Associations of traditional and peer cyber-victimization with adolescents’ internet Use: A latent profile analysis
Vol.13,No.4(2019)
Significant overlap exists between traditional victimization and peer cyber-victimization. Yet, they can also be somewhat differentiated. Adopting person-centered approaches, studies showed that multiple classes of peer victimization are distinguishable. In particular, this study analyzed the differences in Internet use, Internet motives and behavior and ethical media use of adolescents who are victimized only (or mainly) online (i.e., “cyber-victims”), their peers who are victimized at school (“traditional victims”), students who are frequently victimized both offline and online (“dual victims”), and students who are not victimized. A sample of 1377 Italian adolescents (49.5% females, age M = 16.13, SD = 1.27) completed self-report questionnaires of traditional and peer cyber-victimization and a variety of Internet-related measures. Latent profile analysis yielded four distinct groups: non-victims (79.6% of the sample), traditional victims (9.2%), cyber-victims (9.1%), and dual victims (2.1%). Among the four groups, dual victims, that is, adolescents who are frequently victimized both at school and online, showed the most problematic use of information and communication technologies (ICT). Dual victims and cyber-victims also reported to engage more frequently than the other groups in a variety of Internet activities (e.g., role-playing games and visiting adult sites). Traditional victims reported more coping and conformity motives for using Internet compared to non-victims and, in the latter case, also to cyber-victims. The current findings may help to better understand the link between traditional victimization and peer cyber-victimization with adolescent’s use of information and communication technologies and may inform prevention and educational programs about positive use of new technologies among adolescents.
Traditional victimization; cyber-victimization; problematic Internet use; Internet use motives; online risks
Gianluca Gini
Department of Developmental Psychology and Socialization, University of Padua, Padova, Italy
Gianluca Gini, PhD, is professor of developmental psychology at the Department of Developmental Psychology and Socialization, University of Padova, Italy. His research is focused on understanding the individual (emotional and moral) and social (friendship networks, normative peer pressure, school climate) processes associated with different roles of participation in bullying and on assessing the health and psychosocial consequences of frequent involvement in bullying. He is also interested in meta-analytic techniques applied to developmental and educational psychology.
Claudia Marino
Department of Developmental Psychology and Socialization, University of Padua, Padova, Italy
Claudia Marino, PhD, is currently research fellow at the Department of Developmental Psychology and Socialization, University of Padova, Italy. She is also visiting researcher at the Centre for Addictive Behaviours Research, London South Bank University, UK. Her major research interests include problematic Internet use (social media, gaming, smartphone) among adolescents and young adults and metacognitive therapy.
Jia-Yan Xie
Department of Developmental Psychology and Socialization, University of Padua, Padova, Italy
Jia-Yan Xie, MA, is doctoral student in psychological sciences at the University of Padova, Italy. She is currently studying adolescents’ online deviant behavior is relation to family, peer, and contextual risk factors.
Jan Pfetsch
Department of Educational Psychology, Technische Universität Berlin, Berlin, Germany
Jan Pfetsch, Ph.D., is a guest professor and the deputy head of the Department of Educational Psychology at Technische Universität, Berlin, Germany. He developed a bystander intervention training program in the context of offline bullying at school. His current research focuses on cyberbullying (especially cyberbystanders), empathy in offline and online contexts, media use and media literacy, the development of competencies in teacher training (especially diagnostic competence), learning with digital media, and aggressive and prosocial behavior in children and adolescents.
Tiziana Pozzoli
Department of Developmental Psychology and Socialization, University of Padua, Padova, Italy
Tiziana Pozzoli, PhD, is currently assistant professor at the Department of Developmental Psychology and Socialization, University of Padova, Italy. Her research interests include individual and contextual variables associated with different behavior during bullying episodes, focusing especially on bystanders’ behavior (e.g., defending and passive bystanding).
Asparouhov, T., & Muthén, B. (2014). Auxiliary variables in mixture modeling: Using the BCH method in Mplus to estimate a distal outcome model and an arbitrary secondary model. Mplus Web Notes, 21(2), 1-22.
Aufderheide, P. (1993). Media Literacy. A report of the national leadership conference on media literacy. Queenstown, MD: The Aspen Institute.
Bakk, Z., & Vermunt, J. K. (2016). Robustness of stepwise latent class modeling with continuous distal outcomes. Structural Equation Modeling: A Multidisciplinary Journal, 23, 20-31. https://doi.org/10.1080/10705511.2014.955104
Bandura, A. (1978). Social learning theory of aggression. Journal of Communication, 28(3), 12-29. https://doi.org/10.1111/j.1460-2466.1978.tb01621.x
Barboza, G. E. (2015). The association between school exclusion, delinquency and subtypes of cyber-and F2F-victimizations: Identifying and predicting risk profiles and subtypes using latent class analysis. Child Abuse & Neglect, 39, 109-122. https://doi.org/10.1016/j.chiabu.2014.08.007
Bauman, S., Cross, D, & Walker, J. (Eds.). (2013). Routledge monographs in mental health. Principles of cyberbullying research: Definition, methods, and measures. New York, NY, US: Routledge/Taylor & Francis Group.
Beard, K. W., & Wolf, E. M. (2001). Modification in the proposed diagnostic criteria for Internet addiction. CyberPsychology & Behavior, 4, 377-383. https://doi.org/10.1089/109493101300210286
Beltrán-Catalán, M., Zych, I., Ortega-Ruiz, R., & Llorent, V. J. (2018). Victimisation through bullying and cyberbullying: Emotional intelligence, severity of victimisation and technology use in different types of victims. Psicothema, 30, 183-188. https://doi.org/10.7334/psicothema2017.313
Bischof-Kastner, C., Kuntsche, E., & Wolstein, J. (2014). Identifying problematic Internet users: Development and validation of the Internet Motive Questionnaire for Adolescents (IMQ-A). Journal of Medical Internet Research, 16(10), e230. https://doi.org/10.2196/jmir.3398
Boniel-Nissim, M., & Sasson, H. (2018). Bullying victimization and poor relationships with parents as risk factors of problematic internet use in adolescence. Computers in Human Behavior, 88, 176-183. https://doi.org/10.1016/j.chb.2018.05.041
Bradshaw, C. P., Waasdorp, T. E., & O'Brennan, L. M. (2013). A latent class approach to examining forms of peer victimization. Journal of Educational Psychology, 105, 839-849. https://doi.org/10.1037/a0032091
Brown, C. F., Demaray, M. K., Tennant, J. E., & Jenkins, L. N. (2017). Cyber victimization in high school: Measurement, overlap with face-to-face victimization, and associations with social–emotional outcomes. School Psychology Review, 46, 288-303. https://doi.org/10.17105/SPR-2016-0004.V46-3
Canale, N., Vieno, A., Griffiths, M. D., Marino, C., Chieco, F., Disperati, F., . . . Santinello, M. (2016). The efficacy of a web-based gambling intervention program for high school students: A preliminary randomized study. Computers in Human Behavior, 55, 946-954. https://doi.org/10.1016/j.chb.2015.10.012
Caplan, S. E. (2010). Theory and measurement of generalized problematic Internet use: A two-step approach. Computers in Human Behavior, 26, 1089-1097. https://doi.org/10.1016/j.chb.2010.03.012
Carretero, S., Vuorikari, R., & Punie, Y. (2017). DigComp 2.1: The digital competence framework for citizens with eight proficiency levels and examples of use (Report No. EUR 28558 EN). Retrieved from Publications Office of the European Union website: https://doi.org/10.2760/38842
Celeux, G., & Soromenho, G. (1996). An entropy criterion for assessing the number of clusters in a mixture model. Journal of Classification, 13, 195-212. https://doi.org/10.1007/BF01246098
Chang, F.-C., Chiu, C.-H., Miao, N.-F., Chen, P.-H., Lee, C.-M., Huang, T.-F., & Pan, Y.-C. (2015). Online gaming and risks predict cyberbullying perpetration and victimization in adolescents. International Journal of Public Health, 60, 257-266. https://doi.org/10.1007/s00038-014-0643-x
Chen, L., Ho, S. S., & Lwin, M. O. (2017). A meta-analysis of factors predicting cyberbullying perpetration and victimization: From the social cognitive and media effects approach. New Media & Society, 19, 1194-1213. https://doi.org/10.1177/1461444816634037
Commission of the European Communities (2007). Communication from the Commission to the European Parliament, the Council, the European Economic and Social Committee and the Committee of the Regions: A European approach to media literacy in the digital environment. Brussels, Belgium: Commission of the European Communities.
