Web of deceit: Relationships between the dark triad, perceived ability to deceive and cyberloafing
Vol.11,No.2(2017)
The rapid growth of digitally mediated work means that non-traditional forms of counterproductive workplace behaviours are emerging, such as cyberloafing: use of the Internet for non-work related purposes. Time lost due to cyberloafing can have substantial impact on productivity. This research was the first to investigate the mechanisms by which dark personality traits and perceived ability to deceive are associated with cyberloafing. A sample of currently or previously employed participants (N= 273), completed measures of psychopathy, Machiavellianism, narcissism, perceived ability to deceive and cyberloafing. Path analysis was used to evaluate the model, and revealed good fit. As predicted, PATD mediated the relationships between the Dark Triad and cyberloafing, while psychopathy also related to cyberloafing directly. These findings suggest that in order to reduce cyberloafing, workplace policy should target an individual’s confidence in their ability to evade detection when misusing the Internet. Future research could strengthen the approach taken here by including a behavioural measure of cyberloafing. It is concluded that perceived ability to deceive plays a vital role in determining the way in which individuals possessing dark personality characteristics engage in technology-based counterproductive work behaviours.
Counterproductive workplace behaviours; cyberloafing; perceived ability to deceive; personality traits; personal use of the Internet
Emily Lowe-Calverley
University of Tasmania, Hobart, Australia
Emily Lowe-Calverley is a PhD candidate in psychology at the University of Tasmania. Her research investigates
the social and psychological effects, processes, and personality factors underpinning image-based social media
use.
Rachel Grieve
University of Tasmania, Hobart, Australia
Rachel Grieve is a senior lecturer in psychology at the University of Tasmania. Her research interests include
online derived social connectedness and the psychosocial processes underpinning social media use.
Andreassen, C. S., Torsheim, T., & Pallesen, S. (2014). Predictors of use of social network sites at work: A specific type of cyberloafing. Journal of Computer-Mediated Communication, 19, 906-921. https://doi.org/10.1111/jcc4.12085
Arbuckle, J. L. (2014). Amos 23.0 user's guide. Chicago: IBM SPSS.
Askew, K., Buckner, J. E., Taing, M. U., Ilie, A., Bauer, J. A., & Coovert, M. D. (2014). Explaining cyberloafing: The role of the theory of planned behavior. Computers in Human Behavior, 36, 510-519. https://doi.org/10.1016/j.chb.2014.04.006
Babiak, P., Neumann, C.S., & Hare, R.D. (2010). Corporate psychopathy: Talking the walk. Behavioural Sciences and the Law, 28, 174-193. https://doi.org/10.1002/bsl.925
Beugre, C. D., & Kim, D. (2006). Cyberloafing: Vice or virtue? In M. Khosrow-Pour (Ed.), Emerging trends and challenges in information technology management, volume 1 and volume 2 (pp. 834-835). Pennsylvania: Idea Group Publishing. Retrieved from http://www.irma-international.org/viewtitle/32923/
Bibi, Z., Karim, J., & ud Din, S. (2013). Workplace incivility and counterproductive work behaviour: Moderating role of emotional intelligence. Pakistan Journal of Psychological Research, 28, 317-443. Retrieved from http://www.pjprnip.edu.pk/pjpr/index.php/pjpr
Brock, M. E., Martin, L. E., & Buckley, M. R. (2013). Time theft in organisations: The development of the time banditry questionnaire. International Journal of Selection and Assessment, 21, 309-322. https://doi.org/10.1111/ijsa.12040
Chen, J. V., Ross, W. H., & Yang, H. (2011). Personality and motivational factors predicting internet abuse at work. Cyberpsychology: Journal of Psychosocial Research on Cyberspace, 5(1), article 5. Retrieved from https://cyberpsychology.eu/article/view/4240/3286
Cheng, L., Li, W., Zhai, Q., & Smyth, R. (2014). Understanding personal use of the Internet at work: An integrated model of neutralization techniques and general deterrence theory. Computers in Human Behavior, 38, 220-228. https://doi.org/10.1016/j.chb.2014.05.043
Christie, R., & Geis, F.L. (1970). Studies in Machiavellianism. New York: Academic Press.
Cooke, D.J., & Michie, C. (2001). Refining the construct of psychopathy: Towards a hierarchical model. Psychological Assessment, 13, 171-188. https://doi.org/10.1037//1040-3590.13.2.171
de Vaus, D. (2014). Surveys in social research (6th Ed.). Abington, Oxfordshire: Routledge.
Emmons, R. A. (1987). Narcissism: Theory and measurement. Journal of Personality and Social Psychology, 52, 11- 17.
Ford, C. V., King, B. H., & Hollender, M. H. (1988). Lies and liars: Psychiatric aspects of prevarication. The American Journal of Psychiatry, 145, 554- 562. https://doi.org/10.1176/ajp.145.5.554
Garrett, R. K., & Danziger, J. N. (2008). On cyberslacking: Workplace status and personal internet use at work.
