Criteria and rules for privacy management prior to self-disclosures on social network sites (SNSs)
Vol.15,No.2(2021)
This study applied a novel theoretical framework of communication privacy management theory (CPM) to examine how criteria such as context, culture, and privacy motivation influence information boundary coordination rules (boundary linkage, ownership, and permeability rules) on Facebook. In particular, the current study has made an initial attempt to examine how the CPM’s boundary coordination rules are related as a process to make disclosures; how to manage connections (boundary linkage rule) and how to regulate information flow (boundary ownership rule) influence how much to disclose (boundary permeability rule) on Facebook. The study recruited active Facebook users (N = 397, Mage = 20.68, SDage = 3.63) in a large northeastern US university to complete an online survey in fall 2015. A structural equation model was proposed to test the hypothesized paths among variables proposed to build the model. Findings reveal that context (perceptions of boundless communication) and privacy motivation led to the coordination of strict boundary ownership rules for disclosure on Facebook. The context and privacy motivation however differ in their influence on the coordination of boundary linkage rule; the more individuals felt the greater need for privacy, the less likely that they attempted to create connection whereas perceiving a lack of boundaries in communication did not influence the pursuance of future connections. The culture (the goal of using Facebook for making friends) did not predict either the coordination of the boundary linkage rule or the boundary ownership rule. As expected, the coordination of the boundary linkage rule positively influenced the coordination of the permeability rule (depth of disclosure), but the coordination of the boundary ownership rule negatively influenced it. The statistical test suggested an addition of a path from the boundary ownership to the boundary linkage rule, generating an implication that the regulation of information flow (privacy desire) and managing networks (connection desire) work together in disclosure decisions. Implications of the findings on different roles of privacy motivation and context in forming privacy management and disclosure tendency are discussed to advance the modeling of comprehensive information boundary management for disclosures on SNSs.
boundary permeability rule; boundary ownership rule; boundary linkage rule; context; need for privacy; disclosure; social network sites (SNSs); communication privacy management theory (CPM)
SoeYoon Choi
The State University of New York at New Paltz, New Paltz, New York
SoeYoon Choi is an Assistant Professor of Communication in The State University of New York at New Paltz. Her research revolves around privacy, self-disclosure, technology affordance, and the impact of psychological distance on emotional disclosure on social media.
Altman, I. (1975). The environment and social behavior. Wadsworth.
Bazarova, N. N. (2012). Public intimacy: Disclosure interpretation and social judgments on Facebook. Journal of Communication, 62(5), 815–832. https://doi.org/10.1111/j.1460-2466.2012.01664.x
Beer, D. (2008). Social network(ing) sites…revisiting the story so far: A response to danah boyd & Nicole Ellison. Journal of Computer-Mediated Communication, 13(2), 516–529. https://doi.org/10.1111/j.1083-6101.2008.00408.x
Betancourt, H., & López, S. R. (1993). The study of culture, ethnicity, and race in American psychology. American Psychologist, 48(6), 629–637. https://doi.org/10.1037/0003-066X.48.6.629
boyd, d. (2008). Facebook’s privacy trainwreck: Exposure, invasion, and social convergence. Convergence: The International Journal of Research into Media Technologies, 14(1), 13–20. https://doi.org/10.1177/1354856507084416
boyd, d. (2010). Social network sites as networked publics: Affordances, dynamics, and implications. Routledge.
boyd, d. m., & Ellison, N. B. (2007). Social network sites: Definition, history, and scholarship. Journal of Computer-Mediated Communication, 13(1), 210–230. https://doi.org/10.1111/j.1083-6101.2007.00393.x
Chelune, G. J. (1975). Self-disclosure: An elaboration of its basic dimensions. Psychological Reports, 36(1), 79–85. https://doi.org/10.2466/pr0.1975.36.1.79
Chen, H-T., & Chen, W. (2015). Couldn’t or wouldn’t? The influence of privacy concerns and self-efficacy in privacy management on privacy protection. Cyberpsychology, Behavior, and Social Networking, 18(1), 13–19. https://doi.org/10.1089/cyber.2014.0456
Child, J. T., & Agyeman-Budu, E. A. (2010). Blogging privacy management rule development: The impact of self-monitoring skills, concern for appropriateness, and blogging frequency. Computers in Human Behavior, 26(5), 957–963. https://doi.org/10.1016/j.chb.2010.02.009
Child, J. T., Haridakis, P. M., & Petronio, S. (2012). Blogging privacy rule orientations, privacy management, and content deletion practices: The variability of online privacy management activity at different stages of social media use. Computers in Human Behavior, 28(5), 1859–1872. https://doi.org/10.1016/j.chb.2012.05.004
Child, J. T., Pearson, J. C., & Petronio, S. (2009). Blogging, communication, and privacy management: Development of the blogging privacy management measure. Journal of the American Society for Information Science & Technology, 60(10), 2079–2094. https://doi.org/10.1002/asi.21122
Child, J. T., & Petronio, S. (2011). Unpacking the paradoxes of privacy in CMC relationships: The challenges of blogging and relational communication on the Internet. In K. B. Wright & L. M. Webb (Eds.), Computer-mediated communication in personal relationships (pp. 21–40). Peter Lang.
Child, J. T., Petronio, S., Agyeman-Budu, E. A., & Westermann, D. A. (2011). Blog scrubbing: Exploring triggers that change privacy rules. Computers in Human Behavior, 27(5), 2017–2027. https://doi.org/10.1016/j.chb.2011.05.009
Child, J. T., & Starcher, S. C. (2016). Fuzzy Facebook privacy boundaries: Exploring mediated lurking, vague-booking, and Facebook privacy management. Computers in Human Behavior, 54, 483–490. https://doi.org/10.1016/j.chb.2015.08.035
Christofides, E., Muise, A., & Desmarais, S. (2009). Information disclosure and control on Facebook: Are they two sides of the same coin or two different processes? CyberPsychology & Behavior, 12(3), 341–345. https://doi.org/10.1089/cpb.2008.0226
Dhir, A., Kaur, P., & Rajala, R. (2018). Why do young people tag photos on social network sites? Explaining user intentions. International Journal of Information Management, 38(1), 117–127. https://doi.org/10.1016/j.ijinfomgt.2017.07.004
Doyal, L., & Gough, I. (1991). A theory of human need. MacMillan.
Ellison, N. B., Steinfield, C., & Lampe, C. (2007). The benefits of Facebook “friends:” Social capital and college students’ use of online social network sites. Journal of Computer-Mediated Communication, 12(4), 1143–1168. https://doi.org/10.1111/j.1083-6101.2007.00367.x
Ellison, N. B., Vitak, J., Steinfield, C., Gray, R., & Lampe, C. (2011). Negotiating privacy concerns and social capital needs in a social media environment. In S. Trepe & L. Reineke (Eds.), Privacy online: Perspectives on privacy and self-disclosure in the social web (pp. 19–32). Springer.
Frampton, B. D., & Child, J. T. (2013). Friend or not to friend: Coworker Facebook friend requests as an application of communication privacy management theory. Computers in Human Behavior, 29(6), 2257–2264. https://doi.org/10.1016/j.chb.2013.05.006
Hooper, D., Coughlan, J., & Mullen, M. R. (2008). Structural equation modeling: Guidelines for determining model fit. Electronic Journal of Business Research Methods, 6(1), 53–60. http://doi.org/10.21427/D7CF7R
Jin, S.-A. A. (2012). “To disclose or not to disclose, that is the question:” A structural equation modeling approach to communication privacy management in e-health. Computers in Human Behavior, 28(1), 69–77. https://doi.org/10.1016/j.chb.2011.08.012
Joinson, A. N. (2008). ‘Looking at’, ‘looking up’ or ‘keeping up with’ people? Motives and uses of Facebook. In CHI '08: Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (pp. 1027–1036). ACM. https://doi.org/10.1145/1357054.1357213
Joinson, A. N., Reips, U.-D., Buchanan, T., & Paine Schofield, C. B. (2010). Privacy, trust and self-disclosure online. Human-Computer Interaction, 25(1), 1–24. https://doi.org/10.1080/07370020903586662
Jourard, S. M. (1971). Self-disclosure: An experimental analysis of the transparent self. Wiley-Interscience.