Cooper, M. L. (1994). Motivations for alcohol use among adolescents: Development and validation of a four-factor model. Psychological Assessment, 6, 117-128. https://doi.org/10.1037/1040-3590.6.2.117
Cox, W. M., & Klinger, E. (1988). A motivational model of alcohol use. Journal of Abnormal Psychology, 97, 168-180. https://doi.org/10.1037/0021-843X.97.2.168
Crick, N. R., Casas, J. F., & Ku, H.-C. (1999). Relational and physical forms of peer victimization in preschool. Developmental Psychology, 35, 376-385. https://doi.org/10.1037/0012-1649.35.2.376
Crick, N. R., & Grotpeter, J. K. (1996). Children’s treatment by peers: Victims of relational and overt aggression. Development and Psychopathology, 8, 367-380. https://doi.org/10.1017/S0954579400007148
Cross, D., Lester, L., & Barnes, A. (2015). A longitudinal study of the social and emotional predictors and consequences of cyber and traditional bullying victimisation. International Journal of Public Health, 60, 207-217. https://doi.org/10.1007/s00038-015-0655-1
Cross, D., Shaw, T., Hadwen, K., Cardoso, P., Slee, P., Roberts, C., . . . Barnes, A. (2016). Longitudinal impact of the Cyber Friendly Schools program on adolescents’ cyberbullying behavior. Aggressive Behavior, 42, 166-180. https://doi.org/10.1002/ab.21609
Disperati, F., Canale, N., Vieno, A., Marino, C., Chieco, F., Andriolo, S., & Santinello, M. (2015). «Scopri che bevitore sei»: intervento di prevenzione online per ridurre il consumo di alcol e i problemi alcol relati [“Which type of drinker are you?”: An online prevention programme to reduce alcohol consumption and alcohol related problems]. Giornale Italiano di Psicologia, 42, 289-302. Available at https://www.rivisteweb.it/doi/10.1421/79850
Dyer, W. J., & Day, R. D. (2015). Investigating family shared realities with factor mixture modeling. Journal of Marriage and Family, 77, 191-208. https://doi.org/10.1111/jomf.12158
Erdur-Baker, Ö. (2010). Cyberbullying and its correlation to traditional bullying, gender and frequent and risky usage of internet-mediated communication tools. New Media & Society, 12, 109-125. https://doi.org/10.1177/1461444809341260
Espinoza, G., Gonzales, N. A., & Fuligni, A. J. (2013). Daily school peer victimization experiences among Mexican-American adolescents: Associations with psychosocial, physical and school adjustment. Journal of Youth and Adolescence, 42, 1775-1788. https://doi.org/10.1007/s10964-012-9874-4
Finkelhor, D., Ormrod, R. K., & Turner, H. A. (2007). Poly-victimization: A neglected component in child victimization. Child Abuse & Neglect, 31, 7-26. https://doi.org/10.1016/j.chiabu.2006.06.008
Fisher, B. W., Gardella, J. H., & Teurbe-Tolon, A. R. (2016). Peer cybervictimization among adolescents and the associated internalizing and externalizing problems: A meta-analysis. Journal of Youth and Adolescence, 45, 1727-1743. https://doi.org/10.1007/s10964-016-0541-z
Galovan, A. M., Drouin, M., & McDaniel, B. T. (2018). Sexting profiles in the United States and Canada: Implications for individual and relationship well-being. Computers in Human Behavior, 79, 19-29. https://doi.org/10.1016/j.chb.2017.10.017
Gámez-Guadix, M., Orue, I., Smith, P. K., & Calvete, E. (2013). Longitudinal and reciprocal relations of cyberbullying with depression, substance use, and problematic internet use among adolescents. Journal of Adolescent Health, 53, 446-452. https://doi.org/10.1016/j.jadohealth.2013.03.030
Giménez Gualdo, A. M., Maquilón Sánchez, J. J., & Arnaiz Sánchez, P. (2015). Usos problemáticos y agresivos de las TIC por parte de adolescentes implicados en cyberbullying [Problematic and aggressive use of ICT in adolescents involved in cyberbullying]. Revista de Investigation Educativa, 33, 335–351. https://doi.org/10.6018/rie.33.2.199841
Gini, G. (2008). Associations among overt and relational victimization and adolescents’ satisfaction with friends: The moderating role of the need for affective relationships with friends. Journal of Youth and Adolescence, 37, 812-820. https://doi.org/10.1007/s10964-007-9236-9
Gini, G., Card, N. A., & Pozzoli, T. (2018). A meta‐analysis of the differential relations of traditional and cyber‐victimization with internalizing problems. Aggressive Behavior, 44, 185-198. https://doi.org/10.1002/ab.21742
Gini, G., Marino, C., Spada M. M. (2019). The role of metacognitions and thinking styles in the negative outcomes of adolescents’ peer victimization. Violence and Victims, 34, 752-769. https://doi.org/10.1891/0886-6708.VV-D-18-00016
Gini, G., & Pozzoli, T. (2013). Bullied children and psychosomatic problems: A meta-analysis. Pediatrics, 132, 720-729. https://doi.org/10.1542/peds.2013-0614
Gini, G., Pozzoli, T., & Hymel, S. (2014). Moral disengagement among children and youth: A meta‐analytic review of links to aggressive behavior. Aggressive Behavior, 40, 56-68. https://doi.org/10.1002/ab.21502
Goldweber, A., Waasdorp, T. E., & Bradshaw, C. P. (2013). Examining the link between forms of bullying behaviors and perceptions of safety and belonging among secondary school students. Journal of School Psychology, 51, 469-485. https://doi.org/10.1016/j.jsp.2013.04.004
Gómez, P., Rial, A., Braña, T., Golpe, S., & Varela, J. (2017). Screening of problematic Internet use among Spanish adolescents: Prevalence and related variables. Cyberpsychology, Behavior, and Social Networking, 20, 259-267. https://doi.org/10.1089/cyber.2016.0262
Gradinger, P., Strohmeier, D., & Spiel, C. (2009). Traditional bullying and cyberbullying: Identification of risk groups for adjustment problems. Zeitschrift für Psychologie/Journal of Psychology, 217, 205-213. https://doi.org/10.1027/0044-3409.217.4.205
Guo, S. Y. (2016). A meta-analysis of the predictors of cyberbullying perpetration and victimization. Psychology in the Schools, 53, 432-453. https://doi.org/10.1002/pits.21914
Hasebrink, U., Livingstone, S., Haddon, L., & Ólafsson, K. (2009). Comparing children’s online opportunities and risks across Europe: Cross-national comparisons for EU Kids Online. London, UK: EU Kids Online.
