity and adolescent empathy and aggression: The mediating role of moral identity. Psychology of Religion and Spirituality, 4(3), 237–248. https://doi.org/10.1037/a0027566
Hawdon, J., & Costello, M. (2020). Learning to hate: Explaining participation in online extremism. In D. M. D Silva & M. Deflem (Eds.), Sociology of crime, law and deviance, Vol. 25: Radicalization and counter-radicalization (pp. 167–182). Emerald Publishing Limited. https://doi.org/10.1108/S1521-613620200000025010
Hayes, N. L., Marsee, M. A., & Russell, D. W. (2020). Latent profile analysis of traditional and cyber-aggression and victimization: Associations with dark triad traits and psychopathology symptoms. Journal of Psychopathology and Behavioral Assessment, 43, 399–412. https://doi.org/10.1007/s10862-020-09835-2
Hayne, S. C., & Rice, R. E. (1997). Attribution accuracy when using anonymity in group support systems. International Journal of Human–Computer Studies, 47(3), 429–452. https://doi.org/10.1006/ijhc.1997.0134
Heirman, W., & Walrave, M. (2012). Predicting adolescent perpetration in cyberbullying: An application of the theory of planned behavior. Psicothema, 24(4), 614–620. https://pubmed.ncbi.nlm.nih.gov/23079360/
Herring, S. C. (1999). The rhetorical dynamics of gender harassment on-line. The Information Society, 15(3), 151–167. https://doi.org/10.1080/019722499128466
Hilvert-Bruce, Z., & Neill, J. T. (2020). I’m just trolling: The role of normative beliefs in aggressive behaviour in online gaming. Computers in Human Behavior, 102, 303–311. https://doi.org/10.1016/j.chb.2019.09.003
Hinduja, S., & Patchin, J. W. (2007). Offline consequences of online victimization: School violence and delinquency. Journal of School Violence, 6(3), 89–112. https://doi.org/10.1300/J202v06n03_06
Hite, D. M., Voelker, T., & Robertson, A. (2014). Measuring perceived anonymity: The development of a context independent instrument. Journal of Methods and Measurement in the Social Sciences, 5(1), 22–39. https://doi.org/10.2458/v5i1.18305
Howard, R. C. (2011). The quest for excitement: A missing link between personality disorder and violence? Journal of Forensic Psychiatry & Psychology, 22(5), 692–705. https://doi.org/10.1080/14789949.2011.617540
Hungerman, D. M. (2014). Do religious proscriptions matter? Evidence from a theory-based test. Journal of Human Resources, 49(4), 1053–1093. https://doi.org/10.3368/jhr.49.4.1053
Joinson, A. N. (2007). Disinhibition and the internet. In J. Cackenbach (Ed.), Psychology and the internet (pp. 75–92). Academic Press. https://doi.org/10.1016/B978-012369425-6/50023-0
Jolliffe, D., & Farrington, D. P. (2006). Examining the relationship between low empathy and bullying. Aggressive Behavior, 32(6), 540–550. https://doi.org/10.1002/ab.20154
Jolliffe, D., & Farrington, D. P. (2011). Is low empathy related to bullying after controlling for individual and social background variables? Journal of Adolescence, 34(1), 59–71. https://doi.org/10.1016/j.adolescence.2010.02.001
Kapp, J. M., Peters, C., & Oliver, D. P. (2013). Research recruitment using Facebook advertising: Big potential, big challenges. Journal of Cancer Education, 28, 134–137. https://doi.org/10.1007/s13187-012-0443-z
Kaur, P., Dhir, A., Tandon, A., Alzeiby, E. A., & Abohassan, A. A. (2020). A systematic literature review on cyberstalking. An analysis of past achievements and future promises. Technological Forecasting and Social Change, 163, Article 120426. https://doi.org/10.1016/j.techfore.2020.120426
Kim, H. M., Bock, G. W., & Kim, H. S. (2020). A new perspective on online malicious comments: Effects of attention and neutralization. Information Technology & People, 34(1), 50–67. https://doi.org/10.1108/ITP-04-2019-0179
Kintonova, A., Vasyaev, A., & Shestak, V. (2021). Cyberbullying and cyber-mobbing in developing countries. Information & Computer Security, 29(3), 435–456. https://doi.org/10.1108/ICS-02-2020-0031
Kokkinos, C. M., & Voulgaridou, I. (2017). Relational and cyber aggression among adolescents: Personality and emotion regulation as moderators. Computers in Human Behavior, 68, 528–537. https://doi.org/10.1016/j.chb.2016.11.046
Kumari, K., Singh, J. P., Dwivedi, Y. K., & Rana, N. P. (2019). Aggressive social media post detection system containing symbolic images. In I. O. Pappas, P. Mikalef, Y. K. Dwivedi, L. Jaccheri, J. Krogstie, & M. Mäntymäki (Eds.), Digital transformation for a sustainable society in the 21st century (pp. 415–424). Springer. https://doi.org/10.1007/978-3-030-29374-1_34
Kwan, G. C. E., & Skoric, M. M. (2013). Facebook bullying: An extension of battles in school. Computers in Human Behavior, 29(1), 16–25. https://doi.org/10.1016/j.chb.2012.07.014
Lee, S.-G., Kang, M., & Kang, H.-S. (2013). Mechanisms underlying aggravation and relaxation of virtual aggression: A Second Life survey study. Behaviour & Information Technology, 32(7), 735–746. https://doi.org/10.1080/0144929X.2013.801079
Lemercier-Dugarin, M., Romo, L., Tijus, C., & Zerhouni, O. (2021). Who are the Cyka Blyat? How empathy, impulsivity, and motivations to play predict aggressive behaviors in multiplayer online games. Cyberpsychology, Behavior, and Social Networking, 24(1), 63–69. https://doi.org/10.1089/cyber.2020.0041
Leone, R. M., & Parrott, D. J. (2019). Misogynistic peers, masculinity, and bystander intervention for sexual aggression: Is it really just “locker‐room talk?”. Aggressive Behaviour, 45(1), 42–51. https://doi.org/10.1002/ab.21795
Lewis, T. T., Cogburn, C. D., & Williams, D. R. (2015). Self-reported experiences of discrimination and health: Scientific advances, ongoing controversies, and emerging issues. Annual Review of Clinical Psychology, 11, 407–440. https://doi.org/10.1146/annurev-clinpsy-032814-112728
Li, Q. (2007). New bottle but old wine: A research of cyberbullying in schools. Computers in Human Behavior, 23(4), 1777–1791. https://doi.org/10.1016/j.chb.2005.10.005
Li, S., & Nie, Y. (2023). Spirituality and cyberaggression: Mediating and moderating effect of self-control and school climate. International Journal of Environmental Research and Public Health, 20(4), Article 2973. https://doi.org/10.3390/ijerph20042973
Lowry, P. B., Zhang, J., Wang, C., & Siponen, M. (2016). Why do adults engage in cyberbullying on social media? An integration of online disinhibition and deindividuation effects with the social structure and social learning model. Information Systems Research, 27(4), 962–986. https://doi.org/10.1287/isre.2016.0671
Lu, J. G., Martin, A. E., Usova, A., & Galinsky, A. D. (2019). Creativity and humor across cultures: Where aha meets haha. In S. R. Luria, J. Baer, & J. C. Kaufman (Eds.), Creativity and humor (pp. 183–203). Academic Press. https://doi.org/10.1016/B978-0-12-813802-1.00009-0
Lumsden, K. (2019). ‘“I want to kill you in front of your children’ is not a threat. It’s an expression of a desire”: Discourses of online abuse, trolling and violence on r/MensRights. In K. Lumsden & E. Harmer (Eds.), Online othering (pp. 91–115). Palgrave Macmillan. https://doi.org/10.1007/978-3-030-12633-9_4
Macaulay, P. J., Boulton, M. J., & Betts, L. R. (2019). Comparing early adolescents’ positive bystander responses to cyberbullying and traditional bullying: The impact of severity and gender. Journal of Technology in Behavioral Science, 4(3), 253–261. https://doi.org/10.1007/s41347-018-0082-2
Marín-López, I., Zych, I., Ortega-Ruiz, R., Monks, C. P., & Llorent, V. J. (2020). Empathy online and moral disengagement through technology as longitudinal predictors of cyberbullying victimization and perpetration. Children and Youth Services Review, 116, Article 105144. https://doi.org/10.1016/j.childyouth.2020.105144
Marx, G. T. (1999). What’s in a name? Some reflections on the sociology of anonymity. The Information Society, 15(2), 99–112. https://doi.org/10.1080/019722499128565
Mayberry, M. L., & Espelage, D. L. (2007). Associations among empathy, social competence, & reactive/proactive aggression subtypes. Journal of Youth and Adolescence, 36(6), 787–798. https://doi.org/10.1007/s10964-006-9113-y
McCullough, M. E., & Willoughby, B. L. B. (2009). Religion, self-regulation, and self-control: Associations, explanations, and implications. Psychological Bulletin, 135(1), 69–93. https://doi.org/10.1037/a0014213
Mellor, J. M., & Freeborn, B. A. (2011). Religious participation and risky health behaviors among adolescents. Health Economics, 20(10), 1226–1240. https://doi.org/10.1002/hec.1666
Mendolia, S., Paloyo, A., & Walker, I. (2019). Intrinsic religiosity, personality traits, and adolescent risky behaviors. The BE Journal of Economic Analysis & Policy, 19(3), Article 20180311. https://doi.org/10.1515/bejeap-2018-0311
Millie, A. (2008). Anti-social behaviour, behavioural expectations and an urban aesthetic. The British Journal of Criminology, 48(3), 379–394. https://doi.org/10.1093/bjc/azm076
Mishna, F., Saini, M., & Solomon, S. (2009). Ongoing and online: Children and youth’s perceptions of cyber bullying. Children and Youth Services Review, 31(12), 1222–1228. https://doi.org/10.1016/j.childyouth.2009.05.004
Modha, S., Majumder, P., & Mandl, T. (2018). Filtering aggression from the multilingual social media feed. In R. Kumar, A. K. Ojha, M. Zampieri, & S. Malmasi (Eds.), Proceedings of the first workshop on trolling, aggression and cyberbullying (TRAC-2018) (pp. 199–207). Association for Computational Linguistics. https://aclanthology.org/W18-4423
Modha, S., Majumder, P., Mandl, T., & Mandalia, C. (2020). Detecting and visualizing hate speech in social media: A cyber watchdog for surveillance. Expert Systems with Applications, 161, Article 113725. https://doi.org/10.1016/j.eswa.2020.113725
Mosqueiro, B. P., da Rocha, N. S., & de Almeida Fleck, M. P. (2015). Intrinsic religiosity, resilience, quality of life, and suicide risk in depressed inpatients. Journal of Affective Disorders, 179, 128–133. https://doi.org/10.1016/j.jad.2015.03.022
Nakano, T., Suda, T., Okaie, Y., & Moore, M. J. (2016). Analysis of cyber aggression and cyber-bullying in social networking. In 2016 IEEE tenth international conference on semantic computing (ICSC) (pp. 337–334). IEEE. https://doi.org/10.1109/ICSC.2016.111
Obermaier, M., Fawzi, N., & Koch, T. (2016). Bystanding or standing by? How the number of bystanders affects the intention to intervene in cyberbullying. New Media & Society, 18(8), 1491–1507. https://doi.org/10.1177/1461444814563519
Pabian, S., De Backer, C. J., & Vandebosch, H. (2015). Dark triad personality traits and adolescent cyber-aggression. Personality and Individual Differences, 75, 41–46. https://doi.org/10.1016/j.paid.2014.11.015
Parvaresh, V., & Tayebi, T. (2018). Impoliteness, aggression and the moral order. Journal of Pragmatics, 132, 91–107. https://doi.org/10.1016/j.pragma.2018.05.010
Peker, A., & Yildiz, M. N. (2021). Mediating role of self-control in the relationship between aggressiveness and cyber bullying. Psychiatry and Behavioral Sciences, 11(1), 40–49. https://doi.org/10.5455/PBS.20210114051215
Perfumi, S. C. (2020). Social identity model of deindividuation effects and media use. In The international encyclopedia of media psychology (pp. 1–8). John Wiley & Sons. https://doi.org/10.1002/9781119011071.iemp0151