Kaya, N., & Weber, M. J. (2003). Cross-cultural differences in the perception of crowding and privacy regulation: American and Turkish students. Journal of Environmental Psychology, 23(3), 301–309. https://doi.org/10.1016/S0272-4944(02)00087-7
Lawton, M. P., & Bader, J. (1970). Wish for privacy by young and old. Journal of Gerontology, 25(1), 48–54. https://doi.org/10.1093/geronj/25.1.48
Lewis, K., Kaufman, J., & Christakis, N. (2008). The taste for privacy: An analysis of college student privacy settings in an online social network. Journal of Computer-Mediated Communication, 14(1), 79–100. https://doi.org/10.1111/j.1083-6101.2008.01432.x
Litt, E. (2013). Understanding social network site users’ privacy tool use. Computers in Human Behavior, 29(4), 1649–1656. https://doi.org/10.1016/j.chb.2013.01.049
Litt, E., & Hargittai, E. (2016). “Just cast the net, and hopefully the right fish swim into it”: Audience management on social network sites. In CSCW '16: Proceedings of the 19th ACM Conference on Computer-Supported Cooperative Work & Social Computing (pp. 1488–1500). ACM. https://doi.org/10.1145/2818048.2819933
Long, C. R, & Averill, J. R. (2003). Solitude: An exploration of benefits of being alone. Journal for the Theory of Social Behavior, 33(1), 21–43. https://doi.org/10.1111/1468-5914.00204
Marwick, A. E., & boyd, d. (2011). I tweet honestly, I tweet passionately: Twitter users, context collapse, and the imagined audience. New Media & Society, 13(1), 114–133. https://doi.org/10.1177/1461444810365313
Metzger, M. J. (2007). Communication privacy management in electronic commerce. Journal of Computer-Mediated Communication, 12(2), 335–361. https://doi.org/10.1111/j.1083-6101.2007.00328.x
Mohajan, H. K. (2017). Two criteria for good measurements in research: Validity and reliability. Annals of Spiru Haret University Economic Series, 17(4), 59–82. https://doi.org/10.26458/1746
Mousavizadeh, M., & Kim, D. (2015, August). A study of the effect of privacy assurance mechanisms on self-disclosure in social networking sites from the view of protection motivation theory [Paper presentation]. 21st Americas Conference on Information System (AMCIS 2015), Fajardo, Puerto Rico.
Parks, M. R., & Floyd, K. (1996). Making friends in cyberspace. Journal of Computer-Mediated Communication, 1(4), 80–97. https://doi.org/10.1111/j.1083-6101.1996.tb00176.x
Petronio, S. (2002). Boundaries of privacy: Dialectics of disclosure. State University of New York Press.
Petronio, S., & Sargent, J. (2011). Disclosure predicaments arising during the course of patient care: Nurses’ privacy management. Health Communication, 26(3), 255–266. https://doi.org/10.1080/10410236.2010.549812
Pierson, J. (2012). Online privacy in social media: A conceptual exploration of empowerment and vulnerability. Communication & Strategies, 88, 99–120. https://ssrn.com/abstract=2374376
Rohner, R. P. (1984). Toward a conception of culture for cross-cultural psychology. Journal of Cross-Cultural Psychology, 15(2), 111–138. https://doi.org/10.1177/0022002184015002002
Stutzman, F., & Kramer-Duffield, J. (2010). Friends only: Examining a privacy-enhancing behavior in Facebook. In CHI '10: Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (pp. 1553–1562). ACM. https://doi.org/10.1145/1753326.1753559
Stutzman, F., Gross, R., & Acquisti, A. (2012). Silent listeners: The evolution of privacy and disclosure on Facebook. Journal of Privacy and Confidentiality, 4(2), 7–41. https://doi.org/10.29012/jpc.v4i2.620
Terwee, C. B., Bot, S. D. M., de Boer, M. R., van der Windt, D. A. W. M., Knol, D. L., Dekker, J., Bouter, L. M., & de Vet, H. C. W. (2007). Quality criteria were proposed for measurement properties of health status questionnaires. Journal of Clinical Epidemiology, 60(1), 34–42. https://doi.org/10.1016/j.jclinepi.2006.03.012
Treem, J. W., & Leonardi, P. M. (2013). Social media use in organizations: Exploring the affordances of visibility, editability, persistence, and association. Annals of the International Communication Association, 36(1), 143–189. https://doi.org/10.1080/23808985.2013.11679130
Trepte, S., & Reinecke, L. (2013). The reciprocal effects of social network site use and the disposition for self-disclosure: A longitudinal study. Computers in Human Behavior, 29(3), 1102–1112. https://doi.org/10.1016/j.chb.2012.10.002
Ur, B., & Wang, Y. (2013). A cross-cultural framework for protecting user privacy in online social media. In WWW '13 Companion: Proceedings of the 22nd International Conference on World Wide Web (pp. 755–762). ACM. https://doi.org/10.1145/2487788.2488037
Utz, S., & Krämer, N. C. (2009). The privacy paradox on social network sites revisited: The role of individual characteristics and group norms. Cyberpsychology: Journal of Psychosocial Research on Cyberspace, 3(2), Article 2. https://cyberpsychology.eu/article/view/4223/3265
Vitak, J. (2012). The impact of context collapse and privacy on social network site disclosures. Journal of Broadcasting & Electronic Media, 56(4), 451–470. https://doi.org/10.1080/08838151.2012.732140
Vitak, J., Blasiola, S., Patil, S., & Litt, E. (2015). Balancing audience and privacy tensions on social network sites. International Journal of Communication Systems, 9, 1485–1504. https://ijoc.org/index.php/ijoc/article/view/3208
Vitak, J., & Kim, J. (Eds.). (2014). “You can’t block people offline”: Examining how Facebook’s affordances shape the disclosure process. In CSCW '14: Proceedings of the 17th ACM Conference on Computer Supported Cooperative Work & Social Computing (pp. 461–474). ACM. https://doi.org/10.1145/2531602.2531672
Waters, S., & Ackerman, J. (2011). Exploring privacy management on Facebook: Motivations and perceived consequences of voluntary disclosure. Journal of Computer-Mediated Communication, 17(1), 101–115. https://doi.org/10.1111/j.1083-6101.2011.01559.x
Yan, D., & Sengupta, J. (2011). Effects of construal level on the price-quality relationship. Journal of Consumer Research, 38(2), 376–389. https://doi.org/10.1086/659755
Yao, M. Z., Rice, R. E., & Wallis, K. (2007). Predicting user concerns about online privacy. Journal of the American Society for Information Science and Technology, 58(5), 710–722. https://doi.org/10.1002/asi.20530
Zlatolas, L. N., Welzer, T., Heričko, M., & Hölbl, M. (2015). Privacy antecedents for SNS self-disclosure: The case of Facebook. Computers in Human Behavior, 45, 158–167. https://doi.org/10.1016/j.chb.2014.12.012
Editorial Record
First submission received:
January 30, 2020
Revisions received:
July 9, 2020
December 14, 2020
Accepted for publication:
February 15, 2021
Editor in charge:
Michael Walrave
Introduction
Making a disclosure on SNSs is an important means to connect with others and to promote social capital (see Ellison et al., 2011 for detailed discussion). At the same time, disclosing about self on such public venues comes with concerns about what to reveal to whom among diverse audiences in the network (Vitak et al., 2015). Therefore, when people post on SNSs, careful considerations should be made about what information they should share with different audiences. A body of research has examined disclosure patterns on SNSs and how it relates to concerns about privacy (Vitak et al., 2015), impression management (Child et al., 2011; Vitak & Kim, 2014), and concerns about mediated lurking (Child & Starcher, 2016). Little research, however, has examined how the simultaneous and competing motivations for connection and information ownership work together to drive disclosure decisions on SNSs.