Hsieh, Y.-P., Wei, H.-S., Hwa, H.-L., Shen, A. C.-T., Feng, J.-Y., & Huang, C.-Y. (2018). The effects of peer victimization on children’s Internet addiction and psychological distress: The moderating roles of emotional and social intelligence. Journal of Child and Family Studies, 28, 2487-2498. https://doi.org/10.1007/s10826-018-1120-6
Hug, T. (2012). Media competence and visual literacy-towards considerations beyond literacies. Periodica Polytechnica Social and Management Sciences, 20, 115-125. https://doi.org/10.3311/pp.so.2012-2.06
Jia, J., Li, D., Li, X., Zhou, Y., Wang, Y., Sun, W., & Zhao, L. (2018). Peer victimization and adolescent Internet addiction: The mediating role of psychological security and the moderating role of teacher-student relationships. Computers in Human Behavior, 85, 116-124. https://doi.org/10.1016/j.chb.2018.03.042
Ke, G. N., & Wong, S. F. (2018). A healthy mind for problematic internet use. Cyberpsychology, Behavior, and Social Networking, 21, 637-645. https://doi.org/10.1089/cyber.2018.0072
Király, O., Urbán, R., Griffiths, M. D., Ágoston, C., Nagygyörgy, K., Kökönyei, G., & Demetrovics, Z. (2015). The mediating effect of gaming motivation between psychiatric symptoms and problematic online gaming: An online survey. Journal of Medical Internet Research, 17(4), e88. https://doi.org/10.2196/jmir.3515
Koltay, T. (2011). The media and the literacies: Media literacy, information literacy, digital literacy. Media Culture Society, 33, 211-221. https://doi.org/10.1177/0163443710393382
Kowalski, R. M., Giumetti, G. W., Schroeder, A. N., & Lattanner, M. R. (2014). Bullying in the digital age: A critical review and meta-analysis of cyberbullying research among youth. Psychological Bulletin, 140, 1073-1137. https://doi.org/10.1037/a0035618
Kumazaki, A., Suzuki, K., Katsura, R., Sakamoto, A., & Kashibuchi, M. (2011). The effects of netiquette and ICT skills on school-bullying and cyber-bullying: The two-wave panel study of Japanese elementary, secondary, and high school students. Procedia – Social and Behavioral Sciences, 29, 735-741. https://doi.org/10.1016/j.sbspro.2011.11.299
Lenhart, A., Duggan, M., Perrin, A., Stepler, R., Rainie, H., & Parker, K. (2015). Teens, social media & technology overview 2015: Smartphones facilitate shifts in communication landscape for teens. Retrieved from Pew Research Center website: https://www.pewinternet.org/2015/04/09/teens-social-media-technology-2015/
Leung, L., & Lee, P. S. N. (2012). The influences of information literacy, internet addiction and parenting styles on internet risks. New Media & Society, 14, 117-136. https://doi.org/10.1177/1461444811410406
Livingstone, S. (2004). Media literacy and the challenge of new information and communication technologies. The Communication Review, 7, 3-14. https://doi.org/10.1080/10714420490280152
Lubke, G., & Muthén, B. O. (2007). Performance of factor mixture models as a function of model size, covariate effects, and class-specific parameters. Structural Equation Modeling: A Multidisciplinary Journal, 14, 26-47. https://doi.org/10.1080/10705510709336735
Marino, C. (2018). Quality of social media use may matter more than frequency of use for adolescents’ depression. Clinical Psychological Science, 6, 455. https://doi.org/10.1177/2167702618771979
Marino, C., Mazzieri, E., Caselli, G., Vieno, A., & Spada, M. M. (2018). Motives to use Facebook and problematic Facebook use in adolescents. Journal of Behavioral Addictions, 7, 276-283. https://doi.org/10.1556/2006.7.2018.32
Marino, C., Vieno, A., Moss, A. C., Caselli, G., Nikčević, A. V., & Spada, M. M. (2016). Personality, motives and metacognitions as predictors of problematic Facebook Use in university students. Personality and Individual Differences, 101, 70-77. https://doi.org/10.1016/j.paid.2016.05.053
Martínez-Ferrer, B., Moreno, D., & Musitu, G. (2018). Are adolescents engaged in the problematic use of social networking sites more involved in peer aggression and victimization? Frontiers in Psychology, 9, article 801. https://doi.org/10.3389/fpsyg.2018.00801
Meerkerk, G. J., van den Eijnden, R. J. J. M., Vermulst, A. A., & Garretsen, H. F. L. (2009). The Compulsive Internet Use Scale (CIUS): Some psychometric properties. CyberPsychology & Behavior, 12, 1-6. https://doi.org/10.1089/cpb.2008.0181
Mesch, G. S. (2009). Parental mediation, online activities, and cyberbullying. CyberPsychology & Behavior, 12, 387-393. https://doi.org/10.1089/cpb.2009.0068
Mishna, F., Khoury-Kassabri, M., Gadalla, T., & Daciuk, J. (2012). Risk factors for involvement in cyber bullying: Victims, bullies and bully–victims. Children and Youth Services Review, 34, 63-70. https://doi.org/10.1016/j.childyouth.2011.08.032
Mitchell, K. J., Finkelhor, D., Jones, L. M., & Wolak, J. (2010). Use of social networking sites in online sex crimes against minors: An examination of national incidence and means of utilization. Journal of Adolescent Health, 47, 183-190. https://doi.org/10.1016/j.jadohealth.2010.01.007
Modecki, K. L., Minchin, J., Harbaugh, A. G., Guerra, N. G., & Runions, K. C. (2014). Bullying prevalence across contexts: A meta-analysis measuring cyber and traditional bullying. Journal of Adolescent Health, 55, 602-611. https://doi.org/10.1016/j.jadohealth.2014.06.007
Molenaar, P. C. M., & Campbell, C. G. (2009). The new person-specific paradigm in psychology. Current Directions in Psychological Science, 18, 112–117. https://doi.org/10.1111/j.1467-8721.2009.01619.x
Müller, C. R., Pfetsch, J., & Ittel, A. (2014). Ethical media competence as a protective factor against cyberbullying and cybervictimization among German school students. Cyberpsychology, Behavior, and Social Networking, 17, 644-651. https://doi.org/10.1089/cyber.2014.0168
Muthén, L. K., & Muthén, B. O. (1998-2017). Mplus user’s guide (8th ed.). Los Angeles, CA: Muthén & Muthén.