CyberPsychology and Behaviour, 11, 287- 292. https://doi.org/10.1089/cpb.2007.0146
Giammarco, E. A., Atkinson, B., Baughman, H. M., Veselka, L., & Vernon, P. A. (2013). The relation between antisocial personality and the perceived ability to deceive. Personality and Individual Differences, 54, 246-250. https://doi.org/10.1016/j.paid.2012.09.004
Grieve, R. (2012). The role of personality, psychopathy, and previous experience with assessment in intentions to fake in psychological testing. Current Psychology, 31, 414-422. https://doi.org/10.1007/s12144-012-9158-x
Grieve, R., & Hayes, J. (2013). Does perceived ability to deceive = ability to deceive? Predictive validity of the perceived ability to deceive (PATD) scale. Personality and Individual Differences, 54, 311-314. https://doi.org/10.1016/j.paid.2012.09.001
Grieve, R., & Panebianco, L. (2013). Assessing the role of aggression, empathy, and self-serving cognitive distortions in trait emotional manipulation. Australian Journal of Psychology, 65, 79-88. https://doi.org/10.1111/j.1742-9536.2012.00059.x
Grijalva, E., & Newman, D.A. (2015). Narcissism and counterproductive work behavior (CWB): Meta-analysis and consideration of collectivist culture, big five personality, and narcissism’s facet structure. Applied Psychology: An International Review, 64, 93-126. https://doi.org/10.1111/apps.12025
Hare, R. D. (1996). Psychopathy: A clinical construct whose time has come. Criminal Justice and Behavior, 23, 25- 54.
Hislop, D., & Axtell, C. (2011). Mobile phones during work and non-work time: A case study of mobile, non- mangerial workers. Information and Organization, 21, 41-56.
Holtzman, N. S., Vazire, S., & Mehl, M. R. (2010). Sounds like a narcissist: Behavioural manifestations of narcissism in everyday life. Journal of Research in Personality, 44, 478-484. https://doi.org/10.1016/j.jrp.2010.06.001
Hu, L., & Bentler, P. M. (1999). Cutoff criteria for fit indexes in covariance structure analysis: Conventional criteria versus new alternatives. Structural Equation Modeling, 6, 1-55. https://doi.org/10.1080/10705519909540118
Jamaluddin, H., Ahmad, Z., Alias, M., & Simun., M. (2015). Personal internet use: The use of personal mobile devices in the workplace. Procedia – Social and Behavioural Sciences, 172, 495-502. https://doi.org/10.1016/j.sbspro.2015.01.391
Jia, H., Jia, R., & Karau, S. (2013). Cyberloafing and personality: The impact of the big five traits and workplace situational factors. Journal of Leadership and Organizational Studies, 20, 358-365. https://doi.org/10.1177/1548051813488208
Jones, D. N., & Paulhus, D. L. (2009). Machiavellianism. In M. R. Leary, & R. H. Hoyle (Eds.), Handbook of individual differences in social behaviour (pp. 93- 108). New York: Guilford.
Jones, D. N., & Paulhus, D. L. (2011). The role of impulsivity in the dark triad of personality. Personality and Individual Differences, 51, 679-682. https://doi.org/10.1016/j.paid.2011.04.011
Kubarych, T. S., Deary, I. J., & Austin, E. J. (2004). The narcissistic personality inventory: Factor structure in a non clinical sample. Personality and Individual Differences, 36, 857-872. https://doi.org/10.1016/S0191-8869(03)00158-2
Le Roy, J., Bastounis, M., & Minibas-Poussard, J. (2012). Interactional justice and counterproductive work behaviours: The mediating role of negative emotions. Social Behaviour and Personality, 40, 1341-1356. https://doi.org/10.2224/sbp.2012.40.8.1341
Levenson, M. R., Kiehl, K. A., & Fitzpatrick, C. M. (1995). Assessing psychopathic attributes in a noninstitutionalized population. Journal of Personality and Social Psychology, 68, 151-158. https://doi.org/10.1037/0022-3514.68.1.151
Lim, V. K. G. (2002). The IT way of loafing on the job: Cyberloafing, neutralizing and organizational justice. Journal of Organizational Behavior, 23, 675-694. https://doi.org/10.1002/job.161
Lim, V. K. G., & Chen, D. J. Q. (2012). Cyberloafing at the workplace: Gain or drain on work? Behaviour & Information Technology, 31, 343–353. https://doi.org/10.1080/01449290903353054
Mastrangelo, P. M., Everton, W., & Jolton, J. A. (2006). Personal use of work computers: Distraction versus destruction. CyberPsychology and Behavior, 9, 730-741. https://doi.org/10.1089/cpb.2006.9.730
Metin, U. B., Taris, T. W., & Peeters, M. C. W. W. (2016). Measuring procrastination at work and its associated workplace aspects. Personality and Individual Differences, 101, 254–263. https://doi.org/10.1016/j.paid.2016.06.006
O’Boyle, E. H., Forsyth, D. R., Banks, G. C., & McDaniel, M. A. (2012). A meta- analysis or the dark triad and work behaviour: A social exchange perspective. Journal of Applied Psychology, 97, 557-579. https://doi.org/10.1037/a0025679
Obushenkova, E. A., & Plester, B. (2015). Sending the wrong message: How company smartphones create new Psychological contract expectation. In Proceedings of the 29th Australian and New Zealand Academy of Management Conference (ANZAM 2015). Managing for Peak Performance, ANZAM, Queenstown, New Zealand. Retrieved from http://www.anzam.org/wp-content/uploads/pdf-manager/2575_044.PDF
Oravec, J. A. (2015). Gamification and multigamification in the workplace: Expanding the ludic dimension of work and challenging the work/play dichotomy. Cyberpsychology: Journal of Psychosocial Research on Cyberspace, 9(3), article 6. https://doi.org/10.5817/CP2015-3-6
Page, D. (2015). Teachers’ personal web use at work. Behaviour & Information Technology, 34, 443-453. https://doi.org/10.1080/0144929x.2014.928744
Paulhus, D. L., & Williams, K. M. (2002). The dark triad of personality: Narcissism, Machiavellianism, and psychopathy. Journal of Research in Personality, 36, 556-563. https://doi.org/10.1016/s0092-6566(02)00505-6
Raskin, R., & Terry, H. (1988). A principal-components analysis of the narcissistic personality inventory and further evidence of its construct validity. Journal of Personality and Social Psychology, 54, 890-902. https://doi.org/10.1037/0022-3514.54.5.890
Rauthmann, J. F. (2012). The dark triad and interpersonal perception: Similarities and differences in the social consequences of narcissism, Machiavellianism, and psychopathy. Social Psychological and Personality Science, 3, 487- 496. https://doi.org/10.1177/1948550611427608
Rauthmann, J. F. (2013). Investigating the MACH-IV with item response theory and proposing the trimmed MACH*. Journal of Personality Assessment, 95, 388-397. https://doi.org/10.1080/00223891.2012.742905
Schneider, T. J., & Goffin, R. D. (2012). Perceived ability to deceive and incremental prediction in pre-employment personality testing. Personality and Individual Differences, 52, 806-811. https://doi.org/10.1016/j.paid.2012.01.015
Sheikh, A., Atashgah, M. S., & Abidzadegan, M. (2015). Antecedents of cyberloafing: A case study in an Iranian copper industry. Computers in Human Behavior, 51, 172-179. https://doi.org/10.1016/j.chb.2015.04.042
Sherry, S. B., Hewitt, P. L., Besser, A., Flett, G. L., & Klein, C. (2006). Machiavellianism, trait perfectionism, and perfectionistic self-presentation. Personality and Individual Differences, 40, 829-839. https://doi.org/10.1016/j.paid.2005.09.010
Spector, P. E., & Fox, S. (2005). The stressor-emotion model of counterproductive work behaviour. In S. Fox & P.