Disclosure offline involves cooperative efforts between disclosers and recipients to coordinate rules for information boundary management (Petronio, 2002). This explicit negotiation of rules between both parties may help the disclosers reduce uncertainties about disclosure risks such as how the revealed information may be perceived or leaked after disclosures. Disclosure on SNSs should be understood differently from that in dyadic offline interactions because of the affordance of the platform for one-to-many communication that allows for expansive social networking but also may come with a lack of negotiation for mutual rules to protect individuals’ personal information flow. The context of SNSs can drive contrasting motivations for privacy in that it can increase concerns about privacy violations due to unexpected leakage of information as well as benefits for connections to a wide variety of others. These concerns about disclosure costs and benefits are perceptual and can influence how individuals establish strategies for disclosure, including decisions about what to disclose and to whom.
To add empirical and theoretical explanations for how people generate rules for protecting personal information boundaries on SNSs, this study contextualizes privacy boundary management patterns and how they influence individuals’ disclosures. It uses communication privacy management theory (CPM; Petronio, 2002) to propose a conceptual model that describes the procedure for disclosure in terms of how people’s privacy rules are intertwined with context, culture, and motivation prior to disclosures. Privacy boundary management is a process that individuals dynamically negotiate their motivations for privacy protection and openness. The motivation for privacy protection can generate defensive privacy protective patterns, reducing intentions for disclosures on SNSs (Mousavizadeh & Kim, 2015) whereas the drive to connect on SNSs can increase the tendency to reveal (Waters & Ackerman, 2011). The study proposes that the individual drive for regulation (need for privacy) and the social drive for revealing (context and culture) should be treated as comparable predictors for making privacy rules. In doing so, a quantitative model for privacy boundary regulation and disclosure for users of social media (here, Facebook) will be proposed.
Theory of Communication Privacy Management (CPM)
CPM (Petronio, 2002) proposes a rule-based information boundary management system to understand motivations and processes of privacy protection. Disclosing about self is the act of sharing personal information including feelings, thoughts, or opinions with others (Chelune, 1975; Jourard, 1971). The information revealed through disclosure falls within the continuum of personal information. The information can be conceptualized based on the degree of intimacy, but it may not always be considered as private. However, the concept of privacy pertaining to personal information is relative in that people may have different perspectives about what information is private and to what extent (see Petronio, 2002 for discussion). In that sense, CPM provides a framework to understand how people make decisions about personal information boundaries prior to disclosures.
According to CPM, a general goal of privacy management is to protect personal information. CPM focuses on the mechanisms of dialectical tensions between openness and closure. People have the simultaneous desire to make themselves public while pursuing privacy, and disclosure involves their decisions about the extent to which they open up about self to others (Petronio, 2002). Therefore, people need to consider various tensions that influence motives to disclose or withdraw. The privacy goal is met when people manage the dialectical tension to regulate their information flow appropriately for different situations or targets. For example, disclosure on SNSs may come with greater feelings of surveillance than disclosures offline because of the difficulty in anticipating the flow of information. Thus, people should enact disclosures only after conscious assessment of disclosure situations and outcomes.
CPM has been employed to understand the process of disclosing personal information not only in offline but also in online contexts including: e-commerce (Metzger, 2007), blogs (Child et al., 2011; Child et al., 2012), health institutions (Jin, 2012) and social media (Frampton & Child, 2013). These studies reveal that concerns for privacy positively predict information protection motivation and more rigid information boundary management patterns. Beyond the examination of a linear relationship between privacy concerns and information boundary management patterns, this study elaborates the underlying process for privacy rule management and disclosures on SNSs.
Principles of Privacy Management
In explicating mechanisms underlying privacy boundary management, CPM proposes five principles of privacy management regarding when access to personal information is granted or denied (Child & Petronio, 2011; Petronio, 2002). These principles describe the ways in which people claim ownership and control over their information and generate rules to regulate information flow. The first principle states that people consider information to be similar to a commodity and thus desire ownership of their information. The ownership in CPM refers to the perceived rights to declare ownership of private information. The second principle focuses on people’s perceived need and right to control the flow of the information to others. The third principle is that people create rules for information boundary management based on criteria that are important to them (among these criteria are gender, culture, motivation, context, and cost-benefit analyses). The fourth principle describes procedures for how people coordinate collective information boundaries after sharing while individuals regulate the amount (boundary permeability rule), target (boundary ownership rule), and the third target of the disclosures (boundary linkage rule). The fifth and last principle concerns the violation and re-negotiation of boundary regulation rules between information owners and co-owners.
The decision to make disclosures on SNSs can be based largely on principles three and four in that individuals may have a tendency to experiment with boundary management and adjust the boundary according to motivations shaped both by the context and individual privacy desire, which are described further in the next section. In particular, the negotiation of collective information boundaries on SNSs ideally occur based on individuals’ own decisions for how much to reveal (permeability rule), with whom (linkage rule), and how to grant information ownership (ownership rule).
The boundary permeability rule indicates the amount, breadth, and depth of disclosure (Child et al., 2009). When people want rigid control over information, they erect a thick boundary around the information as a way to reduce the possibility that the information is leaked to unwanted others. On SNSs, people may regulate the information flow between themselves and the SNSs either by erecting solid boundary walls or by loosening the flow of information. For instance, in a study that investigated how patients regulate their health-related information posted on the hospital website, Jin (2012) conceptualized the boundary permeability rule as “how much information is able to pass through the boundary after consumers’ private information disclosure to the e-health website” (pp. 70-71). This conceptualization of the boundary permeability rule shows how careful people are about the accessibility to their information from unwanted others. Another study shows that people may regulate permeability of their information by avoiding sharing specific topics about self on blogs, thus limiting information that is available to others (Child & Agyeman-Budu, 2010). In short, the permeability rule can reflect individual tendency to be more or less open.
People may also regulate information boundaries on SNSs in consideration of target audiences. Drawing on CPM, the boundary ownership rule indicates that original disclosers have the right to own and to control who will have access to the information. Further, recipients of information, who are conceptualized as information co-owners, are also responsible for regulating the flow of information based on a mutually agreed-upon boundary access rule. The rules can be negotiated implicitly or explicitly, but for the case of disclosures on SNSs, the rules may be determined mainly by people who post information. A past study operationalized boundary ownership in a way that individuals possess the right to control posts (e.g., the degree to which individuals perceive how much they have control over information revealed on blog) (Child et al., 2009). On SNSs, users may exercise information ownership by strategically shaping or filtering information according to anticipated audiences.
The boundary linkage rule is about managing boundaries of target audiences through building a unique linkage that individuals attempt to maintain through limiting or driving connections with certain audiences. For example, patients who need to reveal personal information to a hospital’s patient care portal will want to be assured that their information is accessible to others who are able to protect the information (Jin, 2012). The different online platforms afford various ways to link, both for individual users and their audiences. Child et al. (2009) focused on how bloggers manage boundary linkage rules through enabling access and communication with their blog visitors. On blogs, the blog posts can function as a medium to create ties between bloggers and visitors who share similar interests with the bloggers. In the case of SNSs such as Facebook, the coordination of linkage among SNS users can be facilitated through adding channels to connect and to interact. For example, social tagging can build relationships between those who tag and others who are being tagged, enabling mutual sharing of information ownership. This reciprocal sharing, however, can increase concerns about a third party’s access to the shared link, influencing the ways in which SNS users manage personal information boundaries.
In sum, the coordination of the information boundary on SNSs can occur through diverse perceptual paths that involve how individuals select what to reveal (boundary ownership rule), with whom (boundary linkage rule), and how much (boundary permeability rule). The permeability rule, defining the extent to which individuals open up about self, is likely to be influenced by their prior judgments of the boundary ownership rule and the boundary linkage rule. In other words, what individuals are willing to share will depend largely on strategic management of information flow through both defending and promoting the personal information boundary. To examine how the boundary coordination rules tie together, this study will propose and test a causal model according to the theoretical explanations of boundary coordination rules. Based on this initial assumption, the following review will focus on how individuals establish information boundary management rules (ownership and linkage rules) may depend on the ways in which they estimate privacy risks in a disclosure context and are motivated to manage privacy.
Criteria and Privacy Rules
The principles for privacy management show the procedure by which information boundary management rules are made. For example, as described in principles one and two of CPM, individuals’ motivation for information control may increase a tendency to build more rigid rules for managing personal information boundaries. In a similar vein, what SNSs platforms afford (Treem & Leonardi, 2013), such as meeting friends and seeing what people share will impact the extent to which individuals pursue more or less openness. The relationship between these criteria and boundary management rules is proposed next.