Nansel, T. R., Overpeck, M., Pilla, R. S., Ruan, W. J., Simons-Morton, B., & Scheidt, P. (2001). Bullying behaviors among US youth: Prevalence and association with psychosocial adjustment. JAMA, 285, 2094-2100. https://doi.org/10.1001/jama.285.16.2094
Navarro, R., Serna, C., Martínez, V., & Ruiz-Oliva, R. (2013). The role of Internet use and parental mediation on cyberbullying victimization among Spanish children from rural public schools. European Journal of Psychology of Education, 28, 725-745. https://doi.org/10.1007/s10212-012-0137-2
Nesi, J., Choukas-Bradley, S., & Prinstein, M. J. (2018). Transformation of adolescent peer relations in the social media context: Part 2—application to peer group processes and future directions for research. Clinical Child and Family Psychology Review, 21, 295-319. https://doi.org/10.1007/s10567-018-0262-9
Nocentini, A., Calmaestra, J., Schultze-Krumbholz, A., Scheithauer, H., Ortega, R., & Menesini, E. (2010). Cyberbullying: Labels, behaviours and definition in three European countries. Journal of Psychologists and Counsellors in Schools, 20, 129-142. https://doi.org/10.1375/ajgc.20.2.129
Nylund, K. L., Asparouhov, T., & Muthén, B. O. (2007). Deciding on the number of classes in latent class analysis and growth mixture modeling: A Monte Carlo simulation study. Structural Equation Modeling, 14, 535-569. https://doi.org/10.1080/10705510701575396
Olweus, D. (2012). Cyberbullying: An overrated phenomenon? European Journal of Developmental Psychology, 9, 520-538. https://doi.org/10.1080/17405629.2012.682358
Ortega-Ruiz, R., Del Rey, R., & Casas, J. A. (2012). Knowing, building and living together on Internet and social networks: The ConRed cyberbullying prevention program. International Journal of Conflict and Violence, 6, 302-312. https://doi.org/10.4119/UNIBI/ijcv.250
Palladino, B. E., Nocentini, A., & Menesini, E. (2015). Psychometric properties of the Florence CyberBullying-CyberVictimization Scales. Cyberpsychology, Behavior, and Social Networking, 18, 112-119. https://doi.org/10.1089/cyber.2014.0366
Park, S., Na, E.-Y., & Kim, E.-M. (2014). The relationship between online activities, netiquette and cyberbullying. Children and Youth Services Review, 42, 74-81. https://doi.org/10.1016/j.childyouth.2014.04.002
Pieschl, S. (2018). Ist Medienkompetenz ein protektiver Faktor gegen problematische Mediennutzung? [Is media competence a protective factor against problematic media use?]. In O.D. Kothgassner & A. Felnhofer (Eds.), Klinische Cyberpsychologie und Cybertherapie (pp. 180-188). Stuttgart, Germany: UTB.
Reijntjes, A., Kamphuis, J. H., Prinzie, P., & Telch, M. J. (2010). Peer victimization and internalizing problems in children: A meta-analysis of longitudinal studies. Child Abuse & Neglect, 34, 244-252. https://doi.org/10.1016/j.chiabu.2009.07.009
Salmivalli, C., Sainio, M., & Hodges, E. V. E. (2013). Electronic victimization: Correlates, antecedents, and consequences among elementary and middle school students. Journal of Clinical Child & Adolescent Psychology, 42, 442-453. https://doi.org/10.1080/15374416.2012.759228
Scott, C. F., Bay-Cheng, L. Y., Prince, M. A., Nochajski, T. H., & Collins, R. L. (2017). Time spent online: Latent profile analyses of emerging adults' social media use. Computers in Human Behavior, 75, 311-319.
https://doi.org/10.1016/j.chb.2017.05.026
Siciliano, V., Bastiani, L., Mezzasalma, L., Thanki, D., Curzio, O., & Molinaro, S. (2015). Validation of a new Short Problematic Internet Use Test in a nationally representative sample of adolescents. Computers in Human Behavior, 45, 177-184. https://doi.org/10.1016/j.chb.2014.11.097
Spada, M. M. (2014). An overview of problematic Internet use. Addictive Behaviors, 39, 3-6. https://doi.org/10.1016/j.addbeh.2013.09.007
Stodt, B., Wegmann, E., & Brand, M. (2015). Geschickt geklickt?! Zum Zusammenhang von Internetnutzungskompetenzen, Internetsucht und Cybermobbing bei Jugendlichen und jungen Erwachsenen [Skillful clicked. On the relation of internet use competence, internet addiction and cyberbullying among adolescents and young adults] (LfM-Schriftenreihe Medienforschung, 78). Leipzig, Germany: Vistas.
Storch, E. A., & Ledley, D. R. (2005). Peer victimization and psychosocial adjustment in children: Current knowledge and future directions. Clinical Pediatrics, 44, 29-38.
https://doi.org/10.1177/000992280504400103
Sturge-Apple, M. L., Davies, P. T., Cummings, E. M. (2010). Typologies of family functioning and children’s adjustment during the early school years. Child Development, 81, 1320-1335. https://doi.org/10.1111/j.1467-8624.2010.01471.x
Sumter, S. R., & Baumgartner, S. E. (2017). Psychosomatic complaints in adolescence: Untangling the relationship between offline and online peer victimization, psychosomatic complaints and social support. European Journal of Developmental Psychology, 14, 399-415. https://doi.org/10.1080/17405629.2016.1215980
Ttofi, M. M., Farrington, D. P., Lösel, F., & Loeber, R. (2011). Do the victims of school bullies tend to become depressed later in life? A systematic review and meta-analysis of longitudinal studies. Journal of Aggression, Conflict and Peace Research, 3, 63-73. https://doi.org/10.1108/17596591111132873
Valkenburg, P. M., & Peter, J. (2009). Social consequences of the Internet for adolescents: A decade of research. Current Directions in Psychological Science, 18, 1-5. https://doi.org/10.1111/j.1467-8721.2009.01595.x
van Geel, M., Vedder, P., & Tanilon, J. (2014). Relationship between peer victimization, cyberbullying, and suicide in children and adolescents: A meta-analysis. JAMA Pediatrics, 168, 435-442. https://doi.org/10.1001/jamapediatrics.2013.4143
Vandebosch, H., & Van Cleemput, K. (2009). Cyberbullying among youngsters: Profiles of bullies and victims. New Media & Society, 11, 1349-1371. https://doi.org/10.1177/1461444809341263
Waasdorp, T. E., & Bradshaw, C. P. (2011). Examining student responses to frequent bullying: A latent class approach. Journal of Educational Psychology, 103, 336-352. https://doi.org/10.1037/a0022747
Waasdorp, T. E., & Bradshaw, C. P. (2015). The overlap between cyberbullying and traditional bullying. Journal of Adolescent Health, 56, 483-488. https://doi.org/10.1016/j.jadohealth.2014.12.002
Wachs, S., Whittle, H. C., Hamilton-Giachritsis, C., Wolf, K. D., Vazsonyi, A. T., & Junger, M. (2018). Correlates of mono- and dual-victims of cybergrooming and cyberbullying: Evidence from four countries. Cyberpsychology, Behavior, and Social Networking, 21, 91-98. https://doi.org/10.1089/cyber.2016.0733
Walrave, M., & Heirman, W. (2011). Cyberbullying: Predicting victimisation and perpetration. Children & Society, 25, 59-72. https://doi.org/10.1111/j.1099-0860.2009.00260.x
Wang, J., Iannotti, R. J., Luk, J. W., & Nansel, T. R. (2010). Co-occurrence of victimization from five subtypes of bullying: Physical, verbal, social exclusion, spreading rumors, and cyber. Journal of Pediatric Psychology, 35, 1103-1112. https://doi.org/10.1093/jpepsy/jsq048
Wölfer, R., Schultze-Krumbholz, A., Zagorscak, P., Jäkel, A., Göbel, K., & Scheithauer, H. (2014). Prevention 2.0: Targeting cyberbullying @ school. Prevention Science, 15, 879-887. https://doi.org/10.1007/s11121-013-0438-y
Zhou, Z., Tang, H., Tian, Y., Wei, H., Zhang, F., & Morrison, C. M. (2013). Cyberbullying and its risk factors among Chinese high school students. School Psychology International, 34, 630-647. https://doi.org/10.1177/0143034313479692
Zsila, Á., Orosz, G., Király, O., Urbán, R., Ujhelyi, A., Jármi, É., . . . Demetrovics, Z. (2018). Psychoactive substance use and problematic internet use as predictors of bullying and cyberbullying victimization. International Journal of Mental Health and Addiction, 16, 466-479. https://doi.org/10.1007/s11469-017-9809-0
Editorial Record:
First submission received:
February 22, 2019
Revisions received:
July 16, 2019
October 1, 2019
Accepted for publication:
October 7, 2019
Editor in charge:
Michel Walrave
Introduction