Spector (Eds.), Counterproductive work behaviour: Investigations of actors and targets (pp. 151-174). Washington, DC: American Psychological Association.
Tennakoon, K. L. U. S., da Silveira, G. J. C., & Taras, D. G. (2013). Drivers of context-specific ICT use across work and nonwork domains: A boundary theory perspective. Information and Organization, 23, 107-128. https://doi.org/10.1016/j.infoandorg.2013.03.002
Widiger, T. A., & Lynam, D. R. (1998). Psychopathy and the five-factor model of personality. In T. Millon, E. Simonsen, M. Birket-Smith, & R. D. Davis (Eds.), Psychopathy: Antisocial, criminal and violent behaviour (pp. 171- 187). New York: Guilford.
Wu, J., & Lebreton, J. M. (2011). Reconsidering the dispositional basis of counterproductive work behaviour: The role of aberrant personality. Personnel Psychology, 64, 593-626. https://doi.org/10.1111/j.1744-6570.2011.01220.x
Zettler, I., & Solga, M. (2013). Not enough of a ‘dark’ trait? Linking Machiavellianism to job performance. European Journal of Personality, 27, 545-554. https://doi.org/10.1002/per.1912
Editorial Record:
First submission received:
October 13, 2016
Revision received:
April 4, 2017
Accepted for publication:
June 22, 2017
Introduction
Counterproductive work behaviours (CWBs) are intentional behaviours that go against the interests of an organisation, and often result in detrimental consequences for that organisation (Le Roy, Bastounis, & Minibas-Poussard, 2012). Common behaviours encompassed by the counterproductive banner include sabotage, theft, and withdrawal (Bibi, Karim, & ud Din, 2013; Spector & Fox, 2005). While theft in the workplace usually denotes an individual stealing assets that are not their own, a more subtle form of workplace theft is also gaining the attention of researchers and employers: time banditry. Time banditry is the act of employees engaging in non-work related activities whilst they are at work, thus essentially stealing time from their employers (Brock, Martin, & Buckley, 2013).
The Tech-Savvy Time Bandit
The technological distinction of time banditry, which can also be referred to as ‘cyberloafing’, involves behaviours such as sending and receiving non-work related emails, engaging in social media, and surfing the Internet for non-work related reasons whilst ‘on the clock’ (Brock et al., 2013). Technology is essential to the functioning of many workplaces, however the pervasiveness of technology and the Internet at work can invite misuse and distraction (Lim, 2002), that may go unnoticed by employers because of the often personal nature of computer and device use.
It is unclear whether cyberloafing can be defined as a purely harmful and counterproductive workplace behaviour. Metin, Taris, & Peeters (2016), define cyberloafing (or ‘cyberslacking’) as a form of workplace procrastination. While indeed an unhelpful behaviour in many respects, the authors established that cyberslacking as procrastination was separate from counterproductive workplace behaviour, as it lacks conscious harmful intent. Further research suggests that employees have a positive attitude toward cyberloafing and believe it is acceptable in the workplace (Lim & Chen, 2012). This belief suggests that employees do not ‘set out’ to harm their workplace or productivity through their cyberloafing. Furthermore, cyberloafing behaviours can have a positive impact on employees and their work, with Internet browsing positively influencing employee’s emotions (Lim & Chen, 2012). Therefore, defining cyberloafing purely as a CWB would be inaccurate. However, the parallels between CWBs and cyberloafing suggest that some of the predictors of CWB may also be relevant to cyberloafing where behaviour may be counterproductive but not intentionally harmful.
Recently, researchers have attempted to unpack some of the mechanisms by which cyberloafing occurs. Attitudes towards cyberloafing, subjective social norms, and perceived behavioural control (in this case the ability to hide cyberloafing) explain significant variance in an individual’s intention to engage in cyberloafing (Askew et al., 2014; Sheikh, Atashgah, & Abidzadegan, 2015). Neutralisation (in particular, where individuals do not feel that they are responsible for being familiar with company computer use policy), perceiving benefits of cyberloafing (for example, the convenience of using the Internet at work rather than at home), and feeling that detection of non-work related Internet access is unlikely, also predict intentions to use the Internet at work for personal purposes (Cheng, Li, Zhai, & Smyth, 2014). Perceptions of the usefulness of information and communication technologies (ICT) impact the use of work ICTs for non-work purposes (Tennakoon, da Silveira, & Taras, 2013). An external locus of control has also been implicated in the prediction of Internet abuse at work (in the form of shopping, searching for non-work related information, and communicating with friends) (Chen, Ross, & Yang, 2011).