Petrović, Z. K., Peraica, T., Kozarić-Kovačić, D., & Palavra, I. R. (2022). Internet use and internet-based addictive behaviours during coronavirus pandemic. Current Opinion in Psychiatry, 35(5), 324–331. https://doi.org/10.1097/YCO.0000000000000804
Piazza, J., & Bering, J. M. (2008). The effects of perceived anonymity on altruistic punishment. Evolutionary Psychology, 6(3). https://doi.org/10.1177/147470490800600314
Piccoli, V., Carnaghi, A., Grassi, M., Stragà, M., & Bianchi, M. (2020). Cyberbullying through the lens of social influence: Predicting cyberbullying perpetration from perceived peer-norm, cyberspace regulations and ingroup processes. Computers in Human Behaviour, 102, 260–273. https://doi.org/10.1016/j.chb.2019.09.001
Pirutinsky, S., Rosmarin, D. H., Holt, C. L., Feldman, R. H., Caplan, L. S., Midlarsky, E., & Pargament, K. I. (2011). Does social support mediate the moderating effect of intrinsic religiosity on the relationship between physical health and depressive symptoms among Jews? Journal of Behavioral Medicine, 34(6), 489–496. https://doi.org/10.1007/s10865-011-9325-9
Ray, A., & Kaushik, A. (2017). State transgression on electronic expression: Is it for real? Information & Computer Security, 25(4), 382–401. https://doi.org/10.1108/ICS-03-2016-0024
Reinartz, W. J., Haenlein, M., & Henseler, J. (2009). An empirical comparison of the efficacy of covariance-based and variance-based SEM. International Journal of Market Research, 26(4), 332–344. https://doi.org/10.1016/j.ijresmar.2009.08.001
Reisig, M. D., Wolfe, S. E., & Pratt, T. C. (2012). Low self-control and the religiosity-crime relationship. Criminal Justice and Behavior, 39(9), 1172–1191. https://doi.org/10.1177/0093854812442916
Rejón-Guardia, F., Polo-Peña, A. I., & Maraver-Tarifa, G. (2020). The acceptance of a personal learning environment based on Google apps: The role of subjective norms and social image. Journal of Computing in Higher Education, 32(2), 203–233. https://doi.org/10.1007/s12528-019-09206-1
Richetin, J., Richardson, D. S., & Boykin, D. M. (2011). Role of prevolitional processes in aggressive behavior: The indirect influence of goal. Aggressive Behavior, 37(1), 36–47. https://doi.org/10.1002/ab.20364
Ringle, C. M., & Sarstedt, M. (2016). Gain more insight from your PLS-SEM results: The importance-performance map analysis. Industrial Management & Data Systems, 116(9), 1865–1886. https://doi.org/10.1108/IMDS-10-2015-0449
Rivers, I., & Noret, N. (2010). ‘I h8 u’: Findings from a five‐year study of text and email bullying. British Educational Research Journal, 36(4), 643–671. https://doi.org/10.1080/01411920903071918
Rogers, R. W., & Prentice-Dunn, S. (1981). Deindividuation and anger-mediated interracial aggression: Unmasking regressive racism. Journal of Personality and Social Psychology, 41(1), 63–73. https://doi.org/10.1037/0022-3514.41.1.63
Roman, A., Rad, D., Egerau, A., Dixon, D., Dughi, T., Kelemen, G., Balas, E., & Rad, G. (2020). Physical self-schema acceptance and perceived severity of online aggressiveness in cyberbullying incidents. Journal of Interdisciplinary Studies in Education, 9(1), 100–116. https://doi.org/10.32674/jise.v9i1.1961
Rösner, L., & Krämer, N. C. (2016). Verbal venting in the social web: Effects of anonymity and group norms on aggressive language use in online comments. Social Media + Society, 2(3), 1–13. https://doi.org/10.1177/2056305116664220
Rudnicki, K., Ouvrein, G., De Backer, C., & Heidi, V. (2020). Intranasal oxytocin administration reduces bystanders’ acceptance of online celebrity bashing. International Journal of Bullying Prevention, 2(1), 29–40. https://doi.org/10.1007/s42380-019-00054-2
Runions, K. C. (2013). Toward a conceptual model of motive and self-control in cyber-aggression: Rage, revenge, reward, and recreation. Journal of Youth and Adolescence, 42(5), 751–771. https://doi.org/10.1007/s10964-013-9936-2
Saridakis, G., Benson, V., Ezingeard, J. N., & Tennakoon, H. (2016). Individual information security, user behaviour and cyber victimisation: An empirical study of social networking users. Technological Forecasting and Social Change, 102, 320–330. https://doi.org/10.1016/j.techfore.2015.08.012
Sasson, H., & Mesch, G. (2014). Parental mediation, peer norms and risky online behavior among adolescents. Computers in Human Behavior, 33, 32–38. https://doi.org/10.1016/j.chb.2013.12.025
Scollon, C. N., Kim-Prieto, C., Diener, E. (2003). Experience sampling: Promises and pitfalls, strengths and weaknesses. Journal of Happiness Studies, 4, 5–34. https://doi.org/10.1023/A:1023605205115
Scott, C. R. (1998). Reveal or not to reveal: A theoretical model of anonymous communication. Communication Theory, 8, 381–407. https://doi.org/10.1111/j.1468-2885.1998.tb00226.x
Scott, G. G., Brodie, Z. P., Wilson, M. J., Ivory, L., Hand, C. J., & Sereno, S. C. (2020). Celebrity abuse on Twitter: The impact of tweet valence, volume of abuse, and dark triad personality factors on victim blaming and perceptions of severity. Computers in Human Behavior, 103, 109–119. https://doi.org/10.1016/j.chb.2019.09.020
Sessions, L. F. (2010). How offline gatherings affect online communities: When virtual community members ‘meetup’. Information, Communication & Society, 13(3), 375–395. https://doi.org/10.1080/13691180903468954
Setijanto, R. D., Bramantoro, T., Palupi, R., & Hanani, A. (2019). The role of attitude, subjective norm, and perceived behavioral control (PBC) of mothers on teaching toothbrushing to preschool children–based on the theory of planned behavior: A cross-sectional study. Family Medicine & Primary Care, 21(1), 53–57. https://doi.org/10.5114/fmpcr.2019.82974
Sigfusdottir, I. D., Gudjonsson, G. H., & Sigurdsson, J. F. (2010). Bullying and delinquency. The mediating role of anger. Personality and Individual Differences, 48(4), 391–396. https://doi.org/10.1016/j.paid.2009.10.034
Smith, P. K., Mahdavi, J., Carvalho, M., Fisher, S., Russell, S., & Tippett, N. (2008). Cyberbullying: Its nature and impact in secondary school pupils. Journal of Child Psychology and Psychiatry, 49(4), 376–385. https://doi.org/10.1111/j.1469-7610.2007.01846.x
Smith, T. W. (2013). Survey-research paradigms old and new. International Journal of Public Opinion Research, 25(2), 218–229. https://doi.org/10.1093/ijpor/eds040
Sosik, J. J., Kahai, S. S., & Piovoso, M. J. (2009). Silver bullet or voodoo statistics?: A primer for using the partial least squares data analytic technique in group and organization research. Group and Organization Management, 34(1), 5–36. https://doi.org/10.1177/1059601108329198
Stavrinides, P., Georgiou, S., & Theofanous, V. (2010). Bullying and empathy: A short-term longitudinal investigation. Educational Psychology, 30(7), 793–802. https://doi.org/10.1080/01443410.2010.506004
Steffgen, G., König, A., Pfetsch, J., & Melzer, A. (2011). Are cyberbullies less empathic? Adolescents’ cyberbullying behavior and empathic responsiveness. Cyberpsychology, Behavior, and Social Networking, 14(11), 643–648. https://doi.org/10.1089/cyber.2010.0445
Stutzman, F., & Hartzog, W. (2012). Boundary regulation in social media. Proceedings of the ACM 2012 conference on Computer Supported Cooperative Work - CSCW ‘12, 769–778. https://doi.org/10.1145/2145204.2145320
Sugarman, D. B., & Willoughby, T. (2013). Technology and violence: Conceptual issues raised by the rapidly changing social environment. Psychology of Violence, 3(1), 1–8. https://doi.org/10.1037/a0031010
Suler, J. (2004). The online disinhibition effect. Cyberpsychology and Behavior, 7(3), 321–326. https://doi.org/10.1089/1094931041291295
Sutton, J., Smith, P. K., & Swettenham, J. (1999). Social cognition and bullying: Social inadequacy or skilled manipulation? British Journal of Developmental Psychology, 17(3), 435–450. https://doi.org/10.1348/026151099165384
Suzor, N., Dragiewicz, M., Harris, B., Gillett, R., Burgess, J., & Van Geelen, T. (2019). Human rights by design: The responsibilities of social media platforms to address gender‐based violence online. Policy & Internet, 11(1), 84–103. https://doi.org/10.1002/poi3.185
Swearer, S. M., & Espelage, D. L. (2004). Introduction: A social-ecological framework of bullying among youth. In D. L. Espelage & S. M. Swearer (Eds.), Bullying in American schools: A social-ecological perspective on prevention and intervention (pp. 1–12). Lawrence Erlbaum Associates Publishers. https://psycnet.apa.org/record/2004-00070-001
Tajfel, H., Billig, M. G., Bundy, R. P., & Flament, C. (1971). Social categorization and intergroup behaviour. European Journal of Social Psychology, 1(2), 149–178. https://doi.org/10.1002/ejsp.2420010202
Tanis, M., & Postmes, T. (2007). Two faces of anonymity: Paradoxical effects of cues to identity in CMC. Computers in Human Behavior, 23(2), 955–970. https://doi.org/10.1016/j.chb.2005.08.004
Tenenhaus, M., Esposito Vinzi, V., Chatelin, Y-M., & Lauro, C. (2005). PLS path modelling. Computational Statistics and Data Analysis, 48(1), 159–205. https://doi.org/10.1016/j.csda.2004.03.005
Tesler, R., Nissanholtz-Gannot, R., Zigdon, A., & Harel-Fisch, Y. (2019). The association of cyber-bullying and adolescents in religious and secular schools in Israel. Journal of Religion and Health, 58(6), 2095–2109. https://doi.org/10.1007/s10943-019-00938-z
Theriault, J. E., Young, L., & Barrett, L. F. (2021). The sense of should: A biologically-based framework for modeling social pressure. Physics of Life Reviews, 36, 100–136. https://doi.org/10.1016/j.plrev.2020.01.004
Udupa, S., & Pohjonen, M. (2019). Extreme speech| Extreme speech and global digital cultures—Introduction. International Journal of Communication, 13, 3049–3067. https://ijoc.org/index.php/ijoc/article/view/9102
Uysal, A., & Okumuş, A. (2019). Impact of religiosity on ethical judgement: A study on preference of retail stores among consumers. Journal of Islamic Marketing, 10(4), 1332–1350. https://doi.org/10.1108/JIMA-07-2018-0131
Valentine, S. R., & Bateman, C. R. (2011). The impact of ethical ideologies, moral intensity, and social context on sales-based ethical reasoning. Journal of Business Ethics, 102(1), 155–168. https://doi.org/10.1007/s10551-011-0807-z
Van Noorden, T. H. J., Cillessen, A. H. N., Haselager, G. J. T., Lansu., T. A. M., & Bukowski, W. M. (2017). Bullying involvement and empathy: Child and target characteristics. Social Development, 26(2), 248–262. https://doi.org/10.1111/sode.12197
Vandebosch, H., & Van Cleemput, K. (2009). Cyberbullying among youngsters: Profiles of bullies and victims. New Media & Society, 11(8), 1349–1371. https://doi.org/10.1177/1461444809341263
Vazsonyi, A. T., Machackova, H., Sevcikova, A., Smahel, D., & Cerna, A. (2012). Cyberbullying in context: Direct and indirect effects by low self-control across 25 European countries. European Journal of Developmental Psychology, 9(2), 210–227. https://doi.org/10.1080/17405629.2011.644919
Venkatesh, V., & Bala, H. (2008). Technology acceptance model 3 and a research agenda on interventions. Decision Sciences, 39(2), 273–315. https://doi.org/10.1111/j.1540-5915.2008.00192.x
Venkatesh, V., & Davis, F. D. (2000). A theoretical extension of the technology acceptance model: Four longitudinal field studies. Management Science, 46(2), 186–204. https://doi.org/10.1287/mnsc.46.2.186.11926
Vohs, K. D., & Baumeister, R. F. (2004). Understanding self-regulation: An introduction. In Handbook of self-regulation: Research, theory, and applications (pp. 1–9). The Guilford Press.