Peer victimization refers to any aggression against a peer and is one of the most common problems that children and adolescents experience during their school career. About one-third of youth reports experiencing various forms of peer victimization (Nansel et al., 2001; Storch & Ledley, 2005), which are often linked to serious health, psycho-social, and academic problems as documented by several meta-analyses (Gini & Pozzoli, 2013; Reijntjes, Kamphuis, Prinzie, & Telch, 2010; Ttofi, Farrington, Lösel, & Loeber, 2011; van Geel, Vedder, & Tanilon, 2014). So-called traditional (or offline) victimization happens in the school context where it takes various forms—both direct/overt (e.g., physical assaults, threatening behavior) and indirect/relational (e.g., psychological and social strategies such as exclusion and rumor spreading) (Crick, Casas, & Ku, 1999). Moreover, especially in the last decade scholars have dedicated a growing body of research to another form of peer victimization, namely peer cyber-victimization (also called electronic or online or Internet victimization; henceforth “cyber-victimization”) (e.g., Bauman, Cross, & Walker, 2013; Nocentini et al., 2010). Cyber-victimization refers to peer victimization received via information and communication technologies (ICT). Examples of cyber-victimization include nasty comments received via email or text message, as well as humiliation, threats, or exclusion through social networks, forums, or chat rooms (Fisher, Gardella, & Teurbe-Tolon, 2016; Kowalski, Giumetti, Schroeder, & Lattanner, 2014). Experiences of cyber-victimization tend to increase from early to middle adolescence probably due to an increased Internet usage during this period of life (Lenhart et al., 2015). Studies that explicitly compare traditional forms of peer victimization with cyber-victimization and their different associations with outcomes and personal characteristics of targeted youth are still scarce (Gini, Card, & Pozzoli, 2018). Furthermore, quite paradoxically if one considers the role of ICT in cyber-victimization and in adolescents’ lives in general, very little is still known about the “online life” of adolescents who experience different forms of peer victimization. The current study was designed with the aim of analyzing—with a person-centered approach—the differences in Internet use and online behavior of adolescents who suffer different forms of peer victimization compared to their non-victimized peers.
Overlap Between Traditional and Cyber-Victimization
In the peer victimization literature, it has been debated whether cyber-victimization is a new phenomenon or it is just another form of victimization by peers (Olweus, 2012). Similarities and differences between the two forms of peer victimization have been highlighted. Cyber-victimization potentially differs from traditional victimization in some respects. In particular, the nature of ICT allows cyber-aggression to occur more covertly, to spread more rapidly among a wider audience, and to persist for longer across time and space, than is the case for traditional victimization. However, significant overlap between traditional and cyber-victimization has been confirmed in recent meta-analyses (Gini et al., 2018; Kowalski, Giumetti et al., 2014; Modecki, Minchin, Harbaugh, Guerra, & Runions, 2014), which has led to the conclusion that targets of cyber-victimization “also tended to report high levels of TV [traditional victimization], indicating that many individuals may be targets of bullying behavior in both face-to-face and online contexts” (Kowalski, Giumetti et al., 2014, p. 1124). However, it should be noted that the overlap is not complete, so some youth are only or mainly targets of cyber-victimization (Olweus, 2012).
The majorities of the studies that have analyzed and compared traditional and cyber-victimization have based their conclusions about the similarities and differences between the two forms on the degree to which youth’s scores in the different forms overlap (i.e., correlate) and, to a lesser extent, to what extent the correlates of traditional and cyber-victimization are the same (see Gini et al., 2018 for a meta-analysis). While this approach provides useful information, especially about the interindividual variations of the variables of interest (Molenaar & Campbell, 2009), authors in the field of peer victimization (e.g., Bradshaw, Waasdorp, & Brennan, 2013; Goldweber, Waasdorp, & Bradshaw, 2013), as well as of Internet use (e.g., Scott, Bay-Cheng, Prince, Nochajski, & Collins, 2017), are increasingly recommending the use of complementary approaches. It has been suggested, for example, that person-centered approaches enable researchers to capture “qualitatively different profiles of study variables that are not anchored on a linear or continuous scale” (Sturge-Apple, Davies, & Cummings, 2010, p. 1320), as is the case of different forms of victimization. Adopting a person-centered approach, researchers have indeed shown that it is usually possible to identify multiple classes of peer victimization that are differentially related to personal correlates and outcomes. For example, Wang, Iannotti, Luk, and Nansel (2010) conducted latent class analysis on victimization by physical, verbal, social exclusion, spreading rumors, and cyberbullying, reporting three latent classes: a “non-victim” class, a “verbal/relational victims” class and a small (about 3.5% of the sample) “all-types victims” class. Increased co-occurrence of peer victimization types was found to be associated with higher levels of depression, frequency of injuries, and medicine use. Similarly, in Bradshaw and colleagues’ (2013) study employing latent class analysis the majority of adolescents belonged to a “low victimization” category, while a group of students (about 10% of the sample) reported experiencing all forms of peer victimization, including cyber-victimization, and they were more likely to report internalizing problems. More recently, in a large sample of adolescents in the United States, Barboza (2015) examined the cross-classification of bullying and cyberbullying victimization simultaneously with latent class analysis and identified four categories of victims: the large majority of students were not victimized; about 8% of adolescents were victims of traditional victimization (overt and relational) but not of cyber-victimization; another group of students (about 11%) were classified as being victims of traditional forms (both relational and verbal victimization) and cyber-victimization; and a small group (about 3%) were highly victimized by both traditional victimization and cyber-victimization. Comparisons among these victim-groups showed that the highly victimized class had the strongest association with measures of school maladjustment and academic risk. Moreover, in another study with latent class analysis Brown, Demaray, Tennant, and Jenkins (2017) found that adolescents who experienced even low levels of cyber and traditional victimization (i.e., dual victimization) reported more social and emotional problems than non-victimized students. In one of the few studies conducted with adolescents not living in the United States, Salmivalli, Sainio, and Hodges (2013) have identified (based on standard cut-offs) four groups of students in Finland, including non-victims, traditional-only victims, electronic-only victims, and traditional and electronic victims. Longitudinally, they have found some evidence in support of cumulative risk models (Finkelhor, Ormrod, & Turner, 2007); indeed, victims of both traditional and cyber-victimization showed the most increases in depression over time. Similarly, among Dutch adolescents, Sumter and Baumgartner (2017) have found three distinct classes of victims beyond non-victims: traditional victims (called by the authors “offline” victims), cyber-victims (called “online” victims) and dual victims. Both traditional and dual victims were found to report more psychosomatic complaints than non-victims.