These findings (Askew et al, 2014; Chen et al., 2011; Cheng et al., 2014, Sheikh et al., 2015; Tennakoon et al., 2013) provide valuable insight into general factors likely to influence cyberloafing. However, identifying the individual difference factors that contribute to an individual’s cyberloafing, and the processes involved in that behaviour, might further inform corporate approaches to managing this behaviour, and facilitate means to reduce existing or future behaviour. The role of dark characteristics in CWBs is well-established (Grijalva & Newman, 2015; O’Boyle, Forsyth, Banks, & McDaniel, 2012), yet the application of these has not extended to the rapidly changing web connected workplace, or to cyberloafing behaviours that may in fact lack the harmful intent associated with traditional counterproductive workplace behaviours. The aim of this research was therefore to investigate whether dark personality characteristics predict an individual’s cyberloafing behaviour in a vocational context, and the processes by which this occurs.
The Dark Triad
Spector and Fox (2005) propose that personality factors (particularly those associated with emotional reactivity) play a role in acts of counterproductive behaviour. In line with this, it has been theorised that individual differences such as personality may play a key role in cyberloafing (Mastrangelo, Everton, & Jolton, 2006). Indeed, when controlling for age and gender, the Big 5 personality traits explain significant variance in cyberloafing, with less emotional stability, less conscientiousness, and greater extraversion associated with cyberloafing (Jia, Jia, & Karau, 2013). However, cyberloafing has yet to be considered in the context of ‘dark’ personality traits. This represents a substantial gap in the cyberloafing literature, given the characteristics associated with Dark Triad traits.
The Dark Triad of personality describes the subclinical manifestations of three socially aversive personality traits: psychopathy, narcissism, and Machiavellianism (Paulhus & Williams, 2002). The concept of the ‘successful psychopath’ has drawn considerable interest with high levels of subclinical psychopathy evident in many executives (Babiak, Neumann, & Hare, 2010). However, the callousness (Levenson, Kiehl, & Fitzpatrick, 1995), impulsivity (Jones & Paulhus, 2011), and lack of empathy (Grieve & Panebianco, 2013) that these individuals possess can also be problematic. Narcissists exhibit socially extraverted characteristics, and often make a good first impression (Holtzman, Vazire, & Mehl, 2010), but their feelings of grandiosity, superiority, and a sense of entitlement (Emmons, 1987), mean that people’s opinions of narcissistic individuals sour over time as their true nature emerges (Rauthmann, 2012). Machiavellianism involves self-interest, ruthlessness and manipulation (Zettler & Solga, 2013). In line with their self-interest, Machiavellians are goal-focused and willing to do anything it takes in order to achieve their goals, even at the cost of manipulating others (Wu & Lebreton, 2011).
Links between the Dark Triad and CWBs are evident (e.g. Grijalva & Newman, 2015; O’Boyle, Forsyth, Banks, & McDaniel, 2012). For example, in two studies, a meta-analysis and an international primary data collection, Grijalva and Newman examined the relationship between narcissism and counterproductive workplace behaviours. Narcissism was a useful predictor of CWBs beyond the Big 5 traits because of a suppressor effect, whereby the unique characteristics of narcissism were particularly strong predictors of counterproductive behaviours. Furthermore, the narcissism—CWB relationship was weaker for cultures with higher levels of in-group collectivism. Given the nature of these Dark Triad traits, relationships with problematic behaviour in the workplace are not surprising. Yet to date, the relationship between the Dark Triad traits and cyberloafing behaviour has not been investigated.
A Deceptive Disposition
A potential relationship between the Dark Triad and a technology-based form of counterproductive behaviour is intuitive. However previous research has also implicated an individual’s perceived ability to deceive (PATD) in the likelihood that they will engage in counterproductive behaviours in the workplace (Schneider & Goffin, 2012). Schnieder and Goffin (2012) defined PATD as perception of the extent to which you can successfully deceive others without such deception being detected. Interestingly, the ability for PATD to predict CWB was incremental to that of personality predictors typically associated with CWB (Schnieder & Goffin, 2012). Consistent with the link between PATD and counterproductive workplace behaviours, perceptions of the ability to “get away with” cyberloafing are associated with intentions to cyberloaf (Askew et al., 2014; Cheng et al., 2014). Importantly, the Dark Triad is related to the perceived ability to deceive (Giammarco, Atkinson, Baughman, Veselka, & Vernon, 2013), with 21.6% of variance in perceived ability to deceive explained by the Dark Triad. Machiavellianism had the majority of the predictive power in the model.
Machiavellianism is characterised by deception and manipulation (Christie & Geis, 1970). The dominant association between Machiavellianism and perceived ability to deceive was explained in light of Machiavellians’ self-concept as a more successful deceiver than the average person; perhaps as a result of more frequent involvement in deceptive behaviour (Giammarco et al., 2013). Based on this premise, and given the PATD—counterproductive workplace behaviour relationship (Schneider & Goffin, 2012), it seems possible that Machiavellians consider their ability to deceive prior to engaging in undesirable behaviour, and cyberloaf when they believe they can get away with it.