Vranjes, I., Baillien, E., Erreygers, S., Vandebosch, H., & De Witte, H. (2020). You wouldn’t like me when I’m angry: A daily diary study of displaced online aggression in dual‐earner couples. Applied Psychology, 70(4), 1463–1491. https://doi.org/10.1111/apps.12283
Wachs, S., & Wright, M. F. (2018). Associations between bystanders and perpetrators of online hate: The moderating role of toxic online disinhibition. International Journal of Environmental Research and Public Health, 15(9), Article 2030. https://doi.org/10.3390/ijerph15092030
Wallace, K. A. (1999). Anonymity. Ethics and Information Technology, 1(1), 21–31. https://doi.org/10.1023/A:1010066509278
Walters, G. D., & Espelage, D. L. (2018). From victim to victimizer: Hostility, anger, and depression as mediators of the bullying victimization–bullying perpetration association. Journal of School Psychology, 68, 73–83. https://doi.org/10.1016/j.jsp.2017.12.003
Wang, C. W., Musumari, P. M., Techasrivichien, T., Suguimoto, S. P., Chan, C. C., Ono-Kihara, M., Kihara, M., & Nakayama, T. (2019). ‘I felt angry, but I couldn’t do anything about it’: A qualitative study of cyberbullying among Taiwanese high school students. BMC Public Health, 19(1), Article 654. https://doi.org/10.1186/s12889-019-7005-9
White, J. L., Moffitt, T. E., Caspi, A., Bartusch, D. J., Needles, D. J., & Stouthamer-Loeber, M. (1994). Measuring impulsivity and examining its relationship to delinquency. Journal of Abnormal Psychology, 103(2), 192–205. https://doi.org/10.1037/0021-843X.103.2.192
Whiteside, S. P., Lynam, D. R., Miller, J. D., & Reynolds, S. K. (2005). Validation of the UPPS Impulsive Behaviour Scale: A four‐factor model of impulsivity. European Journal of Personality, 19(7), 559–574. https://doi.org/10.1002/per.556
Willard, N. E. (2007). Cyberbullying and cyberthreats: Responding to the challenge of online social aggression, threats, and distress. Research Press. https://psycnet.apa.org/record/2007-02981-000
Williams, K. R., & Mattson, S. A. (2006). Qualitative lessons from a community‐based violence prevention project with null findings. New Directions for Evaluation, 2006(110), 5-17. https://doi.org/10.1002/ev.183
Williams, K. R., & Guerra, N. G. (2007). Prevalence and predictors of internet bullying. Journal of Adolescent Health, 41(6), S14–S21. https://doi.org/10.1016/j.jadohealth.2007.08.018
Williams, M. L., & Pearson, O. (2016). Hate crime and bullying in the age of social media. https://orca.cardiff.ac.uk/id/eprint/88865/1/Cyber-Hate-and-Bullying-Post-Conference-Report_English_pdf.pdf
Wright, M. F. (2013). The relationship between young adults’ beliefs about anonymity and subsequent cyber aggression. Cyberpsychology, Behavior, and Social Networking, 16(12), 858–862. https://doi.org/10.1089/cyber.2013.0009
Wright, M. F. (2014a). Cyber victimization and perceived stress. Youth & Society, 47(6), 789–810. https://doi.org/10.1177/0044118X14537088
Wright, M. F. (2014b). Predictors of anonymous cyber aggression: The role of adolescents’ beliefs about anonymity, aggression, and the permanency of digital content. Cyberpsychology, Behavior, and Social Networking, 17(7), 431–438. https://doi.org/10.1089/cyber.2013.0457
Wright, M. F., Wachs, S., & Harper, B. D. (2018). The moderation of empathy in the longitudinal association between witnessing cyberbullying, depression, and anxiety. Cyberpsychology: Journal of Psychosocial Research on Cyberspace, 12(4), Article 6. https://doi.org/10.25932/publishup-47050
Xu, B., Xu, Z., & Li, D. (2016). Internet aggression in online communities: A contemporary deterrence perspective. Information Systems Journal, 26(6), 641–667. https://doi.org/10.1111/isj.12077
Ybarra, M. L., & Mitchell, K. J. (2004). Online aggressor/targets, aggressors, and targets: A comparison of associated youth characteristics. Journal of Child Psychology and Psychiatry, 45(7), 1308–1316. https://doi.org/10.1111/j.1469-7610.2004.00328.x
Ybarra, M. L., Mitchell, K. J., Wolak, J., & Finkelhor, D. (2006). Examining characteristics and associated distress related to internet harassment: Findings from the Second Youth Internet Safety Survey. Pediatrics, 118(4), e1169-e1177. https://doi.org/10.1542/peds.2006-0815
Zhong, L. R., Kebbell, M. R., & Webster, J. L. (2020). An exploratory study of technology-facilitated sexual violence in online romantic interactions: Can the internet’s toxic disinhibition exacerbate sexual aggression? Computers in Human Behavior, 108, Article 106314. https://doi.org/10.1016/j.chb.2020.106314
Zhu, X. W., Chu, X. W., Zhang, Y. H., & Li, Z. H. (2020). Exposure to online game violence and cyberbullying among Chinese adolescents: Normative beliefs about aggression as a mediator and trait aggressiveness as a moderator. Journal of Aggression, Maltreatment & Trauma, 29(2), 148–166. https://doi.org/10.1080/10926771.2018.1550830
Zimbardo, P. G. (1969). The human choice: Individuation, reason, and order versus deindividuation, impulse, and chaos. Nebraska Symposium on Motivation, 17, 237–307. https://psycnet.apa.org/record/1971-08069-001
Zych, I., Ttofi, M. M., & Farrington, D. P. (2019). Empathy and callous–unemotional traits in different bullying roles: A systematic review and meta-analysis. Trauma, Violence and Abuse, 20(1), 3–21. https://doi.org/10.1177/1524838016683456
Authors’ Contribution
Hemamali Tennakoon: conceptualization, investigation, data curation, methodology, formal analysis, writing—original draft, writing—review & editing. Lucy Betts: conceptualization, investigation, writing—original draft, writing—review & editing. George Saridakis: methodology, formal analysis, writing—original draft, writing—review & editing. Chris Hand: methodology, formal analysis, writing – original draft, writing—review & editing. Anil Chandrakumara: conceptualization, writing—original draft, writing—review & editing.
Editorial Record
First submission received:
May 6, 2023
Revisions received:
January 8, 2024
March 29, 2024
Accepted for publication:
May 2, 2024
Editor in charge:
Fabio Sticca
Introduction
The boundary between online and offline social spaces is blurring and offline behaviours are migrating to the online sphere (Ray & Kaushik, 2017). However, there is no regulation or gatekeeping in terms of which behaviours are acceptable and which are not (Awan & Zempi, 2016; J. Chan et al., 2016; Evolvi, 2018; Sessions, 2010; Sugarman & Willoughby, 2013; Udupa & Pohjonen, 2019). The concept of “online violence” has been studied in relation to general web users (Kaur et al., 2020; Kokkinos & Voulgaridou, 2017; Saridakis et al., 2016; Suzor et al., 2019; Zhong et al., 2020; Zhu et al., 2020). There is however room for further research around the concept of “cyber aggression”, particularly in the context of Social Networking Sites (SNS).
From extant literature, it emerges that “cyber aggression” is a broad term and comprises a wide range of antisocial online behaviours that include “bullying, harassment, stalking, abuse, assault or hostility, as well as violent behaviours such as ‘happy slapping, ‘outing’ and ‘flaming’” (Grigg, 2010, p. 152). Aggressive behaviour is likely the observable outcome of a trigger that leads to such behaviours. In support of this argument, DeWall and Chester (2016) posited that there is a distinction between an aggressive urge and aggressive action. There is the practical difficulty of measuring acts of aggression in real-time. Taking this into account, we base our definition on that suggested by Grigg (2010, p. 143) where Cyber Aggression Inclination (CAI) is defined as “intended harm and the use of technological devices” to act aggressively towards another individual in cyberspace.