Overall, these results confirm the importance of untangling the relationship between traditional and cyber-victimization and support the claim that experiencing multiple forms of peer victimization (sometimes called “polyvictimization”; Finkelhor et al., 2007) may have stronger influences in targets’ well-being and adjustment than single victimization. However, the number of studies that have so far described different patterns of peer victimization such as traditional victimization only versus cyber-victimization only or both is still quite limited. Moreover, it is still necessary to understand how these types of victims differ from each other in a variety of personal characteristics, especially as regards their motives for Internet use, frequency of use, as well as problematic and ethical Internet use. Investigating potential differences between different groups of victims can have important theoretical advantages by, for example, lending empirical support to broader theories about Internet use and abuse, such as the Social Compensation Theory (Valkenburg & Peter, 2009) or the Generalized Problematic Internet Use model (Caplan, 2010; Marino et al., 2016), and testing whether these theories can be also applied to the specific context of adolescents’ peer victimization. For example, the Social Compensation Theory would suggest that (some groups of) victimized adolescents could use the Internet to adjust—in a maladaptive way—to their victimization problems, by escaping from unwanted moods or distress. However, so far, no explicit tests of motives for Internet use in victimized youth have been published. Furthermore, from a practical perspective, distinguishing different profiles of victims and understanding how they differ in specific aspects of their online life can also have important implications for designing more nuanced intervention programs that take into account the possible differences among these victim groups.
Peer Victimization and Internet Usage
The first and most understandable link between Internet use and peer victimization experiences that occur online is that increased use (i.e., higher time spent online and higher engagement in a variety of online activities) is significantly associated with higher risk for cyber-victimization. Not surprisingly, recent meta-analyses have indeed showed that low frequency of technology use is among the strongest protective factors against cyber-victimization (Chen, Ho, & Lwin, 2017; Guo, 2016). Conversely, adolescents with greater use of social network sites (Giménez Gualdo, Maquilón Sánchez, & Arnaiz Sánchez, 2015; Navarro, Serna, Martínez, & Ruiz-Oliva, 2013) and online gaming (Chang et al., 2015) have shown a greater probability of experiencing cyber-victimization. More in general, higher Internet use by adolescents is associated with increased probability to encounter risky situations online (Erdur-Baker, 2010; Gómez, Rial, Braña, Golpe, & Varela, 2017; Hasebrink, Livingstone, Haddon, & Ólafsson, 2009; Mesch, 2009; Mishna, Khoury-Kassabri, Gadalla, & Daciuk, 2012; Mitchell, Finkelhor, Jones, & Wolak, 2010; Walrave & Heirman, 2011; Zhou et al., 2013). However, stopping the use of ICT among adolescents is obviously not a viable tool for preventing cyber-victimization because of the high importance of adolescents’ online activities for social relationships, civic engagement, and information needs. Yet, beyond frequency of use, it has been proposed that the quality of ICT use may also matter for adolescents’ adjustment (Marino, 2018). In fact, an increasing number of studies have recently shown that a positive association exists between experiencing cyber-victimization and reporting a poor quality of Internet use, in terms of problematic and risky behaviors online. For example, recent studies (e.g., Boniel-Nissim, & Sasson, 2018; Gámez-Guadix, Orue, Smith, & Calvete, 2013; Gómez et al., 2017; Vandebosch & Van Cleemput, 2009) have shown that youth who are cyber-victims also report higher levels of problematic Internet use, defined as the “use of the Internet that creates psychological, social, school and/or work difficulties in a person’s life” (Beard & Wolf, 2001, p. 378). In line with the Social Compensation Theory (Valkenburg & Peter, 2009), Boniel-Nissim and Sasson (2018) argued that cyber-victims may tend to use Internet as a maladaptive strategy to escape from unwanted moods or distress due to victimization. In doing so, they might be more exposed to harassment and hostile messages (Leung & Lee, 2012), thus encountering further negative experiences in daily life.
Similarly, regarding traditional victimization, in a recent study that adopted a variable-centered approach, Martínez-Ferrer, Moreno, and Musitu (2018) have found a positive association of peer victimization (both overt and relational forms) with problematic use of social network sites in a sample of Spanish adolescents. The authors have discussed their finding in relation to the functions of social network sites for adolescents, who are attracted by such sites because they enable building support networks beyond geographical proximity. It is therefore “possible that the SNS constitute, in turn, a support-seeking tool for adolescents victimized by their peer group” (Martínez-Ferrer et al., 2018, p. 10). However, until very recently, a still limited number of studies have analyzed the relationship between traditional victimization and problematic Internet use (Hsieh et al., 2018; Jia et al., 2018; Martínez-Ferrer et al., 2018). Even more apparently, studies that have explicitly compared cyber-victims and traditional victims in their potentially problematic use of the Internet are still very limited. For example, Zsila and colleagues (2018) have found that cyber-victims reported higher levels of problematic Internet use than traditional victims, who in turn scored higher than non-victims. In other terms, it may be possible that adolescents who are victimized online engage in a wide range of online activities to escape from negative feelings whereas adolescents who are victimized at school mainly engage in online social network sites to seek social-emotional support and inclusion and to relief their emotional distress. On the other hand, problematic Internet use has been conceptualized as a form of maladaptive self-regulatory strategy (Spada, 2014), in that it can represent a way of coping with life’s difficulties that takes the form of problem solving through avoidance. Therefore, adolescents may problematically use the Internet as a strategy to diminish psychological distress and the negative emotions that stem from experiences of victimization (Hsieh et al., 2018).
However, no study, so far, has explicitly analyzed the psychological motives for using Internet expressed by adolescents who are victimized at school and/or online. Understanding motives that underlie youth’s use and misuse of the Internet and social media, and how such motives differ across victim groups, is paramount to the appreciation of the psychological underpinnings of ICT use among adolescents and to the development of more nuanced prevention and intervention programs. Indeed, psychological motives are commonly considered preferential targets of prevention programs (e.g., Marino, Mazzieri, Caselli, Vieno, & Spada, 2018) as they represent the proximal factors for engaging in problematic behaviors (Cooper, 1994). Studies on motives in the literature about problematic behaviors are theoretically grounded on the traditional motivational model of alcohol use (Cox & Klinger, 1988). Briefly, according to this theory, expectations to achieve certain desired effects drive adolescents’ problematic behaviors, including Internet (Bischof-Kastner, Kuntsche, & Wolstein, 2014) and social media use (Marino et al., 2018). Such expectations descend from the mixture of individual differences (e.g., genetic inclinations, personality traits), contextual factors (e.g., socio-economic status, Internet availability), and cognitive effects (e.g., thoughts, perceptions, and memories) which, in turn, lead adolescents to behave accordingly. In this model, four concise motives for Internet use, namely enhancement, social, coping, and conformity, are obtained by crossing two dimensions of expected effects, that is, positive or negative valence (enhancing or reducing positive or negative feelings), and internal or external source (dealing with one’s own sensations or significant others). Bischof-Kastner and colleagues (2014) showed that the emotion-regulation motives for using Internet (i.e. coping and enhancement) are more frequent among problematic Internet users than among low-risk adolescents who engage in social online interactions. The so far limited literature on motives for using Internet has focused on the general population of adolescents and young adults. To our knowledge, no study has investigated which motives for using Internet are more prevalent among youth who are victimized, nor whether traditional victims and cyber-victims differ in such motives. Relatedly to the discussion about problematic Internet use in peer victimized adolescents, knowing which motives drive victims’ use of ICT may enhance our understanding of their online experience and might be useful for cyber-victimization prevention efforts.