Context. According to CPM, context influences people’s perceived risks of disclosures through considerations of the information type, relational considerations, or situations of information sharing (Petronio, 2002). The examination of disclosure contexts can serve as a cue or a knowledge base that people use to assess the potential risks surrounding revealing a specific piece of information. The types and assessments of contexts can vary, so different disclosers may view the disclosure situation through a different lens. For example, people who consider sharing a secret may need to understand how revealing the secret will impact individual (e.g., embarrassment) and relational outcomes (e.g., topic avoidance by the message recipient). In other cases, these people may evaluate the secret based simply on its valence to understand how the disclosure of secret can bring about desirable or undesirable outcomes.
On SNSs, the ways in which perceptions of the context are built are complicated. On one hand, perceptions of context may be formed by factors that signal potential privacy violations. For example, the size of audiences can influence how much a disclosure makes one feel vulnerable due to the possibility of a third party’s access to the disclosed information (Pierson, 2012; Vitak, 2012). According to boyd (2008), context collapse (indicating the process by which individuals are grouped and called a generic term such as “friends” due to blurring individual boundaries on SNSs) generates perceived uncertainties about the identities of disclosure targets because audiences on SNSs are often identified as a large unit of communities (e.g., Facebook friends). It is however not yet clear whether the perception of disclosure targets as a unit of individuals may drive concerns about privacy or perceived benefits of connection. Past research shows contradictory results on the association between the size or composition of audiences and privacy management practices (Litt & Hargittai, 2016; Stutzman & Kramer-Duffield, 2010; Vitak, 2012).
The perceptions about the context of SNSs can be also developed through experiencing the unique features of SNSs that promote boundless communication, connectivity, and networking. Because SNSs afford a platform for people to make friends, build, and maintain connections, using such a site is likely to bring about relational benefits to users (Ellison et al., 2007). Thus, on SNSs, people often interact without spatial, temporal, or relational boundaries, which may increase not only flexibilities in communication but also perceived norms to engage in boundless communication. Therefore, SNSs’ characteristics in generating connections will increase beliefs that openness may be expected and appropriate more than closure or exclusiveness.
Previous research shows that people follow norms about privacy behaviors on SNSs; people are more likely to use privacy features for regulating information when their peers also use those features for privacy protection, although this research does not take into account perceived norms of boundless interactions beyond the norms of using privacy features (Lewis et al., 2008; Utz & Kramer, 2009). The current study thus aims to examine this issue through a research question on how perceptions of boundless interactions on SNSs may impact information boundary management.
RQ1: How will the perceived presence of boundless communication influence the regulation of boundary linkage and boundary ownership rules?
In addition to perceptions of context, culture of disclosure in SNSs will serve as the set of rules for how to regulate information boundaries among users, which is described next.
Culture. Culture is another criterion proposed by CPM that influences information boundary management rules on SNSs. People may generate boundary management rules based on what is believed to be the appropriate pattern of information sharing. Culture can be conceptualized differently based on an assumption that cultural categories relate to the different valuations of privacy rights. For example, the desired level of privacy may be different across countries or ethnicities, so that the tolerance toward reduced personal boundaries varies accordingly (Kaya & Weber, 2003; Ur & Wang, 2013).
In investigating the relationship between culture and behavior, the common cultural categories such as race, ethnicity, and socioeconomic backgrounds have been criticized in their use to understand behaviors across cultures due to the lack of a rigid conceptual definition of the culture as tied to cultural behaviors (Betancourt & López, 1993). A culture may not be a solid construct, but its systems of meanings build and change through the interactions between individuals and expectations of the cultural community (Betancourt & López, 1993; Rohner, 1984). Regarding privacy management on SNSs, a more nuanced understanding of culture is needed, considering that privacy concerns can conflict with the pattern of activities and information sharing within the platform. The activities people engage in on SNSs help shape the unique culture of the platform for forming relationships (Beer, 2008; boyd & Ellison, 2007). That is, the culture promoting disclosure can play a part in forming values about privacy on SNSs. Beer (2008) particularly pointed out the purposive use of SNSs for social networking can serve as a ground to provide a more granular classification of SNSs. Extending this discussion to the matter of privacy management, Child and Petronio (2011) argued that how social networks are defined holds relevance to variations in disclosure and privacy practices. The dynamic of privacy management tied to the culture of each platform will require a more context-dependent conceptualization of culture in relation to the characteristics and expectations of behaviors on SNSs.
In arguing the culture of SNSs, this study posits that SNSs can create a platform for a culture of connections and boundary regulation for appropriate sharing of information. The affordances of SNSs (as a venue to make friends) such as searchability (for more discussions about social media affordance, see boyd, 2010) may be one motivator influencing the expansion of online social networks and information boundary management on SNSs. Treem and Leonardi (2013) also pointed out different functional affordances such as association and visibility that can trigger the desire for revealing rather than hiding. For instance, on SNSs where information sharing and exchanging activities are expected and common, people may be more likely to regulate information boundaries in a looser manner in light of their goal of using the SNSs to make connections.
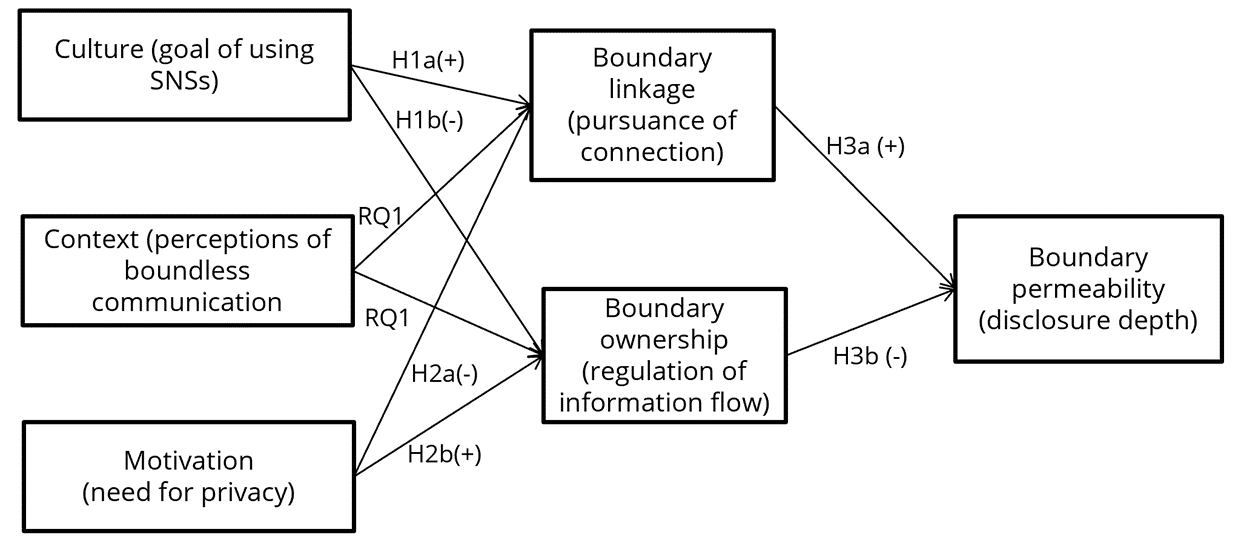
Thus, this research proposes a hypothesis that perceptions of how SNSs meet people’s need to expand connections may induce goals of openness rather than closure, and will positively influence the pursuance of opportunities to create connections with others (coordination of boundary linkage rule) but will negatively influence controlling information ownership (coordination of boundary ownership rule).
H1a: The culture of SNSs to make friends will positively influence the coordination of the boundary linkage rule.
H1b: The culture of SNSs to make friends will negatively influence the coordination of the boundary ownership rule.