Narcissistic Personality Disorder has been linked to deception due to the Narcissist’s need for self-enhancement (Ford, King, & Hollender, 1988). The narcissist’s sense of entitlement also facilitates an attitude of ‘not having to play by the rules’, which can result in lying (Ford et al., 1988). Narcissists’ grandiose perception of their abilities (Raskin & Terry, 1988) may influence the belief that they are capable of deception. Moreover, their attitude that rules do not apply to them and need for self-enhancement may also bolster the belief that they can deceive through lying; therefore they might engage in undesirable cyberloafing behaviour if they believe they can get away with it and can lie to maintain a positive reputation.
Psychopathy can be conceptualised as comprising an arrogant and deceitful interpersonal style, deficient affective experience, and impulsive and irresponsible behaviours (Cooke & Michie, 2001). Given their deceitful interpersonal style, it is unsurprising that individuals demonstrating higher levels of psychopathy also demonstrate a greater perceived ability to deceive (e.g. Giammarco et al., 2013), and presumably this would be associated with greater counterproductive workplace behaviours. However, their deficient affective processing and irresponsible behavioural style (Cooke & Michie, 2001) combined with a lack of concern for social norms (Hare, 1996) suggests that they will act regardless of their perceived ability to deceive.
The Current Research
We propose that because of their cunning and self-serving nature (e.g., Christie & Geis, 1970; Hare, 1996; Raskin & Terry, 1988), individuals exhibiting the Dark Triad traits should be more likely to engage in cyberloafing behaviours if they believe in their ability to engage in deception in the workplace. Put simply, such individuals will engage in cyberloafing behaviour in the workplace more readily if they think they can get away with it. In order to provide a nuanced examination of the relationship between personality and cyberloafing, we therefore tested the possible mediating influence of ‘perceived ability to deceive’.
Building on the existing literature demonstrating links between the Dark Triad traits and CWBs (Grijalva & Newman, 2015; O’Boyle, Forsyth, Banks, & McDaniel, 2012), and extending examination of personality and cyberloafing (e.g. Jia et al., 2013) to the Dark Triad traits, the current study presented a model to be evaluated using path analysis. As noted, psychopathy is characterised by lying and deceit in interpersonal interactions (Cooke & Michie, 2001). Machiavellianism is associated with manipulating and deceiving others (Christie & Geis, 1970). Grandiose narcissists have over-inflated perceptions of their abilities in general (Raskin & Terry, 1988), therefore theoretically including their ability to deceive.
It was therefore hypothesised that psychopathy, Machiavellianism and grandiose narcissism would significantly relate to perceived ability to deceive, which would be significantly associated with cyberloafing. Further, psychopathy is associated with low conscientiousness (Grieve, 2012), and low conscientiousness is related to cyberloafing (Jia et al., 2013). Thus in addition to the relationship to PATD, it was predicted that psychopathy would also be directly related to cyberloafing.
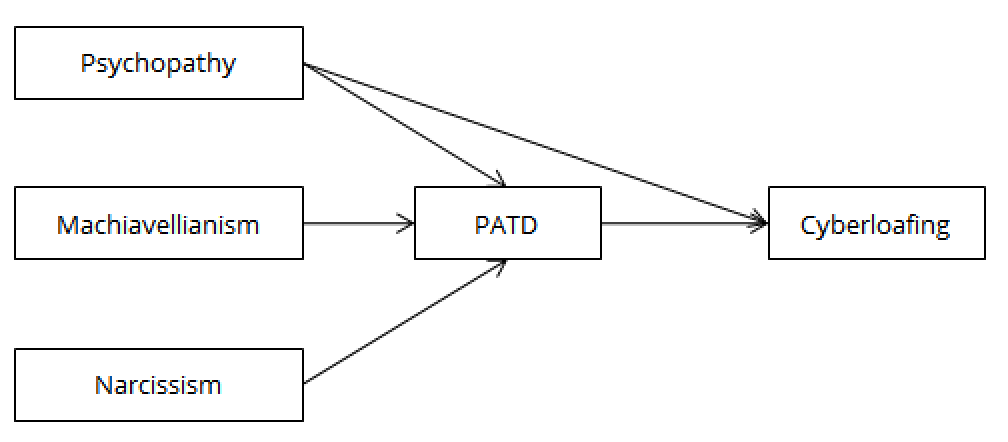
Figure 1. Proposed model of the relationship between the Dark Triad traits, perceived ability to deceive and cyberloafing.
Method
Participants
The sample (N = 273) was predominantly female (80%), with an average age of 28.12 years (SD = 10.65 years). The only selection criterion was that participants were either currently or formerly formally employed. Respondents were recruited via posters, emails, and social media posts seeking participants for an anonymous online survey examining personality in the workplace; with the opportunity to win a $100.00 gift voucher. The majority of participants were employed either fulltime (40.7%) or on a casual basis (37.3%), followed by permanent part-time (18.3%), on contract (3.0%), or in a job sharing role (0.7%). Participants reported a number of occupational categories: salesperson (25.6%); professional (22%); clerical/administration (13.2%); management (7.7%); community workers (7%); technical and trade (3.3%); labourer (2.6%) and “other” (18.7%).
Measures
Measures of psychopathy, grandiose narcissism, Machiavellianism, cyberloafing, and perceived ability to deceive were administered. For each scale the sum of responses was calculated, with some items reverse scored as necessary. For means and internal reliabilities for each scale please refer to Table 1.
Psychopathy. The primary psychopathy scale (Levenson et al., 1995) measured psychopathy. The scale includes 16 items (e.g. “Success is based on survival of the fittest; I am not concerned about the losers”; “In today’s world, I feel justified in doing anything I can get away with to succeed”; “Looking out for myself is my top priority”). Participants responded on a four point Likert scale, with responses options 1= disagree strongly; 2= disagree somewhat; 3= agree somewhat; 4= agree strongly.