Finally, another way to conceptualize the quality of Internet use is media competence (also called “media literacy”), that is, a multidimensional ability to use ICT effectively, to share contents, and to identify and avoid negative or harmful contents (Hug, 2012). Several dimensions of media competency have been discussed, such as decoding, evaluating, analyzing and producing media (Aufderheide, 1993) or the ability to access, understand, critically evaluate media contents and to create media communication (Commission of the European Communities, 2007), or information and data literacy, communication and collaboration, digital content creation, safety, and problem solving (Carretero, Vuorikari, & Punie, 2017), with the critical aspect of media reception and production being stressed (Livingstone, 2004; Koltay, 2011). Regarding online aggressive behaviors, among the different components of media competence, the ethical dimension has been proposed as the most relevant (Müller, Pfetsch, & Ittel, 2014). Ethical media competence has been defined as “the knowledge, motivation, and ability for computer-mediated interpersonal communication that conforms to the law and to social norms (e.g., the ‘golden rule’)” (Müller et al., 2014, p. 645). This includes knowledge about legal rules and social norms in computer-mediated communication, skills for socially responsible computer-mediated communication, and motivation to adopt socially responsible behavior in computer-mediated communication (Müller et al., 2014). So far, ethical behavior online was seldom studied in relation to cyberbullying victimization (Pieschl, 2018). Netiquette – the sense of morality and ethical values in the online world – was negatively linked to cyberbullying and cyber-victimization over and above internet use and social networking use (Park, Na, & Kim, 2014). Netiquette also had a moderating influence on cyberbullying perpetration among older adolescents: higher ICT skills increased cyberbullying when netiquette was low but not when netiquette was high (Kumazaki, Suzuki, Katsura, Sakamoto, & Kashibuchi, 2011). Perpetrators and victims of cyberbullying reported higher competencies in media production and interaction but less self-regulation (self-restriction of internet usage time) in comparison to non-involved peers (Stodt, Wegmann, & Brand, 2015). In sum, there is first evidence that dimensions related to ethical media competence is negatively linked to cyberbullying perpetration.
While the existence of a negative association between ethical media competence and cyber-aggression is straightforward, Müller and colleagues (2014) showed that ethical media competence can also act as a protective factor against cyber-victimization and concluded that adolescents who responsibly use ICT might be less vulnerable to becoming a victim because, for example, they might disclose less personal information. Conversely, lack of (or less) ethical media competence might characterize youth who are victimized online (Müller et al., 2014; Park et al., 2014; in contrast: Stodt et al., 2015). To the best of our knowledge, no study so far has compared ethical media competence in different profiles of adolescent victims.
The Current Study
In sum, the current study was aimed at analyzing how different profiles of victims differ from each other and from non-victimized peers in their motives for using Internet, their problematic Internet use and ethical media use. Differentiating groups of involved adolescents based on their behavioral patterns and motivational/behavioral correlates deepens our understanding of victims and can help to provide more appropriate intervention measures. First, based on the studies reviewed above that have used latent class analysis, we expected to find also in our sample three different groups of victims, namely a group of youth who are victims only of traditional peer victimization, a group of cyber-victims, and a group of so-called “dual victims”, that is, adolescents who experience high levels of both forms of peer victimization. Second, regarding youth’s motives and use of Internet, it was expected that adolescents who are not victimized showed the highest adjustment and, therefore, the least problematic use of the Internet. In keeping with cumulative risk models and the concept of polyvictimization (Finkelhor et al., 2007), we also hypothesized that dual victims, that is, adolescents who are harassed both at school and online, would show a stronger pattern of problematic and risky use of ICT. For example, we hypothesized that dual victims would use ICT more intensively and for less adaptive motives (i.e., coping and conformity), would have higher levels of problematic Internet use and would show lower levels of ethical media use. This would be consistent with previous studies showing lower adjustment and well-being in this type of victims, compared to both non-victims and victims of traditional victimization only (e.g., Barboza, 2015; Brown et al., 2017; Salmivalli et al., 2013). As far as the direct comparison of traditional victims and cyber-victims is concerned, it is more difficult to develop specific hypotheses, because the literature that compares the two forms of peer victimization is still limited, especially regarding the characteristics of these victim groups in terms of ICT use and problematic Internet use. Therefore, we should consider these comparisons as mostly exploratory. Nonetheless, we expected cyber-victims to share some problematic online behaviors with dual victims. In both cases, indeed, a more frequent use of ICT (or at least of specific websites and activities, such as particular types of online games) and the use of the Internet that is more problematic and less competent may be “part of the problem” of their victimization from peers. Conversely, traditional victims live their negative experiences with peers in their everyday offline life and may, therefore, show problematic behaviors online to a lesser extent than cyber-victims and dual victims. However, traditional victims may also look for online activities as a way to escape their suffering and their feeling of loneliness or social failure, to find support from others, or to fit in and be accepted by the peer group (Boniel-Nissim & Sasson, 2018). If this were the case, we would expect traditional victims to endorse more coping and conformity motives and to use the Internet more problematically compared to non-victimized peers.
Method
Participants
Data used in the current study are drawn from a larger project about offline and online risk factors for adolescents’ adjustment and well-being (Gini, Marino, & Spada, 2019). The participants were 1377 adolescents (49.5% females, age: M = 16.13, SD = 1.27 years, range: 14-18) for whom signed active consent from parents was obtained (85% of the contacted parents agreed) and who assented to participate (none of the adolescents with parental consent refused to participate). The participant students attended public secondary schools (representative of public schools in that region of the country, e.g., lyceum, technical and vocational schools) randomly selected from schools located in a Northern-East region of Italy. All contacted schools agreed to participate in the study. In each school students from grades 9-12 were invited.
Measures
Traditional victimization. Traditional victimization by peers was measured with an Italian scale (Gini, 2008), composed of 12 items derived from the Social Experience Questionnaire (Crick & Grotpeter, 1996). Six items measured overt victimization enacted towards the respondent by other schoolmates (e.g., “Other students have threatened me,” “Other students have physically attacked me”), and six items measured relational victimization (e.g., “Other students have spread false stories about me,” “Other students didn’t talk to me to make me feel excluded”). Participants were asked to rate the frequency with which they received each aggressive behavior from peers during the current school year. The items were rated on a 5-point scale (from 1 = “never” to 5 = “almost always”). The Cronbach’s alpha of the scale’s scores in this sample was .68 (95% CI .65-.71) for overt victimization and .78 (95% CI .76-.80) for relational victimization. In the whole sample, the average scores were M = 1.34 (SD = .39) for overt victimization and M = 1.53 (SD = .55) for relational victimization.
Cyber-victimization. The Florence Cyberbullying-Cybervictimization Scale (Palladino, Nocentini, & Menesini, 2015) has been developed and validated for Italian adolescents. For the purpose of the current study, we used the 14 items of the cyber-victimization scale that asks participants how often in the current school year they have suffered different kinds of aggressive behavior by other peers online (such as receiving threatening and insulting text messages, receiving videos/photos of embarrassing or personal situations, or being excluded from an online group in chats, forum, Facebook groups). Each item is evaluated on a 5-point scale from 1 = “never” to 5 = “several times a week”. Internal consistency for the current sample was .78 (95% CI .76-.80). The mean level for cyber-victimization was M = 1.19 (SD = .24).
Problematic Internet use. Problematic Internet use was assessed through the Short Problematic Internet Use Test for Italian adolescents (Siciliano et al., 2015). The instrument includes 6 items, rated on a 5-point scale (from 1 “never” to 5 “very often”), which cover several criteria for problematic Internet use described by Meerkerk, van den Eijnden, Vermulst, and Garretsen (2009): loss of control (e.g., “Do you find that you are staying online longer than you intended?”), preoccupation/salience (e.g., “Have you neglected homework because you are spending more time online?”), conflicts (e.g., “Have you been reprimanded by your parents or your friends about how much time you spend online?”), and withdrawal symptoms and coping (e.g., “Do you feel nervous when you are offline and is that feeling relieved when you do go back online?”). The Cronbach’s alpha for the scale in this sample was .76 (95% CI .74-.78).