Motivation (Need for Privacy). In addition to the goal of using SNSs to connect, people’s motivation to protect privacy may be a factor for building rules for privacy management in general. As postulated by Altman (1975) and Petronio (2002), the desire for privacy is intrinsic, that is, it is part of human nature to simultaneously maintain openness and closure. According to an evolutionary perspective, Long and Averill (2003) articulated the importance of solitude, because it can balance social activities for more harmonious living. Other researchers proposed that the disposition toward solitude or autonomy can vary as people go through developmental stages (Lawton & Bader, 1970). The developmental view of privacy management emphasizes that people learn how to negotiate privacy boundaries through various social and educational environments. For example, Petronio (2002) proposed that one may learn how to negotiate privacy boundaries based on how his/her family teaches him/her to do so. On a more fundamental level, Petronio argued that people deal with increasingly complicated boundary access rules as they grow older because they possess more varied kinds of information. In short, the disposition towards privacy may be constructed through social and learning processes, helping one form strategies for boundary management (see Yao et al., 2007). In SNSs particularly, disclosure decisions may reflect these people’s concerns about privacy caused by the dynamic interaction with unique SNSs platform. Thus, people’s desire for privacy should be considered as a predictor for boundary management rules. The more people perceive a higher need for privacy, the more likely it will be that they may strategize rules to coordinate the information boundary through monitoring what to reveal. On the other hand, the desire for privacy may negatively influence the willingness to promote connections.
H2a: The need for privacy will negatively influence the coordination of the boundary linkage rule.
H2b: The need for privacy will positively influence the coordination of the boundary ownership rule.
Regulation of Information Boundaries and Disclosure Patterns
As discussed above, by managing information boundary coordination rules, individuals may reduce concerns that emerge from circumstances under which their information is open to the public (coordination of boundary ownership rule). Compared to the boundary ownership rule, the boundary linkage rule affects how people coordinate information boundaries with a willingness to maintain rather than to restrict access to personal information. Therefore, the coordination of the boundary ownership rule and the boundary linkage rule can function differently for disclosure outcomes. In examining the influence of boundary coordination rules and disclosure outcomes, Child et al. (2009) proposed the coordination of the boundary permeability rule as how people regulate the amount, breadth, and depth of information. The disclosure depth may be considered as a way to measure the extent of control based on an assumption that an in-depth disclosure can be costly and thus can necessitate the application of boundary coordination rules.
Prior research has provided mixed results on the association between the use of privacy boundary rules and disclosure outcomes (in this study, the permeability rule), although the operationalization of disclosure outcomes varied across studies. For example, one study shows that, over a period of time since the development of Facebook, users have become knowledgeable about how to restrict personal information flow on Facebook. However, the careful privacy strategy (e.g., disclosing to designated targets) eventually increased the amount of information revealed towards unidentified audiences in part because people could not fully control the information flow after sharing (Stutzman et al., 2012). This finding implies that while people have become more alert about the challenge in managing privacy boundaries, they may not fully anticipate the long-term outcomes of disclosure. Other research, however, shows that there is not a significant association between the use of privacy features and disclosure amount (Ellison et al., 2011; Vitak, 2012). Further, perceptions of control and disclosure (operationalized as the likelihood of revealing personal information on Facebook) were not found to be positively associated (see Christofides et al., 2009 for discussion).
This current study drew on Child et al. (2009) to define the boundary ownership rule in terms of how people control the flow of information in general. Controlling information that is supposed to be posted on SNSs reflects an effort to limit what is visible about self on SNSs. For instance, when anticipating the leakage of information to unwanted audiences, the people may use the lowest common denominator to buffer disclosure risks (Marwick & boyd, 2011). Thus, regulating boundary ownership will represent careful considerations of revealed information, reducing the motivation to disclose deeply about self. On the other hand, seeking out future connections through the management of the linkage rule may be positively related to individuals’ willingness to share information about self.
H3a: The coordination of boundary ownership rule will negatively predict disclosure depth on SNSs.
H3b: The coordination of boundary linkage rule will positively predict disclosure depth on SNSs.
Theoretical Model
Figure 1 presents the theoretical model proposed by this study. The pursuance of each boundary coordination rule may be operationalized differently in terms of the ways that individuals regulate information flow on SNSs by how to control it (i.e., regulating boundary ownership rule) with whom (i.e., regulating boundary linkage rule), and to what extent (i.e., regulating boundary permeability rule). These boundary coordination rules will be influenced by the ways in which SNSs users perceive the disclosure culture (goal of using SNSs), context (perceived presence of boundless communication), and privacy motivation (perceived need for privacy). Based on the rationale that proposes the motivations for privacy boundary coordination and following disclosure outcomes, the following model is proposed for this study.
Figure 1. Hypothesized Model for Privacy Rule and Disclosure.
Method
Participants and Procedure
The study examined SNS users through a convenience sample of college students in a large northeastern US university in fall 2015. For this particular study, the popular site Facebook met the study goals to measure boundary coordination rules, so Facebook users were the focus. To recruit participants, the researcher contacted several instructors of communication courses, who distributed a flyer indicating participation criteria: participants needed to be an active Facebook user and have made posts on Facebook in the past six months. Participants provided self-report data on study variables through an online survey. Participants had access to a link to the online survey through a course website and had to fill out the survey all in one sitting. Once the participants clicked the survey, they were asked to fill out the survey, after consenting to participate. Extra credit was offered by instructors to those students who participated. The final total of participants included 397 Facebook users (Mage = 20.68, SDage = 3.63). Among the participants, 265 (66.8%) were female. About forty-three percent of participants were Non-Hispanic White, and the others included Asian (15.9%), Asian Americans (14.9%), Hispanic (9.3%), Non-Hispanic Black (5.0%), Bi-Multiracial (4.3%), and other or unidentified ethnicity (7.5%). The results reported in this study are part of a larger project approved by the author’s university IRB.
Measures
Culture (Goal of Using SNSs)
Individuals’ goal of using SNSs was measured by two 7-point Likert-type items adapted from Joinson (2008) with responses ranging from 1 (strongly disagree) to 7 (strongly agree). Reliability in this study was acceptable (α = .70, r = .55, M = 4.50, SD = 1.49). Items include, “By using Facebook, I can meet new people,” and “By using Facebook, I use advanced search to look for specific types of people.”
Context (Perceptions of Boundless Communication)
Individuals’ perceived presence of boundless communication was measured by three 7-point Likert-type items developed by the author based on prior research by Yan and Sengupta (2011) with responses ranging from 1 (strongly disagree) to 7 (strongly agree). Reliability in this study was acceptable (α = .74, M = 4.55, SD = 1.17). Sample items include, “I feel I am interacting simultaneously with my Facebook friends,” and “I feel my friends are also available on Facebook.”
Motivation (Need for Privacy)
The need for privacy was measured by four 7-point Likert-type items adapted from Yao et al. (2007) with responses ranging from 1 (strongly disagree) to 7 (strongly agree). Reliability in this study was acceptable (α = .77, M = 5.10, SD = 1.08). Sample items include, “I’d rather not talk about myself on Facebook,” and “I prefer others know little about me on Facebook.”
Boundary Ownership (Regulation of Information Flow)
The exercise of the boundary ownership rule was measured by four 7-point Likert-type items adapted from Child et al. (2009) with responses ranging from 1 (strongly disagree) to 7 (strongly agree). Reliability in this study was acceptable (α = .71, M = 5.26, SD = 1.00). Items include, “On Facebook, I use shorthand (e.g., pseudonyms or limited details) when discussing sensitive information so others have limited access to know my personal information,” “When I post on Facebook, I consider whether the information that I am about to post is appropriate to share with others,” “I make posts on Facebook after considering who may view the posts,” and “I have limited the personal information posted on Facebook.”
Boundary Linkage (Pursuance of Connection)
The rule for boundary linkage coordination was measured by two 7-point Likert-type items adapted from Child et al. (2009) with responses ranging from 1 (never) to 7 (often). Reliability in this study was fair (α = .55, r = .40, M = 4.29, SD = 1.04). The items were “How often do you tag others in your posts or photos?” and “How often have you been tagged into others' posts?”
Boundary Permeability (Disclosure Depth)
Boundary permeability coordination, the disclosure depth, was measured by three 7-point Likert-type items adapted from Parks and Floyd (1996), and Child et al. (2009) with responses ranging from 1 (strongly disagree) to 7 (strongly agree). Among the three items, an item was removed to increase reliability and the final reliability of the two remaining items was moderately strong (α = .88, r = .79, M = 2.45, SD = 1.43). The remaining items were “I share in detail how I feel on Facebook,” and “I share intimate or personal things about myself on Facebook.”