Grandiose Narcissism. Grandiose narcissism was measured with an adapted version of the Narcissistic Personality Inventory (NPI, Raskin & Terry, 1988). Kubarych, Deary and Austin (2004) used confirmatory factor analysis to identify the most strongly loading items of the NPI (according to criterion factor loading of .35). Using this cutoff of factor loadings of .35 or above, twenty-three items were selected from Raskin and Terry’s (1988) 40-item NPI. These 23 items were included in the current research. Individuals were asked to indicate their level of agreement with each item (e.g. “I have a natural talent for influencing people”; “I know that I am good because everyone keeps telling me so”; “I like to be the centre of attention”) on a five point Likert style scale, with responses ranging from 1= strongly disagree to 5= strongly agree.
Machiavellianism. The 20 item Mach IV (Christie & Geis, 1970) was used. Sample items include “Never tell anyone the real reason you did something unless it is useful to do so; “It is safest to assume that all people have a vicious streak and it will come out when they are given a chance”; “Anyone who completely trusts anyone else is asking for trouble”, with participants indicating the extent to which they agree with each item on a five point Likert style scale, with responses ranging from 1= strongly disagree to 5= strongly agree.
Cyberloafing. Cyberloafing was measured using the ‘technology’ items from the Time Banditry Questionnaire (Brock et al., 2013). Participants report the frequency of each of 7 items (e.g. “I spend time on the Internet for reasons not related to work”; “I receive non-work-related e-mail at work”; “I check non-work-related email at work”) using a five point Likert style scale ranging from 1= never to 5= always.
Perceived Ability to Deceive. We used Schneider and Goffin’s (2012) 6-item scale, as modified by Grieve and Hayes (2013). This scale assesses perceived ability (e.g. “I would be better than the average person at lying on my resume without getting caught”) and perceived difficulty (e.g. “How difficult would it be for you to overstate some of your work-related experience in a job interview without getting caught?”) in deceiving in the workplace. Likert responses are used, with the anchors strongly disagree and strongly agree used for the perceived ability items, and the anchors extremely difficult and extremely easy for the perceived difficulty items.
Design and Procedure
A cross-sectional design was used, employing path analysis using AMOS (Arbuckle, 2014). Path analysis is a form of multivariate analysis that illustrates relationships between multiple variables using a path diagram, enabling the analysis of relationships between a number of variables in a model (de Vaus, 2014). Ethical approval was given from the institutional board. Data was collected online (using LimeSurvey), with informed consent obtained prior to the commencement of the survey. After completing the survey, participants could follow a link to a separate web page where they could enter their details to go into the prize draw.
Results
Descriptive Statistics and Correlations
Descriptive statistics and bivariate correlations for all measures are presented in Table 1. Mean scores and variability were similar to those seen in previous research (Grieve & Hayes, 2013; Levenson, Kiehl, & Fitzpatrick, 1995; Rauthmann, 2013). Table 1 also displays internal consistency, and shows that values of Cronbach’s α ranged from good to excellent for all measures.
The Dark Triad traits were significantly related to perceived ability to deceive. The relationships between primary psychopathy and PATD, and Machiavellianism and PATD were strong and significant, while the relationship between grandiose narcissism and PATD was moderate and significant. Machiavellianism was strongly correlated with primary psychopathy. The relationship between PATD and cyberloafing was significant.
Table 1. Descriptive Statistics and Bivariate Correlations (with Cronbach’s α in diagonals).
|
|
M |
SD |
PP |
M |
GN |
PATD |
Cyber |
|
Primary Psychopathy |
26.23 |
6.68 |
( .825) |
|
|
|
|
|
Machiavellianism |
51.40 |
8.78 |
.51*** |
(.744) |
|
|
|
|
Grandiose Narcissism |
61.00 |
14.28 |
.40*** |
.25*** |
(.905) |
|
|
|
PATD |
15.19 |
5.58 |
.40*** |
.42*** |
.30*** |
(.767) |
|
|
Cyberloafing |
18.96 |
7.84 |
.19** |
.15* |
.13* |
.21a |
(.903) |
|
Note: PP=Primary Psychopathy;M=Machiavellianism;GN= Grandiose Narcissism; PATD=Perceived ability to deceive;Cyber=Cyberloafing *p<.05;**p<.01;***p<.001; ap=.001
|
|||||||
Model Evaluation
The chi-square statistic (χ2), comparative fit index (CFI), normed fit index (NFI) and the root-mean-square error of approximation (RMSEA) were used to determine the overall model fit. A hypothesised model may be considered a relatively good fit with the observed data if CFI > 0.90, NFI > 0.90 and RMSEA < 0.08 (Hu & Bentler, 1999). The hypothesised model yielded a χ2 = .335, p = .846, CFI = 1.00, NFI = .999, RMSEA = .000, indicating that the model was very well fitting (see Figure 2). Unsurprisingly, Machiavellianism had the highest correlation with PATD, r (n = 273) = .29, p <.001. Both primary psychopathy and grandiose narcissism were also significantly related to PATD, r (n = 273) = .19, p =.004, and r (n = 273) = .16, p = .007, respectively. Psychopathy showed a direct association with cyberloafing, r (n =273) = .13, p = .046, and PATD was a significantly associated with cyberloafing, r (n =273) = .15, p = .016. Therefore, within this model, it appears that PATD partially mediates the relationship between the Dark Triad and cyberloafing, while psychopathy also has a direct relationship with cyberloafing.