This paper empirically examines the potential association between personal and situational factors as triggers of aggressive behaviour and cyber aggression inclination drawing on a number of theories. The General Theory of Crime (Gottfredson & Hirschi, 1990), for example, suggests that individual factors, such as self-control, are directly linked to criminal acts. The General Aggression Model (GAM; Anderson & Bushman, 2002) extends this view to include individual differences and situational factors that could affect the level of self-control. The later theory identifies personal factors such as attitudes (positive attitudes toward aggression), normative acceptance of aggression (norms), low self-control, and situational factors (e.g., anonymity) that are likely to influence aggressive behaviours (Anderson & Carnagey, 2004; DeWall et al., 2007, 2012; Gilbert & Daffern, 2011). Furthermore, Social Learning Theory suggests that individuals can mimic others’ aggressive behaviour through interpersonal observations and thus can internalise such behaviours (Bandura et al., 1963). Social Ecology Theory (Bronfenbrenner, 1977) further identifies personal and situational factors, supporting the argument that personal variables such as demographic traits (age, gender), past history (traditional bullying involvement), personality attributes (empathy, self-control), and external factors, such as peers, parents, mass media, cultural beliefs, etc., can lead to the perpetration of cyberbullying (Barlett, 2019).
Drawing on the theories outlined above and various recent studies (Dempsey et al., 2011; Heirman & Walrave, 2012; Lumsden, 2019; M. L. Williams & Pearson, 2016; Wright et al., 2018) we conclude that a two-dimensional approach that studies personal and situational factors as influencers of cyber aggression is appropriate. Particularly, we hypothesise associations between cyber aggression inclination and four personal factors: Higher virtual empathy towards individuals; Low self-control; Prior cyber-aggression victimisation; and Negative normative beliefs about cyber aggression (subjective norms) and four situational factors: Social pressure; Intrinsic religiosity; Perception of anonymity; and perceived incident severity. The expected associations between cyber aggression and these factors are discussed in the next section where the foundations for the hypotheses are developed.
The contribution of this paper is to extend the existing literature, which mainly focuses on online violence towards general web users, by turning the research lens towards factors affecting cyber aggression inclination in online social media settings. This research develops and tests a theoretical model on cyber aggression inclination. The findings of this study will inform key stakeholders and practitioners (individual users, social media firms, government, law enforcement, and industry-based bodies) on the development of prevention and intervention procedures aimed at reducing cyber aggression impulses.
Hypotheses Development
Cyber aggression is an umbrella term that encompasses numerous types of negative behaviours online. These include activities such as flaming, online harassment, denigration, impersonation, outing and trickery, exclusion, cyber stalking, cyber threats, cyber bullying, etc. (Willard, 2007). In the context of SNS, the term cyber bullying has been used to refer to repeated aggressive behaviors on SNSs against targets who cannot defend themselves easily. (T. K. H. Chan et al., 2019, 2021). In this paper, we use the term “cyber-aggression” and adopt Grigg’s (2010, p. 152) definition as “intentional harm delivered by the use of electronic means to a person or a group of people irrespective of their age, who perceive(s) such acts as offensive, derogatory, harmful or unwanted”. There are many types of aggressive behaviours; they can be verbal, physical, and indirect (Card et al., 2008) and the nature of the aggressive behaviour depends on the intention of the aggressor (Galen et al., 1997). The level of aggression and the way in which aggression is shown can be context-specific.
Nevertheless, from a practical standpoint, it is challenging to measure participants’ levels of social aggression. Eraslan and Kukuoglu (2019, p. 4) state that there is “no definite scientific definition for the concept of aggression. Not to mention the fact that the intention of an individual can be estimated but not exactly known”. Álvarez-García et al. (2016) also contend that acts of cyber aggression occur in virtual and often private environments, making them difficult to observe or measure. When respondents are asked if they behave aggressively, their self-reported responses may be biased and not always accurate. Therefore, in this research, we have focused on the propensity of a person to act aggressively, as measured by the variable Cyber Aggressive Inclination (CAI). We identify two broad groups of predictors of CAI: personal factors and situational factors and identify four predictors in each: Virtual Empathy, Low Self Control, Subjective Norms and Prior Cyber Aggression Victimisation under personal factors and Social / Peer Pressure, Intrinsic Religiosity, Perceived Anonymity and Perceived Incident Severity under situational factors. These are introduced and developed below.
In previous studies, the below discussed factors have been researched independently but not collectively. Also, the associations tested in prior studies do not focus specifically on CAI, but on variations of aggressive and antisocial behaviours such as cyber bullying.
Virtual Empathy and CAI
According to Cuff et al. (2016), the term empathy is “not a well-defined notion” but can be understood as behaviour that involves comforting others (Caplan & Turner, 2007). Being empathetic means to be able to understand another person’s emotional state (Cohen & Strayer, 1996). Previous studies have identified two types of empathy i.e., “affective empathy” (Van Noorden et al., 2017; Zych et al., 2019) and cognitive empathy (Caravita et al., 2010; Sutton et al., 1999). However, Garandeau et al. (2022, p. 515) argue that “findings on cognitive empathy…are less consistent”. Further, Gini et al. (2007), Jolliffe & Farrington (2006, 2011), Stavrinides et al. (2010) and Cheng et al. (2012) found no significant link between aggressive acts such as cyber-bullying and cognitive empathy. Therefore, we have used a more context-specific definition of empathy, namely “virtual empathy” (Carrier et al., 2015), defined as understanding others’ emotions and sharing the emotional state of another person in computer-mediated communication or electronic communication environments, such as social media (Arató et al., 2020; Rudnicki et al., 2020).
Existing studies have used Social Ecology Theory to examine the association between (lack of) empathy and aggression. For instance, Steffgen et al. (2011) studied the relationship between an empathic responsiveness and cyberbullying behaviour in adolescents. They find a negative association between the two variables in that cyberbullies are found to have less empathy towards others who are being victimised. Brewer and Kerslake (2015) draw a similar conclusion and find that low empathy is closely associated with antisocial behaviours, such as cyber aggression. Gini (2007) find that young people who have “affective empathy” are more likely to be involved in bullying intervention, while Mayberry and Espelage (2007) find that non-aggressive youth have higher empathy. Based on these findings, we argue that:
H1: Higher virtual empathy towards individuals is associated with lower cyber aggression inclination.
Low Self-Control and CAI
According to Duckworth and Kern (2011), self-control is a concept of interest to psychologists that is interchangeably used with other terms such as impulsivity, self-regulation, self-discipline, willpower, effortful control, ego strength, and inhibitory control (Evenden, 1999; White et al., 1994; Whiteside et al., 2005). S. Li and Nie (2023, p. 2) define self-control as “the ability to override or change one’s inner responses, as well as to interrupt undesirable behavioral tendencies (such as impulses) and refrain from acting on them”. This definition suggests that self-control is a conscious act wherein the individual is actively motivated to regulate their behaviour. Additionally, Vohs and Baumeister (2004, p. 1) use the terms “self-control” and “self-regulation” interchangeably, defining them as the exercise of “control over oneself”. Drawing from the Social Cognitive Theory of self-regulation, self-control is also defined as the ability to regulate one’s behaviours, thoughts, and emotions (Bandura, 1991). However, Howard’s (2011) Quadripartite Violence Typology (QVT) differentiates between two dimensions of self-control: impulsive versus premeditated, in relation to instrumental/premeditated and affective/impulsive violence. The current research primarily focuses on low self-control, indicating reduced self-regulation and increased impulsive behaviour.
In order to develop our hypotheses, we refer back to the General Aggression Model mentioned above which suggests an association between self-control and aggression. Anderson and Bushman (2002) suggest that a lack of self-control may be linked to aggressive tendencies in that an individual cannot sufficiently restrain impulses that are harmful to others. Vazsonyi et al. (2012) studied low self-control across 25 European countries and found that a deficit of self-control is associated with behavioural issues such as cyber-aggression. Further, DeWall et al. (2011) point out that the more self-control people have, the more likely it is that they will, before acting, consider the consequences of their actions towards others and choose to behave in a nonaggressive manner.
The findings above suggest that some researchers equate a lack of self-control with impulsivity, while others concentrate on outcome-oriented self-control, where individuals consciously regulate harmful behaviour. As previously mentioned, this research focuses on low self-control; therefore, we propose the following hypothesis:
H2: Low self-control is associated with higher cyber aggression inclination.
Prior Cyber-Aggression Victimisation and CAI
Cyber-aggression victimisation means prior exposure to intentional harm inflicted via information and communication technologies, such as being subjected to a form of aggressive behaviour online such as cyberbullying and cyberhate (Hawdon & Costello, 2020; Lewis et al., 2015; P. K. Smith et al., 2008; Wachs & Wright, 2018). As suggested by Hayes et al. (2020), experiencing aggression and victimisation can alter an individual’s personality. Existing evidence shows that being previously victimised by a cybercrime (such as cyber bullying) or offline bullying is associated with delinquent online behaviours. For example, P. K. Smith et al. (2008) find that victims of traditional bullying tend to become bullies themselves and bully others online.
There are many other studies showing a strong link between prior victimisation and the perpetration of cybercrime (Ang et al., 2011; Calvete et al., 2010; Dilmaç, 2009; Hinduja & Patchin, 2007; Vandebosch & Van Cleemput, 2009; Ybarra & Mitchell, 2004; Ybarra et al., 2006). For example, Farrington et al. (2011) find that prior experience of bullying is associated with delinquency in later life. This is consistent with the findings from a study by Sigfusdottir et al. (2010) involving 15- and 16-year old adolescents in Iceland, where the researchers found that the strain created by victimisation is associated with anger, which in turn can led to delinquency. Walters and Espelage (2018) find a strong association between victimisation and perpetration in a study involving adolescent/early adolescent children. The findings are consistent with the control model of criminal lifestyle development. Based on these findings, we argue that:
H3: Prior cyber-aggression victimisation is associated with higher cyber aggression inclination.
Subjective Norms, Social Pressure and CAI
Subjective norms and social pressure are separate concepts, and one is conceptualised as a personal factor and the other a situational factor. Despite this we discuss them together here as their effects on CAI have similar underlying mechanisms. Subjective norms can be defined as what an individual would perceive to be acceptable behaviour, depending on the attitudes and behaviours of people who are close or important to them (Ajzen & Fishbein, 1980; Fishbein & Ajzen, 1977; Rejón-Guardia et al., 2020; Venkatesh & Bala, 2008; Venkatesh & Davis, 2000). It can be argued that human aggression is reliant upon knowledge structures such as attitudes and beliefs (Anderson & Carnagey, 2004; Gilbert & Daffern, 2011), and aggressive knowledge structures are associated with aggressive behaviours (Allen et al., 2018). The potential relationship between normative beliefs and cyber aggression is complex and potentially different to those in the offline world. There is some evidence that people tend to behave more aggressively online when the social group norm was aggression (Rösner & Krämer, 2016). Further, although there was no direct effect of anonymity, people were more likely to conform to an aggressive social norm in an anonymous environment. Relatedly, students who experience classrooms where online aggression is considered normative (due to a higher frequency) are more likely to engage in aggressive online acts (Bullo & Schulz, 2022). However, the influence of the normative group did not extend to increases in an individual’s level of aggression with changes in individual levels of aggression is the same irrespective of their peers’ reports of online aggression
Whether behaviours are deemed appropriate or not is subjective and is partly determined by cultural factors (Lu et al., 2019). With reference to anti-social behaviours, Millie (2008, p. 379) argues that “what is regarded as anti-social is also determined by social and cultural norms of aesthetic acceptability”. Norms of the acceptability of aggressive behaviour are therefore context-specific and are influenced by the social actors present in a particular environment. For example, studies on aggressive language and bystander behaviour show that aggressive language originates in groups with similar normative assumptions and expectations (Parvaresh & Tayebi, 2018). Social groups tend to influence intra- and intergroup behaviours (Densley & Peterson, 2018; Ferreira et al., 2020). Hence it can argue that in-group/out-group behaviours are closely linked to peer pressure (Tajfel et al., 1971).