Facebook Intensity (Control Variable)
Facebook intensity was measured by items adapted from Ellison et al. (2007) that included two self-reported assessments of Facebook behavior (i.e., the number of Facebook friends and the amount of time spent on Facebook on a typical day). The measure also included six 7-point Likert-type items (a sample item was “I am proud to tell people I'm on Facebook.”), with responses ranging from 1 (strongly disagree) to 7 (strongly agree). All these items were standardized before creating a composite scale. The reliability of the final measure in this study was moderately strong (α = .86, M = .00, SD = .71).
Basic Privacy Setting (Control Variable)
Individuals’ basic privacy setting was measured by self-reporting of participants who were asked to look at and report their actual Facebook privacy setting. Among all, 16.1% (n = 64) had modified their privacy setting to only me or a custom setting (i.e., open the Facebook page to selected individuals), 83.9% (n = 333) kept their privacy setting to “Friends”, or opened their setting to the public.
Results
Table 1 presents a zero-order correlation matrix for all study variables. The hypothesized model for this project was tested through maximum likelihood structural equation modeling (AMOS 23). In order to run the structural equation modeling, each variable in the model was tested for parallelism to confirm unidimensionality of measure. The test of parallelism found that all measures included in the model had discriminant validity.
The model is considered to fit the data if x2/df is less than 3, CFI and NFI are greater than .90, and RMSEA is less than .10 (Hooper et al., 2008). The study fixed the error variance for each latent variable within the model to (1-α) (σ2) to account for unreliability within the measures. The data were screened for normality and outliers, and no transformations were needed. When running the model, Facebook intensity and individuals’ basic privacy setting (i.e., whether individuals create any exclusive boundaries on their Facebook page; that is, if their Facebook page is open to all friends or public, or selected individuals) were controlled. The following section reports the results of the study.
Table 1. Zero-Order Correlation Matrix for All Study Variables.
|
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
||
|
1 |
Culture |
1 |
|||||||
|
2 |
Context |
.31** |
1 |
||||||
|
3 |
Motivation |
-.09 |
-.16** |
1 |
|||||
|
4 |
Boundary linkage |
.13** |
.25** |
-.21** |
1 |
||||
|
5 |
Boundary ownership |
.11* |
.17** |
.26** |
.18** |
1 |
|||
|
6 |
Boundary permeability |
.11* |
.17** |
-.16** |
.25** |
-.24** |
1 |
||
|
7 |
Facebook intensity |
.15** |
.37** |
-.20** |
.46** |
.07 |
.16** |
1 |
|
|
8 |
Basic privacy setting |
.05 |
-.02 |
.08 |
-.11* |
.02 |
-.08 |
-.13* |
1 |
|
Note. **p < .01, *p < .05. |
|||||||||
Results of Structural Equation Model
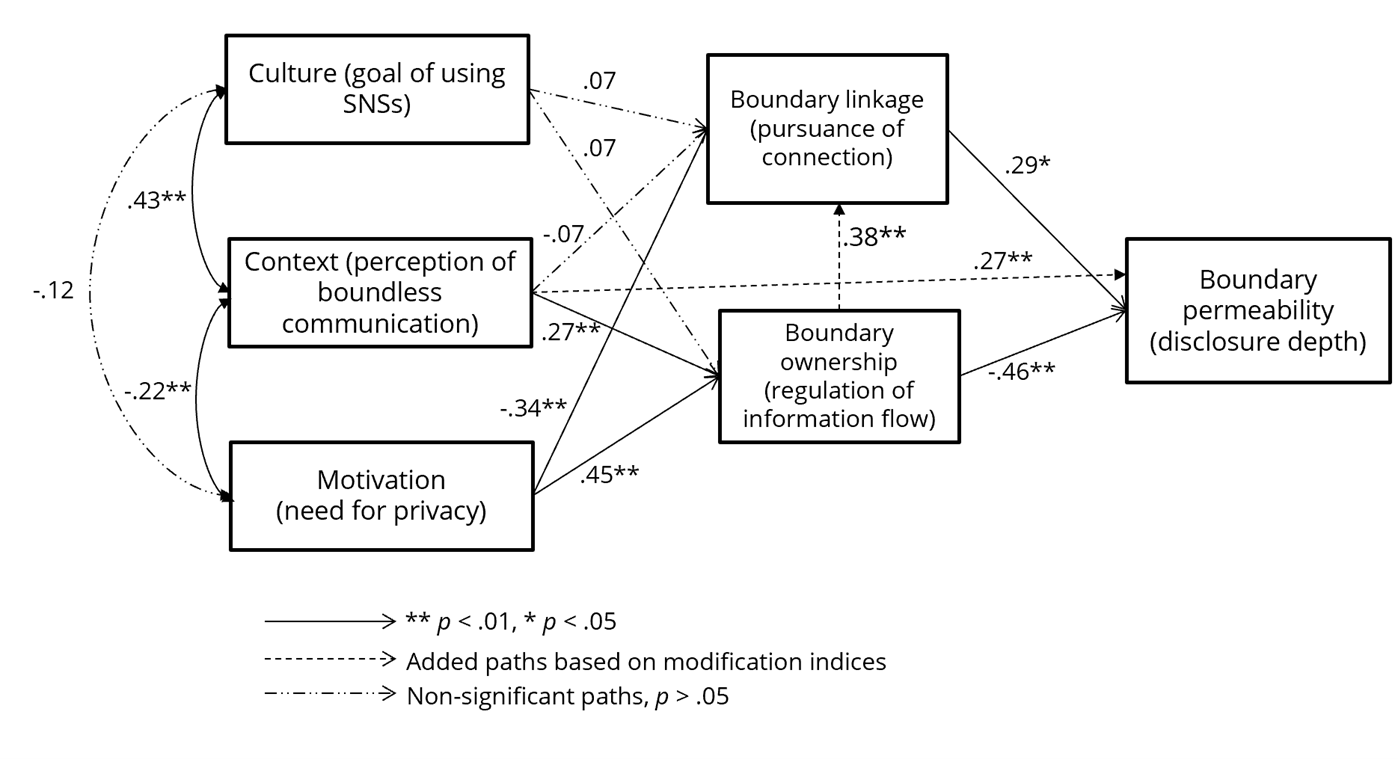
Results of the structural equation modeling indicated that the original model did not adequately fit the data: χ2(4) = 38.59, CFI = .90, NFI = .90, RMSEA = .15. Modification indices recommended the addition of a path from the coordination of boundary ownership rule to the boundary linkage rule. With this path added, the model fit improved but the model still did not fit the data: χ2(3) = 19.08, CFI = .95, NFI = .95, RMSEA = .12. Modification indices recommended the addition of a path from the context to the coordination of boundary permeability rule (depth of disclosure). With this path added, the model did fit the data: χ2(2) = 5.87, CFI = .99, NFI = .98, RMSEA = .07 (Figure 2)1. The paths presented in the model are standardized coefficients.
Research Question 1 asked how the perception of boundless communication on SNSs influences the coordination of boundary linkage and boundary ownership rules. Findings reveal that perceiving boundless communication on SNSs positively influenced boundary ownership coordination but did not influence the coordination of the boundary linkage rule.
Hypothesis 1a (H1a) predicted that culture (the goal of using SNSs for making friends) will positively influence the coordination of the boundary linkage rule but will negatively influence the coordination of the boundary ownership rule (H1b). Findings of the structural equation modeling show that H1 was not supported because the goal of using SNSs did not predict the coordination of either the boundary linkage rule or the boundary permeability rule. Hypothesis 2a (H2a) predicted that the need for privacy negatively influences the boundary linkage rule coordination whereas hypothesis 2b (H2b) predicted a positive relationship between the need for privacy and the coordination of boundary ownership rule. H2 was supported in that people who had a higher need for privacy were less likely to engage in behaviors to create linkage but were more likely to regulate their information flow on SNSs.
Hypothesis 3a (H3a) predicted that the coordination of the boundary linkage rule positively predicts the coordination of the boundary permeability rule (depth of disclosure). H3b predicted that the coordination of boundary ownership rule negatively predicts the depth of disclosure. As predicted, coordinating boundary linkage on SNSs increased the depth of disclosures. Further, people who cautiously and selectively revealed about self on SNSs were less likely to disclose about self more deeply than others who did not share information selectively. Therefore, H3 is supported.