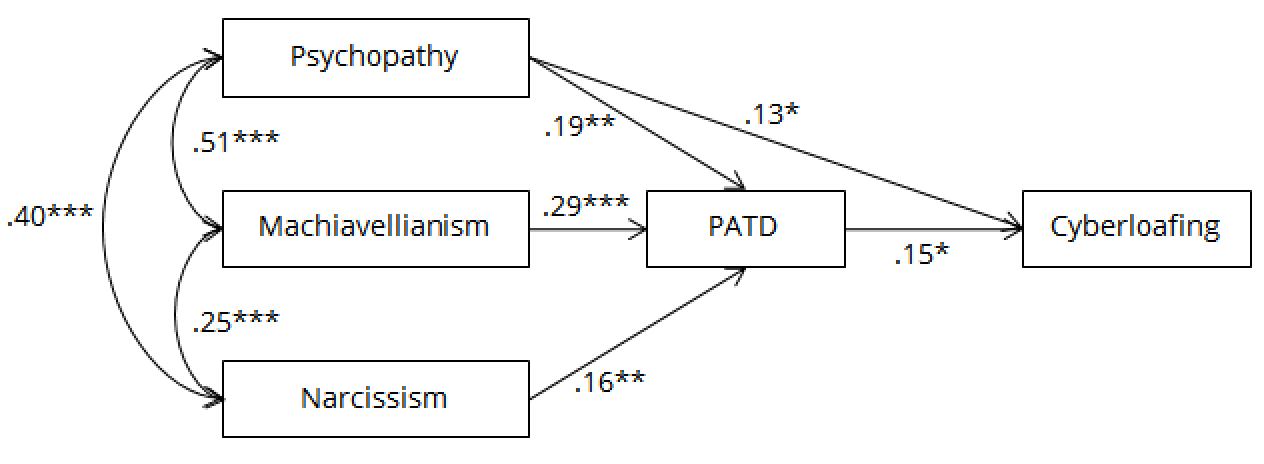
Figure 2. Final model of the relationship between the Dark Triad traits,
perceived ability to deceive and cyberloafing.*p<.05;**p<.01;***p<.001.
Discussion
This research investigated the influence of perceived ability to deceive as a mediator of the relationship between the Dark Triad personality traits and cyberloafing in a vocational context. The hypothesised model was supported; suggesting that individuals possessing high levels of psychopathy, Machiavellianism and grandiose narcissism are more likely to engage in cyberloafing behaviours when they believe they will be able to get away with them.
The mechanisms at play here may be related but different for each of the traits. For example, Machiavellians, characterised as skilled and practiced strategists and manipulators (Jones & Paulhus, 2009), would know it is important to think about what they can get away with. Additionally, Machiavellians care about maintaining a positive impression (Sherry, Hewitt, Besser, Flett, & Klein, 2006). As such, it is unsurprising that Machiavellians know the limits of their manipulations and use these to their advantage. For narcissists, a simpler explanation may suffice: narcissists have an inflated view of the self and their abilities (Paulhus & Williams, 2002). Therefore this self-confidence may extend to the belief that they can get away with deception at work (even if they do not possess necessary skills or experience, as Machiavellians do).
Further, as predicted, our findings suggest that individuals high in subclinical psychopathy will still engage in some cyberloafing behaviours regardless of their perceived ability to deceive. This behaviour may be attributed to their low conscientiousness (Grieve, 2012; Paulhus & Williams, 2002). For individuals exhibiting psychopathic traits, low conscientiousness can manifest as lacking a sense of responsibility, lacking forethought or deliberation, and difficulty with self-discipline required to see a task through to completion, despite boredom and distractions; such characteristics may result in antagonistic behaviour (Widiger & Lynam, 1998). Subclinical psychopaths demonstrate greater risk-taking behaviour and impulsivity (Jones & Paulhus, 2011), and emotional deficits (Grieve & Panebianco, 2013). With impulsivity and orientation toward short-term rewards it is likely that people with high levels of these traits do not bother weighing up whether they will be caught out, or do not carefully consider potential consequences of being caught, thus contributing to their cyberloafing behaviour.
Cyberloafing has been empirically differentiated from traditional counterproductive workplace behaviour, as it lacks a conscious harmful intent (Metin et al., 2016). Whilst unhelpful and costly when widespread, to some degree cyberloafing can occur without great detriment to an organisation, even positively impacting employees (Lim & Chen, 2012), which may have a positive flow on effect to their work productivity. However it is possible that individuals possessing dark and problematic personality types may manifest cyberloafing with these more negative intentions. This may be expressed as an employee spending a greater proportion of their work time cyberloafing, or engaging in cyberloafing behaviours that may be detrimental to an organization’s resources (e.g. downloading content may result in slower network performance or viruses on company devices).
Importantly, perceived ability to deceive was a solid mediator within the model. Given the relationship between perceived ability to deceive and cyberloafing, and the size of this relationship relative to the Dark Triad predictors, it is possible that PATD is the real mechanism by which cyberloafing behaviour might be manipulated. Like other more detrimental and intentionally harmful counterproductive workplace behaviours (Schneider & Goffin, 2012), PATD may underlie cyberloafing as individuals are willing to engage in rebellious behaviours if they perceive a low likelihood of being caught. Given the individual and personal use of online devices, it is possible that employees perceive ease in ‘getting away with’ cyberloafing. Furthermore, the belief that cyberloafing is an acceptable workplace behaviour (Lim & Chen, 2012) may also influence an individual’s PATD, possibly explaining the high prevalence of this behaviour.