Aderibigbe and Ocholla (2020, p. 5) argue that “subjective norms are an important attribute when determining ethical intention with respect to cyber technology” and state that “reference groups…have influential roles to play in determining ethical and unethical cyber behaviour”. These reference groups could be family as in Subjective Norms, or social peers resulting per pressure. Drawing on prior studies (Aderibigbe & Ocholla, 2020; Richetin et al., 2011; Setijanto et al., 2019), Subjective Norms and Social Pressure are treated as separate variables in this study. Both norms and social pressure are collective expectations and in certain societal settings, individuals may be influenced or compelled to adhere to certain norms (Theriault et al., 2021). Further, Barlett (2023, p. 6) argue that “cyberbullying perpetration is a learned social behavior” and can be explained using the social learning theory. Hence, we suggest the following two hypotheses:
H4: Negative normative beliefs about cyber aggression are associated with lower cyber aggression inclination.
H5: Increased social pressure is associated with lower cyber aggression inclination.
Intrinsic Religiosity and Cyber Aggression Inclination
Religiosity is a widely studied concept in psychology, personality, mental health, ethics, and marketing settings (Abeyta & Blake, 2020; Mosqueiro et al., 2015; Pirutinsky et al., 2011; Uysal & Okumuş, 2019). It is a complex construct with multiple definitions (Abdel-Khalek, 2019). Allport and Ross (1967) introduced two dimensions of religiosity: intrinsic and extrinsic. In this paper, we follow Mendolia et al. (2019, p. 2) who argued that “intrinsic religiosity is a better indicator of the role that religion per se plays in an individual’s decisions and attitudes”. To this end, intrinsic religiosity is defined as the tendency of a person to find their motivation in their religion (Allport & Ross, 1967) and intentionally “integrate religion into one’s life” (Pirutinsky et al., 2011).
Several papers find an association between intrinsic religiosity and risky behaviour. It has been argued that religiosity provides individuals with a reference framework of what behaviours are risky/acceptable and how to control and regulate one’s behaviours (Hungerman, 2014; McCullough & Willoughby, 2009; Mellor & Freeborn, 2011). Some suggest that religious commitment leads to positive social interactions (e.g., Hardy et al., 2012). Conversely, Golec de Zavala et al. (2012) identified intrinsic religiosity as a predictor of intergroup hostility. Further, in a study involving adolescents in religious and secular schools in Israel, it was found that “cyber-bullying was more common among secular students than religious students” (Tesler et al., 2019). Here, we propose to test the following hypothesis:
H6: Intrinsic religiosity is associated with lower cyber aggression inclination.
Perceived Anonymity and CAI
Hite et al. (2014, p. 23) defined anonymity “as the state of being unidentified or unknown”. In communications and information systems research, anonymity is further described as “environmental, content-based, and procedural” (Gavish & Gerdes, 1998, p. 297) and incorporates non-identifiability (Marx, 1999; Wallace, 1999). However, there is debate among scholars regarding the distinction between “perception of anonymity” and “actual anonymity” (Gavish & Gerdes, 1998; Hite et al., 2014; C. R. Scott, 1998). For example, Mishna et al. (2009) find that anonymity is considered integral to cyber bullying, but that participants are uncertain as to “whether the Internet and other communication technologies provide actual or perceived anonymity for the aggressor”. Choi et al. (2016) tested the concept “degree of anonymity perception” by classifying it into social anonymity, visual anonymity, definitive anonymity, and location anonymity. Results revealed that online community users with a high degree of visual and location anonymity are more likely to post malicious messages. As a construct, anonymity has also been studied as two broad categories in online communication research: technical anonymity and social anonymity. Technical anonymity refers to the removal of personally identifiable information about a person whereas social anonymity refers to the individual’s perception of identifiability due to the lack of personal cues (Hayne & Rice, 1997). Hence, Christopherson (2007, p. 3040) argues that “it may not be the case that one is truly anonymous in a social context, but the individual perceives him or herself to be anonymous to others”.
Studies show that varying levels of perceptions about anonymity are found to be correlated with different levels of behaviours (Piazza & Bering, 2008). In online settings, perceived anonymity is found to be negatively associated with self-awareness and self-control, which in turn results in deindividuation (Hilvert-Bruce & Neill, 2020; Lowry et al., 2016; Suler, 2004; Zimbardo, 1969). The deindividuation effect has also been found to reduce awareness of oneself and reduce the impact of social norms, leading to a disinhibition effect and influencing aggressive behaviours (Diener, 1976; Dooley et al., 2009; Festinger et al., 1952; Nakano et al., 2016; Perfumi, 2020; Rogers & Prentice-Dunn, 1981; Suler, 2004; Vranjes et al., 2020; Wright, 2013, 2014a, 2014b). Barlett and Gentile (2012) provide more supporting evidence to suggest that in first time youth cyberattacks, the individuals learn to perceive themselves as more anonymous online and this perceived anonymity could lead to perceived cyber-attacks and cyber bullying. Based on these findings, we suggest that:
H7: Higher perception of anonymity is associated with higher cyber aggression inclination.
Perceived Incident Severity and CAI
Studies show that aggressive acts online can have a more severe impact on individuals than their offline equivalents (e.g., cyber bullying versus traditional bullying; Dredge et al., 2014; Gül et al., 2019; Wang et al., 2019). Some argue that the severity of incidents in online behaviour can be viewed through the perception of either the target (victim) or the bystanders (e.g., Macaulay et al., 2019). From a bystander’s perspective, the decision to assist a victim of cyberbullying depends on the perceived severity of the incident (Bastiaensens et al., 2014; Roman et al., 2020). For instance, bystanders may perceive a situation as more severe if it includes threats of physical assault (Allison & Bussey, 2016). Studies involving young people have shown that bystanders assess the likely impact of different types of bullying on victims and that the severity of an incident influences their willingness to intervene (Bastiaensens et al., 2014; Cappadocia et al., 2012; Chen et al., 2015; Macaulay et al., 2019; Obermaier et al., 2016; K. R. Williams & Guerra, 2007). A recent study on celebrity abuse on Twitter found that “the volume of abuse influenced both attributed blame and perceived incident severity” (G. G. Scott et al., 2020, p. 23).
The severity of an incident can also be viewed from the victim’s perspective. For example, Rivers & Noret (2010) identified several forms of cyberbullying (e.g., verbal abuse, uploading images onto websites, distributing images via mobile phones) and argued that the severity of the incident varies with the nature of the bullying experienced by the victim. G. G. Scott et al. (2020) suggest that interpretations of abusive incidents will differ among individuals. In other words, certain behaviours may be deemed less severe by some, potentially increasing their inclination toward aggression. Therefore, in the current research, we employ the concept of “perceived incident severity” to denote an individual’s assessment of the likely impact of an aggressive act on another person (Chen et al., 2015; Kwan & Skoric, 2013; Vandebosch & Van Cleemput, 2009). The individual evaluating the situation and judging the incident’s severity may be either the victim or a bystander.
Therefore, we propose to test the following hypothesis:
H8: High perceived incident severity is associated with lower cyber aggression inclination.
Methods
Data Collection
The study population consists of social media users on the World wide web. In the absence of a sampling frame, the current research uses a non-probability convenience sampling. The sampling design of the current research is drawn from the works of (Brickman Bhutta, 2012; Göritz et al., 2012; Kapp et al., 2013; T. W. Smith, 2013) and closely follows the approach employed by Brickman Bhutta (2012) in similar web-based research. The survey instrument was developed using Qualtrics survey software. Prior to administering the survey, ethics board approval was obtained from the universities of the principal investigators; all participants were fully informed about the general scope of the study, informed consent was collected from every participant, and no remuneration was given for participation.
Given that the active social media user is a parameter of interest for this research, the online survey was posted on the SNS Facebook and LinkedIn. Over a period of fifteen months (November 2019–February 2021), we received 101 responses (respondents mainly from the UK and Sri Lanka with few from Spain, Germany, the USA, Canada, France, Finland, Singapore, Bangladesh, and Thailand). The response rate of the study was low because the topic was sensitive, and participants may have been reluctant to share information through the online survey. We acknowledge the small sample size and the length of time the survey was available. However, limiting the timeframe as we did is appropriate because of the rapidly evolving nature of online spaces and that online behaviour changed during the pandemic (Petrović et al., 2022). Data cleaning involved removal of any partial completed questionnaires from the dataset. This led to a diminished dataset of 71 responses, which was analysed using SPSS and SmartPLS 3. The measures used in this study are based on measures previously validated in the published literature. Table 1 provides a summary of the measures used and sources from which the scale items were obtained.