As for added paths, there was a statistically significant and positive relationship between perceptions of boundless communication and disclosure depth. The relationship between the coordination of boundary ownership and boundary linkage rules was statistically significant and positive.
Figure 2. Tested Model.
Discussion
This study examined processes of information boundary coordination on SNSs as they influence disclosures. The study proposed three predictors of information boundary coordination to contextualize the boundary management practices specifically in SNSs (Facebook). In particular, it aimed to examine how the boundary coordination practices are intertwined in such a way that coordinating potential interactions with others (boundary linkage rule) and regulating personal information flow on SNSs (boundary ownership rule) impacts the depth of disclosures (boundary permeability rule). The analysis provided mixed support for the hypothesized relationships and provided answers to the research question.
The research question of the current study asked about the relationship between the perceptions of boundless communication on SNSs (context) and the coordination of both boundary linkage and ownership rules. The results show that perceiving the presence of boundless communication across time, space, and relationship triggers a need to regulate information posted on SNSs, whereas it does not necessarily influence individuals to engage in actions to build and maintain future interactions. Regarding the RQ, another notable finding was the proposed path from the context to the coordination of the boundary permeability rule (disclosure depth2) in the final model.
Related to the final model fit with this added path (Figure 2), the role of the perceived presence of boundless communication in generating boundary coordination rules can be discussed in terms of its various functions in the comprehensive boundary coordination process. First, given the positive association between the perceived presence of boundless communication and the coordination of the boundary ownership rule, it is assumed that the perception may function to drive potential threats to individual privacy on SNSs, leading to the active regulation of information ownership. This finding supports similar prior research. For example, individuals have been found to engage in self-censorship when they anticipate their audiences to be more diverse, showing that uncertainty about a target audience creates a desire for privacy protection (Vitak, 2012; Vitak et al., 2015).
At the same time, the direct positive association between perceptions of boundless communication and disclosure depth on SNSs may indicate that perceptions of a lack of boundaries may also function to form perceptions about norms of openness on SNSs. As a result, information boundary management on SNSs may occur in two different ways such that, in response to the perceptions of context, people need to control information that will be posted on the site, but while controlling information, they may stretch the range of connections through making disclosures. This finding connects to the basic premise of the privacy management process within which people continuously balance tensions between openness and closure rather than choosing one goal over the other (Petronio, 2002). Another explanation for the positive relationship between context and disclosure depth is that people who acknowledge the boundless communication on SNSs are already active on SNSs (see Table 1 for the significant positive relationship between context and Facebook intensity) and also make disclosures more than others who are less active on SNSs. Indeed, research shows that people who actively use SNSs are more likely to make disclosures, and that more disclosures may be facilitated by rewards such as social capital (Trepte & Reinecke, 2013).
The path from the context to disclosure can extend the discussion about boundary coordination rules on a theoretical level. In this study, the context was considered as a predictor of boundary linkage and boundary ownership rules prior to the boundary permeability rule. That is, the study’s theoretical model makes an assumption that the coordination of boundary linkage and ownership rules is under the direct influence of the context while the coordination of boundary permeability rule is considered an outcome of these boundary regulations. However, the addition of a path from the context to the self-disclosure depth suggests the coordination of each rule constitutes the process of information boundary management distinctively but equally as relevant to its association with context, culture, and motivation.
Although Petronio (2002) treated the three boundary coordination rules as distinct but compatible, the management of each rule can interrelate based on their conceptual and operational definitions. For example, in Child et al. (2009), the permeability rule focused on the regulation of disclosure while the ownership rule focused on the regulation of access and the linkage rule focused on the regulation of connection. Considering that disclosures occur with conscious consideration of their outcomes involving various privacy threats, the current research assumed that the coordination of ownership and linkage precede the coordination of permeability rule. The added path from the context to the disclosure depth does not meet this assumption, and it requires further thought on how the privacy rule criteria influence the coordination of boundary management rules. When it comes to privacy management, self-disclosure has been treated as a behavioral outcome of individuals’ anticipated concerns after disclosure (Joinson et al., 2010; Vitak & Kim, 2014). 3The coordination of the boundary ownership rule can reflect a conscious effort to plan on how to regulate personal information, which can impact the disclosure outcomes. The coordination of the boundary linkage rule reflects a motivation to connect, which can broaden shared information ownership and can lead to more disclosures.
Lastly, a methodological point of view can help explain the results. The results may also be driven due to the use of self-report measures for the perception of boundless communication and disclosure depths. There is a possibility that the perceptions of boundless communication can exaggerate perceptions that individuals are making more in-depth disclosures while they are actually being careful about what to disclose. Future research will benefit from building on these findings to propose more nuanced operationalizations of context and communication norms on SNSs, which influence patterns of disclosures on SNSs.
It is also notable in findings of the RQ that there was not a statistically significant relationship between the perceptions of boundless communication and the coordination of the boundary linkage rule. Given that people who perceive the prevalence of communications without rigorous boundaries attempt to regulate their own information flow (as shown through the positive path from the context to the coordination of boundary ownership rule), this finding can provide an insight into how perceiving context can lead to different boundary coordination activities on SNSs. Those perceptions influence the regulation of boundaries but not the expansion of boundaries towards potential future connections. The discussion of this finding can extend to the interpretation of results from the test of Hypothesis 1 and 2.
Hypothesis 1a proposed a positive association between the goal of using SNSs for making friends (culture) and the coordination of the boundary linkage rule. Hypothesis 1b proposed a negative relationship between the goal of using SNSs for making friends and the coordination of the boundary ownership rule. H1 was not supported. There was not a statistically significant relationship between the goal of using SNSs and either the coordination of boundary linkage or ownership rules. Although the goal of using SNSs for making friends may predict an extensive use of SNSs, such a goal may not predict how individuals take advantage of the SNS platform to connect with diversified social networks, or how the individuals regulate their personal information flow.
In relation to CPM’s theoretical framework, the current study conceptualized culture narrowly to identify a relevant boundary coordination pattern on SNSs. The lack of support for H1 leaves room for discussion that culture as conceptualized in this study functions more as perceptions of what SNSs afford, which may be loosely connected to the participation in boundary coordination activities expected on the platform. Past research shows that activities to create links on SNSs such as social tagging are related particularly to individual inclinations such as habits or hedonic motivation (Dhir et al., 2018). The motivation or habit to tag (as conceptualized as the coordination of the boundary linkage rule in this study) may be caused by continuous involvement in the behavior, both cognitively and physically. Thus, being only aware of affordances of SNSs for making connections rather than actively being involved in behaviors afforded by SNSs may not be considered as a sufficient predictor for actions to facilitate linkage.
Another explanation for this nonsignificant association between culture and the coordination of boundary linkage and ownership rules is the degree that culture contributes to the boundary coordination procedure. More specifically, in the correlational analysis among all variables, culture had a statistically significant positive influence on each of the boundary linkage and ownership rules (see Table 1); the more individuals used SNSs for making friends, the more likely that they managed boundary linkage and ownership rules. However, due to the nonsignificant influence of culture on both variables in the suggested comprehensive model, it may be assumed that the degree to which culture impacts the management of these rules may not be as critical as other boundary management criteria (such as privacy need) in this study.
Hypothesis 2a proposed a negative association between the need for privacy (motivation) and the coordination of the boundary linkage rule. Hypothesis 2b proposed a positive relationship between the need for privacy and the coordination of the boundary ownership rule. H2 was supported. People’s desire to protect personal information reduced their tendency to reserve room to connect with others. In addition, this desire for privacy led people to be more cautious about regulating personal information flow.
This result supports what previous research has found in terms of how individuals’ consideration for privacy influences their decision for managing privacy rules. Prior research has examined the different motivations for privacy management rules. For example, people who have greater concerns about privacy are more likely to engage in more rigid information boundary management than others who are less concerned about privacy, and this tendency is found in different online contexts including social media (Vitak, 2012) and online customer websites (Metzger, 2007). Although the concepts of the need for privacy and concerns about privacy are different constructs, these variables may share the variance of perceived need for privacy in the explanations of how people become conscious of privacy protection. The motivation for privacy can be operationalized diversely according to the context. For example, concerns about mediated lurking, impression management concerns, and employment security were identified as possible motives to engage in more rigid management of privacy rules (Child et al., 2012; Child & Starcher, 2016). In light of prior literature, the current study approached the conceptualization of privacy motive as how it relates to the fundamental human desire for privacy.