Conceptually, the current findings add depth to previous research that has examined the relationship between the Dark Triad and counterproductive workplace behaviours, by highlighting the contribution of an individual’s perceived ability to deceive. This finding suggests that specifically it is the deceptive nature of these dark traits that plays a key role in whether an individual will engage in technologically based counterproductive workplace activity.
Devices with Internet access are a common feature in many workplaces; furthermore, research indicates that the majority of computer using workers report using the Internet for personal purposes whilst at work (e.g. Garrett & Danziger, 2008; Page, 2015: Sheikh et al., 2015). Consequently, on an applied level, the importance of the present research lies in its potential to inform policy that might reduce cyberloafing behaviour, such that the productivity of workplaces may be maximised, and the costs associated with cyberloafing reduced. The preliminary nature of our findings mean that exercising caution when tailoring tactics to manage this counterproductive behaviour is essential. Nonetheless, our data indicate that due to the important role played by PATD, employers would be wise to consider stressing accountability, highlighting consequences, and increasing perceptions that counterproductive behaviour will be caught. For example, if a workplace promoted a policy that all web based activity would be recorded and monitored, employees may be less likely to ‘surf the internet’ for non-work reasons (for example, social media sites or online shopping) as they would be under the impression that the activity would not go unnoticed. This, combined with emphasising the personal costs of being caught, may serve as useful deterrents.
It is essential to consider the current findings within the context of the ever-changing digital landscape. While computers are still regularly used devices within an organisational context, the ever-increasing popularity of smartphones and tablet devices allows users to connect to the Internet anywhere and anytime. Research has shown that most smartphone users admit to using their mobile devices for personal purposes within the workplace (Jamaluddin, Ahmad, Alias, & Simun, 2015). Given the personal nature of mobile device use, which would be harder for an organisation to monitor, it is possible that employees perceive a greater ability to engage in cyberloafing behaviours without being caught. Taken together with the current findings, suggesting the key role played by PATD, use of mobile devices may be associated with increased cyberloafing in the workplace. However a further consideration is that company-provided smartphones can lead to employee hyperconnectivity, where employees perceive pressure to be constantly available and responsive (Obushenkova & Plester, 2015). Perhaps the modern workplace blurs the traditional separation between work and home life, with crossover between the personal and organisational spheres due to constant connectivity.
Limitations and Recommendations for Future Research
The measurement of cyberloafing via self-report may be flagged as a limitation of the present study. It is possible that self-reports (rather than behavioural measures) do not accurately reflect cyberloafing behaviour, and individuals may respond in a socially desirable manner. However, participants were informed that the answers they provided would remain completely anonymous, thus honest responses should have been maximised. Previous research investigating cyberloafing has also relied on self-reports (e.g. Askew et al., 2014; Cheng et al., 2014). As such we suggest that the findings presented here reflect a reasonably accurate representation of the participants’ cyberloafing behaviour.
Even so, future research may take the next step of incorporating a behavioural measure of cyberloafing activity. This might be managed through the use of a ‘big data’ approach; monitoring participants’ online activity to measure cyberloafing across all the devices used by the participant in the workplace. Further, a comparison of self-reports and behavioural measures of cyberloafing would also provide insight into how this aspect of time banditry might be best operationalised. However, the ethical implications of this kind of access to information warrant substantial consideration.
Investigation of any cyberloafing subtypes may also reveal under what circumstances cyberloafing is most counterproductive and costly. This approach might better inform workplace policy. For example, social cyberloafing (e.g. contacting friends on social media, Andreassen, Torsheim, & Pallesen, 2014) may have differential effects than more targeted cyberloafing (e.g. online banking) behaviour. It is also worth noting that in some cases, the line between work and cyberloafing may not always be distinct. For example, in cyber-assisted social interactions, where the majority of the exchange is not work-related, but some work-related issues are addressed (Hislop & Axtell, 2011). Similarly, workplace gamification may also lead to a rise in non-work related use of technology in the office; changing the way we look at ‘work’ and ‘play’ (Oravec, 2015). Finally, short breaks from work to access the Internet for personal use can improve productivity (Page, 2015).
The participants in this study represent employees from a variety of sectors and job types. By sampling a broad range of current or previously employed persons it is possible to examine the ‘big picture’ of how cyberloafing operates in the workplace. However, acknowledging that cyberloafing behaviours may vary substantially between different job types, our results may not be representative, and further investigation is recommended. For example, cyberslacking is a behaviour particularly relevant to office workers where employees are often stationed in front of computers and other work-intended devices, therefore the results seen here may not be consistent through the entire sample, which also includes salespeople, community workers, and tradespeople. It is also possible that behaviours considered cyberloafing might be detrimental in some job contexts, where they result in distraction and lost productivity, yet beneficial in others, where they help to enhance wellbeing and creativity, and decrease anxiety (Beugre & Kim, 2006). Therefore it is recommended that future research more closely examine this issue for workers in different sectors and job types. A final consideration is that the current sample was largely female. As some sex differences in Dark Triad traits exist (e.g. Grieve & Panebianco, 2013), future studies might take gender into account as an additional variable. In the meantime, it is important not to overgeneralise our findings.
Conclusion
Cyberloafing is a potentially distracting and costly counterproductive behaviour, commonly committed in vocational contexts. Investigation of its antecedents is thus warranted. We examined a model of personality and cyberloafing that revealed the vital role of psychopathy and perceived ability to deceive in determining counterproductive work behaviours. It is suggested that in order to reduce cyberloafing, workplaces might implement strategies based on reducing employees’ perceived ability to deceive, and increasing the personal salience of costs if caught: employees might then doubt their ability to get away with, or be concerned with consequences of, cyber-slacking on the job.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
Copyright © 2017 Emily Lowe-Calverley, Rachel Grieve