Table 1. Variable Measures.
|
Variable |
Source |
Items |
Scale used |
|
Virtual empathy |
Carré et al. (2013) |
EMP_2: I don’t become sad when I see other people crying. EMP_3: Other people’s feeling don’t bother me at all. EMP_6: Seeing a person who has been angered has no effect on my feelings. |
Strongly disagree (1)–Strongly agree (5)
|
|
(low) Self-control |
Grasmick et al. (1993) |
SELFC_5: I wish I had more self-discipline when in am using SNS. SELFC_7: Sometimes I can’t stop myself from doing something, even if I know it is wrong. SELFC_8: I often act without thinking through all the alternatives. |
Not at all like me (1)–Very much like me (5) |
|
Cyber-Aggression Victimisation |
Williams and Mattson (2006) |
PRIOR_VIC_1: How often in the last few months, have you had anyone telling lies or making fun of you on SNS? |
Very often (1)–Not at all often (4) |
|
Social pressure |
Buhrmester and Furman (2008) |
SOCIALP_1: How often do your friends push you to do things on SNS that you don’t want to do? SOCIALP_2: How often do your friends try to get you to do things on SNS that you don’t like? SOCIALP_3: How often do your friends pressure you to do the things they want on SNS? SOCIALP_4: How often do you feel obliged to share certain posts on SNS, even though you do not want to yourself? |
Very often (1)–Not at all often (4) |
|
Subjective Norms
|
Richetin et al. (2011) |
NORMS_1: People who are important to me think it is ok to use SNS to express my views against someone/a group when I am angry with them. NORMS_2: People who are important to me would approve of me using SNS to express my views against someone/a group when I am angry with them. NORMS_3: People who are important to me would be very happy if I use express my views against someone/a group when I am angry with them. |
Not at all likely (1)–Very likely (5) |
|
Intrinsic Religiosity |
Gorsuch and McPherson (1989) |
RELIG_2: Although I am religious, I don’t make decisions based on my religious beliefs. RELIG_3: Although I believe in my religion, many other things are more important in life. RELIG_4: How I treat others are not based on my personal religious beliefs. |
Strongly disagree (1)–Strongly agree (5) |
|
Perceived Anonymity |
Hite et al. (2014) |
ANON_3: I am easily identified as an individual by others. ANON_4: Others are likely to know who I am. ANON_5: My personal identity is known to. |
Very likely (1)–Not at all likely (4) |
|
Perceived Incident Severity |
Pabian et al. (2015) and 4 new items |
ISEV_1: Damaging someone else’s reputation by spreading rumours about them on SNS. ISEV_2: Liking and commenting on posts on SNS that are intended to bully a person/group (e.g., religious group). ISEV_3: Resharing a post containing hateful comments about a certain person/group (e.g., religious group) on SNS. ISEV_4: Insulting another person/group (e.g., religious group) publicly on SNS. ISEV_5: Posting embarrassing photos or videos of someone else on SNS. ISEV_6: Deliberately excluding someone from an online social group to make him/her feel excluded. ISEV_7: Sending threatening messages/reactions to someone on SNS. |
Not a severe incident (1)–Very severe incident (5) |
|
Cyber Aggression Inclination |
Buss and Perry (1992), Bryant and Smith (2001) |
AGG_INC_1: I often use SNS to express my views against someone/a group that I don’t like. AGG_INC_2: I often create posts on SNS that are against people/groups I don’t like. AGG_INC_3: I often reshare posts condemning a person/group I don’t like. AGG_INC_4: I often comment on posts I see on SNS that are about people/groups that I don’t like. AGG_INC_5: I am not concerned about how my behaviour on SNS would affect a person/groups I don’t like. |
Strongly disagree (1)–Strongly agree (5) |
Dependent and Independent Variables
All five items for measuring the dependent variable “cyber aggression inclination” were developed using Buss and Perry (1992) and Bryant and Smith (2001). When tested, the items showed high reliability and all items were retained in the final instrument. The items for the independent variables were developed as follows:
The seven items for “virtual empathy” were derived from Carré et al. (2013). Initial testing identified a very low Average Variance Extracted. Further investigation revealed that one item (item 7) loaded onto a factor on its own. Although the construct was expected to be unidimensional, the remaining items loaded onto two factors. Items 2, 3 and 6 loaded onto one which we term “unemotional”. Items 4 and 5 loaded onto a second factor we label as empathy; item 1 was dropped due to a loading below 0.7. Self-control had eight items sourced from Grasmick et al. (1993) measured on a scale Not at all like me (1)–Very much like me (5). A similar issue emerged where a scale expected to be unidimensional produced two factors. Items 1, 2, 3 and 4 loaded onto one factor which captured perceived self-control whilst items 5, 6, 7, 8 loaded onto a separate factor which we label impulsive SNS use. Cyber-Aggression Victimisation is measured using a single item asking if the respondent had experienced being made fun of or lied about. The “subjective norms” construct was measured using three items, all of which were retained. Similarly, the four items sourced from Buhrmester and Furman (2008) to measure social pressure were found to have high reliability and were retained for the final questionnaire Intrinsic religiosity was measured using four items. One (item 1) was dropped because of a low loading. The other three items were reverse coded so that a higher score reflects a greater degree of religiosity. “Perceived anonymity” was measured using five items. Finally, Perceived Incident Severity was measured using 7 items.1 Three of these items were based on Pabian et al. (2015). We also added four new items (i.e., items 1–4) to broaden the scope of the types cyber bullying scenarios that would be deemed as severe to include spreading rumours about someone and liking or sharing bullying or hurtful comments. When all seven items were used, the reliability measures, Cronbach’s alpha and Composite Reliability, were very high (above .97). Items 3 and 4 were found to be strongly correlated so item 3 was dropped as a redundant item.
In Table 2 we present the respondents’ demographic information. Majority of the respondents (69%) were female and 30% were male respondents. 97% of the respondents were educated at University degree level. The distribution based on job status shows that 62% of the sample were employed and 25% unemployed. Marital status shows 63% of respondents as single and 37% as married. The majority of respondents are aged under 50, with just over half (52%) aged 18–28.
Table 2. Participants’ Demographics (Obs. = 71).
|
Measure |
% |
|
Gender |
|
|
Male |
30 |
|
Female |
69 |
|
Non-binary |
1 |
|
Level of education |
|
|
Secondary education |
3 |
|
University degree |
97 |
|
Current job status |
|
|
Self-employed |
11 |
|
Employed |
62 |
|
Unemployed |
25 |
|
Prefer not to say |
1 |
|
Marital status |
|
|
Single |
63 |
|
Married |
37 |
|
Age |
|
|
18–28 |
52 |
|
29–39 |
30 |
|
40–49 |
13 |
|
50–59 |
0 |
|
60–69 |
1 |
|
Over 69 |
4 |
|
Prefer not to say |
|
Empirical Approach
We use Partial Least Squares-Structural Equation Modelling (PLS-SEM) in the assessment of measurement, structural models, and hypotheses testing. PLS-SEM does not require a normal distribution of data and can accommodate smaller sample sizes.
The first step in PLS-SEM assessment involves an examination of the measures of item reliability, construct reliability, and convergent validity, which are assessed using the criteria discussed in Hair et al. (2011), Bagozzi and Yi (2012). As discussed above, several items showed low loadings and they were removed to improve the overall reliability and validity of the measurement model. This was assessed using the criteria discussed in Hair et al. (2011) and Bagozzi and Yi (2012). Table 3 shows the test statistics for items that remained. All of the constructs demonstrated satisfactory reliability (assessed using Cronbach’s Alpha and Composite Reliability) and convergent validity (all loadings are greater than 0.7 and all Average Variance Extracted values are above 0.5). Discriminant validity is then assessed using the square root of average variance extracted (AVE) values and item correlations. Table 4 shows the discriminant validity where the values in bold along the diagonal are the square root of the AVE of the latent variables. Off-diagonal elements are the correlation values between the variables. Discriminant validity is adequately demonstrated in this study since the diagonal elements are larger than the off-diagonal elements in the corresponding row and column (Duarte & Raposo, 2010; Hair et al., 2011).
We also investigated the degree of skewness and kurtosis for the constructs. Both skewness and excess kurtosis values lay outside the acceptable range of −2 to 2 for Cyber Aggression Inclination (skewness = 2.184 and excess kurtosis = 5.964) as do excess kurtosis values for Cyber Aggression Victimisation’s (5.424) and for Unemotional (2.528). All other skewness and kurtosis values lay within the −2 to 2 range.
Table 3. Reliability and Validity Assessment.
|
Constructs |
Items |
Loadings |
AVE |
Composite Reliability |
Cronbach’s Alpha |
|
Prior aggression victimisation |
PRIOR_VIC_1 |
1.000 |
1.000 |
1.000 |
1.000 |
|
Cyber aggression inclination |
AGG_INC_1 |
.867 |
.783 |
.947 |
.930 |
|
AGG_INC_2 |
.916 |
||||
|
AGG_INC_3 |
.919 |
||||
|
AGG_INC_4 |
.871 |
||||
|
AGG_INC_5 |
.849 |
||||
|
Perceived anonymity |
ANON_3 |
.847 |
.815 |
.929 |
.886 |
|
ANON_4 |
.936 |
||||
|
ANON_5 |
.922 |
||||
|
Unemotional |
EMP_2 |
.860 |
.741 |
.852 |
.659 |
|
EMP_3 |
.759 |
||||
|
EMP_6 |
.813 |
|
|
|
|
|
Empathy |
EMP_4 |
.830 |
.723 |
.839 |
.618 |
|
EMP_5 |
.870 |
||||
|
Perceived incident severity |
ISEV_1 |
.957 |
.856 |
.973 |
.968 |
|
ISEV_2 |
.903 |
||||
|
ISEV_3 |
.937 |
||||
|
ISEV_5 |
.930 |
||||
|
ISEV_6 |
.887 |
||||
|
ISEV_7 |
.946 |
||||
|
Subjective norms |
NORMS_1 |
.870 |
.823 |
.933 |
.892 |
|
NORMS_2 |
.922 |
||||
|
NORMS_3 |
.929 |
||||
|
Intrinsic religiosity |
RELIG_2 |
.855 |
.707 |
.876 |
.821 |
|
RELIG_3 |
.964 |
||||
|
RELIG_4 |
.678 |
||||
|
Perceived self-control |
SELFC_1 |
.665 |
.627 |
.869 |
.809 |
|
SELFC_2 |
.844 |
||||
|
SELFC_3 |
.771 |
||||
|
SELFC_4 |
.87 |
||||
|
Impulsive SNS use |
SELFC_5 |
.695 |
.597 |
.853 |
.787 |
|
SELFC_7 |
.864 |
||||
|
SELFC_8 |
.880 |
||||
|
Social pressure |
SOCIALP_1 |
.890 |
.659 |
.885 |
.838 |
|
SOCIALP_2 |
.890 |
||||
|
SOCIALP_3 |
.720 |
||||
|
SOCIALP_4 |
.740 |
Table 4. Discriminant Validity.
|
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
|
|
1 Cyber Aggression Inclination |
.885 |
||||||||||
|
2 Cyber Aggression Victimisation |
−.039 |
1 |
|||||||||
|
3 Empathy |
.258 |
.099 |
.85 |
||||||||
|
4 Intrinsic Religiosity |
.199 |
.326 |
.229 |
.841 |
|||||||
|
5 Impulsive SNS use |
.508 |
−.103 |
.221 |
.084 |
.773 |
||||||
|
6 Perceived Anonymity |
.601 |
−.104 |
.368 |
.052 |
.374 |
.903 |
|||||
|
7 Perceived Incident Severity |
.151 |
−.023 |
.046 |
.033 |
.069 |
.117 |
.925 |
||||
|
8 Perceived Self Control |
−.078 |
−.039 |
−.036 |
−.112 |
−.158 |
−.099 |
.263 |
.792 |
|||
|
9 Subjective Norms |
.617 |
−.011 |
.153 |
.176 |
.36 |
.598 |
.041 |
.026 |
.907 |
||
|
10 Social Pressure |
.226 |
.301 |
.189 |
.329 |
.004 |
.078 |
.281 |
−.002 |
.79 |
.81 |
|
|
11 Unemotional |
.409 |
.25 |
.043 |
.177 |
.25 |
.327 |
.146 |
.223 |
.373 |
−.0 |
.812 |
|
Note. Elements in bold are the square root of the AVE for that construct; other elements are correlation coefficients. |
|||||||||||
Results
Structural Model Assessment and Hypotheses Testing
SmartPLS 4 was used to assess the structural model. This involved testing the hypothesised relationships among the latent constructs and evaluating the coefficient of determination (R2). The R2 suggests that the independent constructs explain 59% of the variation in CAI. We then use a bootstrapping re-sampling procedure to assess the significance of the path estimates for hypotheses testing (Hair et al., 2011; Tenenhaus et al., 2005). PLS-SEM is suitable for the small sample size of this study because it is capable of achieving high statistical power (Reinartz et al., 2009; Sosik et al., 2009). To test the significance of the path coefficients, one-tailed hypothesis tests are adopted.