In general, for the relationship found in the model between boundary management criteria and the coordination rules, it is also notable that privacy motivation was the only predictor for the coordination of the boundary linkage rule. Compared to the influence of context and culture, the motivation (need for privacy) had a statistically significant impact on the extent to which individuals manage their social network as well as regulate the flow of information. The negative association between the need for privacy and the coordination of the linkage rule can be driven by how the protection motivation influences a willingness to expand one’s social network. The need for privacy, while being shaped in part by situational or social needs, can be understood as an inborn trait that has a solid influence on privacy motivations (Doyal & Gough, 1991; Petronio, 2002).
The lack of support for culture and context in facilitating boundary coordination rules (particularly, the boundary linkage rule) may also partially be due to the variability in how people perceive their privacy context and cultural expectations. In particular, research using CPM conceptualized context in different patterns according to the situation appropriate for disclosure (Bazarova, 2012), anticipated positive disclosure outcomes (Petronio & Sargent, 2011), or the dynamic of relationships (Frampton & Child, 2013). In these studies, context was assumed to play a role in helping individuals frame the situation, in that it can signal if the regulation of information is more or less likely to be required for privacy protection. In the current study, the motivation to expand links with others can be related more to the privacy motivation rather than the goal of using SNSs and the prevalence of boundless communication on SNSs.
Hypothesis 3a (H3a) proposed a positive association between the coordination of the linkage rule and disclosure depth. Hypothesis 3b (H3b) proposed a negative association between the coordination of the boundary ownership rule and disclosure depth. Both parts of Hypothesis 3 were supported. Results of H3a show that people who aim to build connections through increasing their visibility to third parties (coordination of boundary linkage rule) are more likely to make in-depth disclosures than their counterparts. Expanding one’s visibility through creating links through shared interests can predict how much people want to open up about self (Child et al., 2009). Although the boundary linkage rule can apply differently as to how individuals regulate the third party’s access or allow that access to personal information (Petronio, 2002), this study aimed to focus on the latter, considering its relevance to the association affordance of SNSs (Treem & Leonardi, 2013).
The results of H3b support previous findings and the theoretical association between boundary coordination and disclosure outcomes. CPM proposes that disclosure is an outcome of dialectical tensions of openness and closure and the ways in which people choose to open up depend on how strictly they claim ownership over information (Petronio, 2002). Regulating boundary ownership indicates that people tend to build a thick and rigid information boundary to restrict access to their information. On SNSs, controlling what to post may reflect people’s motivations of not revealing a lot about self, which may lead to a reduced level of disclosures.
In short, the negative relationship between the coordination of information ownership and disclosure depth, along with the positive relationship between the coordination of boundary linkage and disclosure depth, suggest that boundary linkage and boundary ownership rules play different roles in forming disclosure patterns on SNSs. For example, when disclosing about self on SNSs, people may regulate the ownership of information by restricting the range of information to be disclosed on SNSs. However, granting continuous and mutual interactions through social tagging may also play an important role in triggering disclosure at the same time.
The suggested addition of a path from the coordination of boundary ownership rule to the coordination of boundary linkage rule can also help expand a discussion on how different boundary coordination rules coexist and their shared influence on disclosure depth. More specifically, the positive influence of the coordination of information ownership on the regulation of information linkage informs how different boundary management rules are interrelated. Considering that the model presents causal relationships among the variables, the results show the considered process to filter information (boundary ownership rule) can lead to a greater tendency to engage in fostering networks in the future. Taking the view that the regulation of information flow may represent a motivation to protect privacy, this finding will need further exploration regarding how the boundary coordination efforts work together. As described above, people who actively share personal information may be strategic enough to achieve both goals of privacy and connection. The ways in which people employ privacy rules to simultaneously designate information ownership and linkage are underexplored. Future research may build upon these results to provide a more solid conceptualization of information boundary management rules on SNSs.
Implications and Future Directions of Research
In terms of advancing the theoretical framework to examine the influence of information boundary management on disclosures, this study has made a contribution by examining disclosure processes via boundary management rules. The study focused on creating a conceptual link between information boundary management and disclosure in such a way that disclosure outcomes (reflecting boundary permeability rule) are theoretically driven by boundary coordination rules (boundary linkage and ownership rules) as proposed by CPM. Past research has focused on disclosure as an outcome of various privacy concerns on SNSs and examined the relationship between the degree of privacy concerns and disclosure specifically (Chen & Chen, 2015; Zlatolas et al., 2015). On SNSs, an important goal of disclosure is to build relationships. Thus, although disclosure outcomes can relate to privacy concerns, the process of disclosure should reflect their motivations for connection as well.
Findings from the study can provide nuanced interpretations of how motivations to protect privacy impact the patterns of boundary rule coordination, and how these differ from how perceptions of context and culture influence the coordination of boundaries. Although the need for privacy may increase the tendency to defend personal information boundaries, the perception of culture (as a goal of using SNSs) may not ultimately lead to the planning of how to regulate those information boundaries. This finding suggests the varied roles of boundary management criteria on SNSs in operating the coordination of different boundary management rules, in particular the robust influence of privacy needs in the management of both the linkage and the ownership rules.
As for replicating and building the conceptual model of privacy regulation and disclosure according to CPM, future research may continue exploring the role of context in managing privacy rules and disclosure. The context for privacy management may be different from the norms of privacy practices (in this study, shaped by culture) because understanding the characteristics of context is a perceptual process that can vary among individuals. For example, the size of each individual user’s network on SNSs can have a different influence on how that individual perceives the degree of boundless communication. Therefore, including the context in the privacy and disclosure model helps researchers understand its role in mobilizing privacy rules.
More importantly, such a perceptual variable can indicate how the psychological process of boundary management occurs in decision-making about privacy management and disclosure. As the final model of this study shows, the relationship between perceptions of boundless communication and the need for privacy was statistically significant and negative. This may indicate that perceiving that others engage in boundless communication on SNSs can decrease motivation to pursue one’s own privacy need. On the other hand, there was a statistically significant and positive relationship between both the perception of boundless communication and the management of the boundary permeability rule (disclosure depth). The same direction of impact of context on how much to restrict and how much to reveal can provide room for further research on the ways in which perceptions of context can trigger both desires for privacy and disclosure.
Limitations
The current study has a few limitations. First, the study relied on a convenience sample of college students who—even though they are active SNS users—may not represent all users who may vary in their approach to using boundary coordination rules to make disclosures (Litt, 2013). For approaching the generalization of results, future research will benefit from recruiting population samples who are distinguished across demographics and thus provide a more comprehensive understanding of the boundary coordination process when making disclosures on SNSs. Another limitation of this study is that it used self-report data of information boundary coordination practices and disclosure tendencies. When examining information boundary coordination on SNSs, behavioral measures rather than perception measures may provide more accurate explanations of privacy behaviors given the nature of social desirability measures per privacy management practice. Lastly, in adapting measures from prior research, the study employed selected measures for boundary coordination rules, although those adapted measures did show acceptable reliability, except in the case of the boundary linkage rule (Mohajan, 2017; Terwee et al., 2007). When operationalizing boundary coordination rules in different contexts, the employment of measures from past research can preserve flexibility, but will require rigorous criteria for choosing items to obtain good reliability of measure.
Footnotes
1 Model fit with all measurement scales: χ2(136) = 399.08, CFI = .88, NFI = .83, RMSEA = .07.
2 Hereafter, the disclosure depth instead of the boundary permeability rule will be used for a smoother description of findings.
3 When the model was tested with the three boundary coordination rules treated correspondingly in their associations with context, culture, and motivation, the modification indices proposed the addition of a path from the coordination of boundary ownership rule to the coordination of boundary permeability rule.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
Copyright © 2021 Cyberpsychology: Journal of Psychosocial Research on Cyberspace