The path estimates are presented in Table 5. The results support the hypothesised association between unemotionality and CAI, however, empathy is not significantly associated with CAI (H1), impulsive SNS use and CAI, but not between self-control and CAI (H2), subjective norms and CAI (H4), and lastly perceived anonymity and CAI (H7).
Table 5. Path Coefficients, Significance Tests and Effect Sizes.
|
Pathway |
Path coefficient |
Standard deviation |
t statistic |
p value |
f-square |
|
|
H1 |
Emapthy → Aggression inclination |
.038 |
.086 |
0.44 |
.330 |
.003 |
|
Unemotional → Aggression inclination |
.215 |
.127 |
1.69 |
.046 |
.071 |
|
|
H2 |
Perceived Self Control → Aggression inclination |
−.083 |
.128 |
0.653 |
.257 |
.013 |
|
Impulsive SNS use → Aggression inclination |
.228 |
.109 |
2.086 |
.019 |
.095 |
|
|
H3 |
Prior aggression victimisation → Aggression inclination |
−.122 |
.117 |
1.045 |
.148 |
.026 |
|
H4 |
Subjective Norm → Aggression inclination |
.303 |
.121 |
2.507 |
.006 |
.125 |
|
H5 |
Social Pressure → Aggression inclination |
.203 |
.174 |
1.166 |
.122 |
.073 |
|
H6 |
Intrinsic Religiosity → Aggression inclination |
.039 |
.135 |
0.293 |
.385 |
.003 |
|
H7 |
Perceived Anonymity → Aggression inclination |
.226 |
.112 |
2.028 |
.021 |
.07 |
|
H8 |
Perceived Incident Severity → Aggression inclination |
.024 |
.128 |
0.188 |
.425 |
.001 |
|
Note. Standard deviations are bootstrapped using 5,000 subsamples. |
||||||
Cohen’s (1988) Effect size (f2) calculations are also shown in Table 5; f2 values of .02, .15 and .35 signify small, medium and large effects respectively. Subjective norms have effect size of .125, just below the benchmark for a medium effect. Social pressure shows an effect size of .071 which can be considered as having a small effect on CAI. Impulsive SNS use (.095) and perceived anonymity (.07) shows size effects that are also small. All the other constructs with significant coefficients have a small effect on the dependent construct.
Discussion
Factors That Are Found to Be Significantly Associated With Cyber Aggression Inclination
The analysis of the data confirmed the hypothesised relationships between one of our two measures of virtual empathy and CAI (H1), one of our two measures of self-control and CAI (H2), subjective norms and CAI (H4), and between perceived anonymity and CAI (H7). For example, Fraser et al. (2012) find an association between low empathetic concern lower prosocial behaviour toward strangers in the context of violent video gaming. However, in a similar context, Lemercier-Dugarin et al. (2021) find that gamers with high levels of empathy are “less likely to be toxic”. Further findings by Marín-López et al. (2020) find no association between online empathy and deviate behaviours such as cyberbullying. Our results show an indifference to others’ emotions is associated with CAI whilst empathy has no effect on it. As such our findings support those reported by Marín-López et al. (2020) and by Fraser et al. (2012).
In support of H2, it was found that low self-control, in terms of impulsive use of SNS is positively associated with cyber aggression inclination. Our measure of perceived self-control however shows no association with CAI. In another study involving students, those with high self-control show positive regulation of behaviour and avoid acts of violence against their friends (Cantone et al., 2015). In the context of online social networking and ICT-led communication, an absence of self-control is found to increase cyber-aggression (Runions, 2013). Individual differences in self-control also seem to contribute to proclivities for aggression and antisocial behaviour (Gottfredson & Hirschi, 1990). Further, Lee et al. (2013, p. 736) identify self-control as a “constructs related to controlling one’s actions” and argue that “self-control decreases virtual aggression”. In a more recent study, Peker and Yildiz (2021, p. 40) found that self-control could mediate the relationship between the aggressive behaviors and the cyber bullying behaviors which suggests room for future research in testing the mediating effect of self-control on CAI.
Evidence supporting the findings of H4 show that normative beliefs are associated with cyber aggression. Studies show that individuals who approve of classmates/peers who are involved in cyberbullying are more likely to become cyberbullying perpetrators (Doane et al., 2014; Festl et al., 2015; Sasson & Mesch, 2014). Further, in adolescent studies, subjective norms were identified as a potentially strong predictor of the intention to engage in cyberbullying behaviour (Heirman & Walrave, 2012; K. R. Williams & Guerra, 2007). In online gaming environments, normative beliefs significantly predict cyberaggression (Hilvert-Bruce & Neill, 2020). In contrast, Festl (2016) found that subjective norms do not have a significant role to play in the individual perpetration of bullying.
Our findings also show that perceived anonymity and CAI are associated (H7) and this is supported by prior research. In social media research there is evidence to suggest that users can become more verbally aggressive in an anonymous environment (Rösner & Krämer, 2016). Another study reveals that “aggressor-perceived anonymity is an important risk factor for later cyberbullying behaviour” (Barlett et al., 2016, p. 171). Several other studies support our findings that identify anonymity as a contributor to online aggression because it allows individuals to act in a disinhibited way (Herring, 1999; Joinson, 2007; Q. Li, 2007; Tanis & Postmes, 2007).
Factors That Are Not Significantly Associated With Cyber Aggression Inclination
The remaining hypotheses (H3, H5, H6 and H8) are not supported by the data. There is evidence from past research which suggest that a history of past abuse and victimisation could be associated with abusive behaviour and victimization of others in adulthood (Firoozabadi, 2020). This is in contrast to our finding for (H3) which shows no association between prior aggression victimisation and CAI. The above research involved reviewing of patients referred to a private outpatient clinic. The contextual differences and the self-report nature of data we obtained for our study could account for the lack of support for H3 in the current study.
Moreover, H5 was also not supported. In previous research, it was argued that influence of others on cyberbullying could depend on the priorities of a certain group and the unity/coherence of the group (Dang & Liu, 2020). This is further supported by Bleize et al. (2021) where it is argued that conformity to peer behaviour and social identification could be associated with aggression in adolescent. In the current study, we were not studying specific groups (e.g., peer groups, adolescents, gender groupings of respondents, cultural or other social grouping) and the respondents were reporting their individual behaviours rather than in the context of a specific group. This could account for the findings for H5. This might also explain why similar sized path coefficients attached to other constructs are significant. There certainly seems to be more variation (as captured by the standard deviation) for this construct, which in turn reduces the value of the t-statistic.
In H6 our expectation was that intrinsic religiosity would have a negative effect on CAI, drawing on earlier findings that religiosity can regulate behaviour. Instead, we find no significant association between them. However, in this our study supports Bhargava and Kaura’s (2020) finding that religiosity is not significantly associated with aggression.
We also explored the association between perceived incident severity and CAI in H8 which was not supported. This may reflect the difficulties of measuring perceived severity in a survey study rather than a scenario-based study. Moreover, the current research used the concept of “perceived incident severity” to denote an aggressor’s evaluation of the likely impact of an aggressive act on a victim. This is a personal evaluation that an aggressor would perform subjectively and from one individual to another, this assessment could vary. For instance, what may be considered as a “severe” incident by one person may be perceived as no so by another. Therefore, future, research should consider adopting a scenario based or vignette-based approach with multi-level modelling as they enable researchers to collect rich data on topics that present challenges when trying to study them directly (Baguley et al., 2022).
To extend our analysis further we apply Importance-Performance Map Analysis (IPMA) to our PLS results (Ringle & Sarstedt, 2016, provide an overview). The strength of relationship between constructs is captured by the magnitude of the coefficient. In IPMA this is termed importance and is captured by unstandardized total effects of a construct which is rescaled to lie between 0 and 100. IPMA additionally considers the average latent score (performance). From this, researchers can identify constructs which have a strong relationship with the target construct but also have relatively low or high performance (relatively low or high average scores). A construct with high importance but low performance could be a target for intervention. The high importance shows a greater effect of a change in a predecessor construct on the target variable. Low/high performance indicates that there is scope to increase/decrease the value of that predecessor construct.
By convention, IPMA results are presented as a plot of Importance (on the X axes) against Performance (on the Y axis). Importance and Performance values were calculated using SmartPLS4. The map resulting from IPMA analysis on our data is shown in figure 1 below.
Figure 1. Importance-Performance Map Analysis.
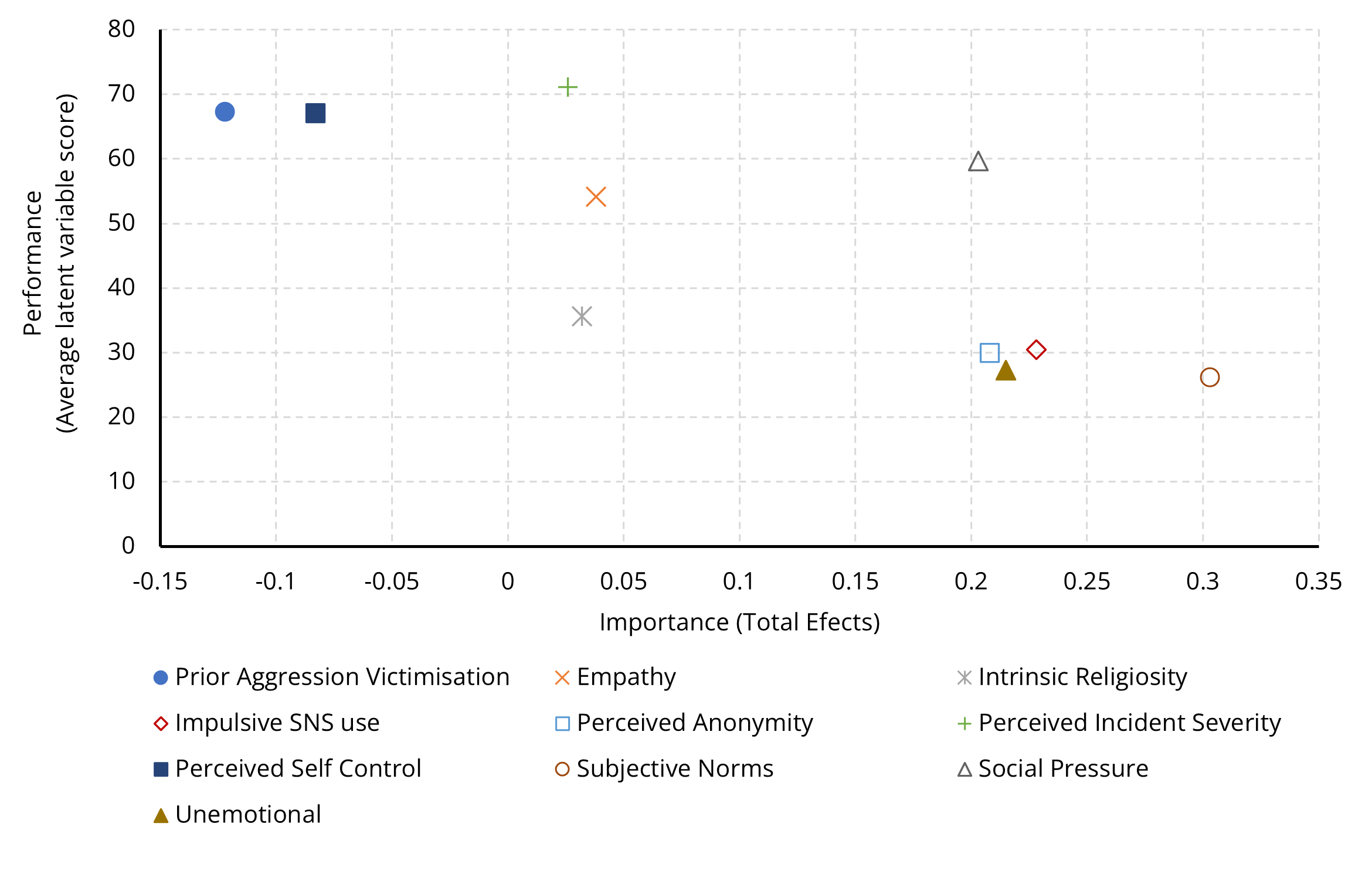
The four constructs with significant pathways: perceived anonymity, Impulsive SNS use, Subjective Norms and Unemotional; all appear on the right-hand side of the map. They also all have lower performance than most other constructs (indicating that responses tend towards the lower end of the scale). Of these, Subjective Norms and Perceived Anonymity would be more easily influenced than impulsive use or being unemotional. The Subjective Norm items are phrased so that lower performance is the desirable outcome. Lower performance signifies that posting view when angry would not be approved of by those important to the respondent. As such there is less scope to influence subjective norms further. A similar argument holds for perceived anonymity.
Social Pressure seems to stand out in the map. Although the coefficient is not significant at the 5% level, but that seems in part to be the result of a higher standard deviation. The coefficient is not that much smaller than other (significant) constructs with a similar effect size (f2 = .073). The higher performance suggests that respondents tended towards agreeing that their online behaviour was influenced by peer pressure. This might suggest a role for reducing peer pressure as a way of reducing cyber aggression inclination, assuming that the non-significant result is a quirk of our data. It certainly seems to suggest that the role of social/peer pressure, separate to subjective norms would be a useful avenue for future investigation.
Implications for Research and Practice
In the development of the hypotheses, several theories informed the direction of the current research. The findings suggest that we can strengthen some of the theoretical perspectives discussed earlier and provide theoretical contributions to a new understanding of cyber aggression from various perspectives. For example, in developing H1, we used Social Ecology Theory to examine the association between (lack of) empathy and aggression. Based on our finding, we can strengthen the argument that individuals interact with varying social contexts or ecological systems and in doing so, influence and are influenced by social relations and the broader culture (Swearer & Espelage, 2004). Similarly, H2 was developed based on Social Cognitive Theory and The General Aggression Model. Our findings are consistent with these theories. Our findings also support the notions presented in Social Learning Theory used to develop H4, where it was argued that cyberbullying perpetration is a learned social behaviour. Social Learning Theory was originally designed to theorise about crime in the physical world. However, our application of the model to virtual worlds extends the applicability of the model in new social contexts (Lowry et al., 2016).
This research adds strength to the argument that situational factors, particularly the behaviour of peers and other social actors around us influence our online behaviour. Specifically, we find that social pressure, low self-control and perceived anonymity show the strongest associations with CAI. The anonymity afforded by online social spaces does appear to contribute to deviant online behaviours. The lack of support for associations between CAI and prior victimisation, incident severity and social pressure suggest an avenue for future research using both quantitative and qualitative data to get a better understanding of how they relate to CAI.
The study also has practical implications. For example, consider the study of the variables “subjective norms” and “social pressure”. While normative beliefs and social pressure are mostly studied as interchangeable constructs (Dang & Liu, 2020; Leone & Parrott, 2019; Piccoli et al., 2020; Xu et al., 2016), the current study explored them as separate variables. This is a unique contribution that highlights the importance of further research into these separate constructs in online social settings. Current findings also suggest that negative normative beliefs are associated with CAI. This finding can influence the policies adopted by social networking communities against aggressive actions. These community policies can serve as a behavioural norm for members, and thereby contribute to the reduction of aggressive behaviours in SNS (Butterfield et al., 2000; Valentine & Bateman, 2011; Xu et al., 2016).
The current study highlights the importance of subjective norms for cyber aggression inclination; this has implications for Social Networking Site content providers. Specifically, trying to influence positive subjective norms (through content posted) may discourage aggressive online behaviours. Previous research shows that it is possible to manipulate subjective norms so as to change behavioural intentions (Grimes & Marquardson, 2019). Therefore, promoting more positive subjective norms may enable levels of aggression to be mitigated.
As subjective norms are associated with people who are close to or important to individuals who engage in cyber aggressions, social media and government law enforcement bodies can consider this second layer of the responsibility networks and initiate some form of social adjustment and orientation program. Using the Covid-19 pandemic as an analogy, the health and safety measures directed at Covid-19 victims differ from those directed at the victims’ associates. As cybercrimes have long-term impact and can themselves operate as CAI triggers, it is important to establish a legal framework that identifies as two separate but related groups (i) the perpetrators of aggressive acts online, and (ii) the perpetrators’ associates, and implements measures that treat each group appropriately. As noted above, the role of social pressure, as distinct from subjective norms, would merit further investigation. Although non-significant in our model, the effect size and path coefficients are of similar magnitude to other (significant) results. This might suggest that there is something else influencing the effect of social pressure on cyber aggression behaviour.
The positive association between the impulsive use of SNS and CAI may indicate that socialisation is key to reducing the level of CAI by enhancing the ability of social media users to practise self-discipline. This might be achieved by nurturing socialisation processes within societies and organisations, highlighting their relevance to religious beliefs and orientations, and emphasising them in the training and education programs, ethics, CSR, and sustainability practices of various private and public sector organisations, and even in the rules and regulations of countries.
Individual perception of online anonymity can be influenced through Social Networking Site design. Developers can introduce measures that prevent social media profiles being created anonymously (Correa et al., 2021; Stutzman & Hartzog, 2012; Gerhart & Koohikamali, 2019). This may reduce the sense of safety and power felt by aggressors when using SNS for delinquent acts. Also, intervention strategies can be used where appropriate (e.g., automatic identification/filtering of aggressive posts on SNS; Barlett et al., 2020; Kim et al., 2020; Kumari et al., 2019; Modha et al., 2018, 2020). Creating awareness among users about the availability of built-in extensions of the social network to protect against cyberbullying is another consideration (Kintonova et al., 2021). Accordingly, we recommend that social media firms incorporate software features that reduce the disinhibition effect that can be arise from anonymity (such as linking a real name and contact details to a username).
Limitations
Some limitations in the current study should be acknowledged. First, the sample size, although meeting the analytical criteria of PLS-SEM, is small. As our results were obtained from a cross-section study, we can only draw conclusions regarding association. A longitudinal (larger scale) study would help to explore causation between the variables.
The current research found four of the eight hypotheses to be unsupported. This may be due to the small sample size. as the study found no evidence in relation to the social desirability bias of responses. The online survey could be improved with new and revalidated items in a future study involving a larger sample. For example, multidimensional concepts such as perceived anonymity can be studied in detail as social anonymity, visual anonymity, definitive anonymity, location anonymity, and technical and social anonymity (Choi et al., 2016; Hayne & Rice, 1997). Further, we did not directly ask participants to report whether they had religious beliefs. Therefore, it is not possible to disentangle participants responses to the religiosity scale according to whether participants held religious beliefs and disagreed with the scale items or whether they did not have religious beliefs. As the nature of the impact of contributing factors might be moderated or mediated by the demographics of the respondents, future study design might consider possible moderators and mediators. For example, the association between religiosity and criminal offending could be considered, given the argument that it may be mediated by self-control (Reisig et al., 2012).
A further limitation is that the current study relied on self-report methods and adopted a cross-sectional design. Therefore, it was not possible to fully explore whether intent translates into behavioural experiences or the extent to which the behaviour is cyclical in nature. Therefore, researchers may want to consider implementing longitudinal designs to allow a further exploration of the direction of the reported relationships and experiential methods as a mechanism to overcome memory bias (Scollon et al., 2003).
Conclusions
This study aimed to explore the concept of cyber aggression inclination and the personal and situational factors that contribute to it. The extant literature suggests that there is a paucity of empirical research exploring the concept of “cyber aggression”, particularly in the context of SNS (e.g., Suzor et al., 2019; Zhong et al., 2020; Zhu et al., 2020). Drawing inferences from various theories, we developed a theoretical framework using eight hypotheses that explore the links between personal and situational factors and CAI. Partial Least Squares-Structural Equation Modelling (PLS-SEM) was used to assess measurement, structural models, and hypotheses testing.
The findings suggest that three personal factors (virtual empathy, self-control, subjective norms) and one situational factors (intrinsic religiosity) are associated with CAI of SNS users, thereby contributing to the development of a conceptual model on cyber aggression inclination. Interestingly, the findings of the study do not provide statistically significant evidence for the influence of prior aggression victimisation, social pressure, and perceived incident severity on CAI. Overall, the study contributes to the advancement of various theories such as the General Aggression Model, Social Identity Theory, Theory of Planned Behaviour, the social identity model of deindividuation effects, Social Ecology Theory, and the General Theory of Crime and provides several important practical implications for key stakeholders in the social media industry. For example, our findings are relevant to the policies being adopted by social networking communities seeking to counter or reduce aggressive actions. The study also emphasises the role played by socialisation processes in reducing cyber aggression behaviour by social media users. We make the case for a wholesale adoption of these socialisation processes at organisation-, country- and global-level.
Footnotes
1 Respondents were asked to rate the following incidents on a scale of 1 (Not a severe incident) to 5 (A very severe incident):
- Damaging someone else’s reputation by spreading rumours about them on SNS.
- Liking and commenting on posts on SNS that are intended to bully a person/group (e.g., religious group)
- Resharing a post containing hateful comments about a certain person/group (e.g., religious group) on SNS.
- Insulting another person/group (e.g., religious group) publicly on SNS.
- Posting embarrassing photos or videos of someone else on SNS.
- deliberately excluding someone from an online social group to make him/her feel excluded.
- Sending threatening messages/reactions to someone on SNS.
Conflict of Interest
The authors have no conflicts of interest to declare.

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Copyright © 2024 Hemamali Tennakoon, Lucy Betts, Anil Chandrakumara, George Saridakis, Chris Hand