Motives for using Internet. The Italian version (Marino et al., 2018) of the Internet Motives Questionnaire for Adolescents (Bischof-Kastner et al., 2014) was used to assess four types of motives. The participants were asked how often they used the Internet for different motivations, thinking of all the times they have been online during the current school year. The scale includes four motives: coping (e.g., “To forget your worries”), conformity (e.g., “To be liked by others”), enhancement (e.g., “Because it is exciting”), and social motive (e.g., “To come into contact with others”). The questionnaire contains 16 items rated on a 5-point scale (ranging from 1 = “never or almost never” to 5 = “always or almost always”), so that higher scores indicate higher endorsement of each motive. The Cronbach’s alpha for each of the four motives was as follows: .87 [95% CI: 0.85-0.88] for coping; .70 [95% CI: 0.67-0.73] for conformity; .70 [95% CI: 0.67-0.72] for enhancement; and .82 [95% CI: 0.80-0.83] for social motive.
Ethical media use. Ethical media use was assessed using the Ethical Media Competence Scale (Müller et al., 2014) that was forward and backward translated for the current study and covers a set of 18 behaviors in computer-mediated peer communication. Sample items are the following: “Sometimes I use an online account with a different name, so that other people believe I am a different person,” (reverse coded) and “I treat others online as I would like to be treated by them.” Students rated the items on a 4-point Likert scale ranging from 1 = “does not apply at all” to 4 = “fully applies.” Answers were averaged to form a score of ethical media use, with higher scores indicating a use of digital media that is more respectful of people and rules. The Cronbach’s alpha for the scale in this sample was .75 (95% CI .72-.77).
Online activities. Adolescents were asked to rate the frequency of different activities on the Internet during a weekday (Siciliano et al., 2015). Five items asked about the following online activities: chatting (e.g., on WhatsApp, Skype), using Facebook, playing ability games (e.g., Texas Hold’em, Sudoku, billiard), playing role-playing games (e.g., adventure multiplayer games), and visiting adult sites. Participants rated how often, typically, they engage in each type of activity during a weekday from 1 = “never” to 5 = “very often.” These items measure different types of activities and do not constitute a single scale, rather they are treated separately, with higher scores in each item indicating more frequent engagement in that type of activity.
Procedure
All anonymous responses to the self-report instruments were collected during a regular school-day in school computer rooms, in the presence of the class teacher and of one trained master’s student, from January to March 2017. Prior to data collection, participants were assured confidentiality and they were told that they could withdraw from the study at any time with no consequences. After completing the questionnaires, students were thanked for their participation in the survey and researchers answered any students’ questions. The research protocol was approved by the Ethics Committee for Psychological Research at the University of (blinded for peer review).
Data Analysis
In mixture modeling, indicator variables are used to identify an underlying latent categorical variable. We performed latent profile analysis in Mplus 8.1 (Muthén & Muthén, 1998–2017) of the three victimization scores (i.e., overt victimization, relational victimization, and cyber-victimization) to identify subgroups of victims. For sake of interpretability, the three victimization scores were standardized so that positive scores indicated scores above the sample mean and negative scores indicated scores below the mean.
Latent profile analysis consists of an exploratory approach in which the number of latent classes is not known a-priori and its aim is to identify the most parsimonious number of classes that describes the association between the selected variables (Nylund, Asparouhov, & Muthén, 2007). It is therefore recommended to first estimate a model with one single class and then to estimate subsequent models including successively more classes until both fit statistics and substantive interpretation indicate a model that identifies the most appropriate number of groups (Galovan, Drouin, & McDaniel, 2018; Nylund et al., 2007). The overall fit of the models was compared via the Akaike information criterion (AIC), the Bayesian information criterion (BIC), the sample size-adjusted Bayesian information criterion (aBIC), the Lo-Mendell-Rubin Likelihood Ratio Test (LMR), and the Bootstrap Likelihood Ratio test (BLRT). Smaller values of AIC, BIC and aBIC indicate better fit, whereas significant p-values associated with LMR and BLRT indicate significant improvement in model fit relative to the solution with one less class. Moreover, we used entropy to indicate quality of correct classification (entropy ranges between 0 and 1, with values higher than 0.80 indicating good classification quality; Celeux & Soromenho, 1996). However, beyond fit indices, a crucial criterion is also class interpretability, that is, that the final solution consists of theoretically meaningful classes. Indeed, even when statistical tests suggest more classes, the simpler model may be more appropriate for theoretical and research purposes (Nylund et al., 2007; Waasdorp & Bradshaw, 2011). For example, a supplementary class may simply correspond to the “tail end” of one of the already identified groups or may have too few cases (Dyer & Day, 2015).
After fitting the most appropriate number of classes through the process outlined above, the following step in the analysis was to test for between-class differences. This was done by using the BCH method implemented in Mplus (Asparouhov & Muthen, 2014; Bakk & Vermunt, 2016), which has been found to be preferable to the 3-step procedure because it avoids shifts in latent class in the final stage that the 3-step method is susceptible to (Bakk & Vermunt, 2016). To test for between-group differences this procedure employs a weighted multiple group, where the groups correspond to the latent classes, and thus the class shift is not possible because the classes are known. For all analyses, maximum likelihood estimation with robust standard error (MLR) was used.
First, we tested whether the classes differed in gender composition and age. Then, to answer our main research questions, we tested for between-class differences for each of the correlates with the Wald’s Chi-square test of mean equality. If the overall test indicated significant between-class differences, we conducted pairwise tests by constraining individual class means to be equal and evaluating the Wald statistics.
Results
Description of Latent Classes
Table 1 shows the model fit information for models with different number of latent classes. Inspection of the fit indices suggests that a four-class model best fits the data as fit indices began to level off after the optional classes. The four groups were very well-differentiated (entropy = 0.913). Average posterior probabilities for the membership in each latent class were high (> .85). In addition, interpretation of the identified classes was meaningful and congruent with theory. The model with five classes simply divided victim classes into smaller groups with more extreme scores, which was not useful for our research purposes.
Table 1. Model Fit Statistics for the n-Class Models of Peer Victimization.
|
Model |
Loglikelihood |
AIC |
BIC |
aBIC |
Entropy |
LMR p-value |
BLR p-value |
|
1 class |
-5856.378 |
11724.756 |
11756.122 |
11737.062 |
- |
- |
- |
|
2 classes |
-5300.175 |
10620.351 |
10672.628 |
10640.862 |
0.928 |
< .001 |
< .001 |
|
3 classes |
-5158.453 |
10344.906 |
10418.094 |
10373.621 |
0.879 |
.178 |
< .001 |
|
4 classes |
-5008.160 |
10052.320 |
10146.418 |
10089.239 |
0.913 |
.062 |
< .001 |
|
5 classes |
-4912.636 |
9869.272 |
9984.281 |
9914.396 |
0.899 |
.186 |
< .001 |
|
Notes. N = 1377; AIC = Akaike Information Criterion; BIC = Bayesian Information Criterion; aBIC = sample-size adjusted Bayesian Information Criterion; LMR = adjusted Lo-Mendell-Rubin Likelihood Ratio Test; BLR = Bootstrapped Likelihood Ratio test. |
|||||||
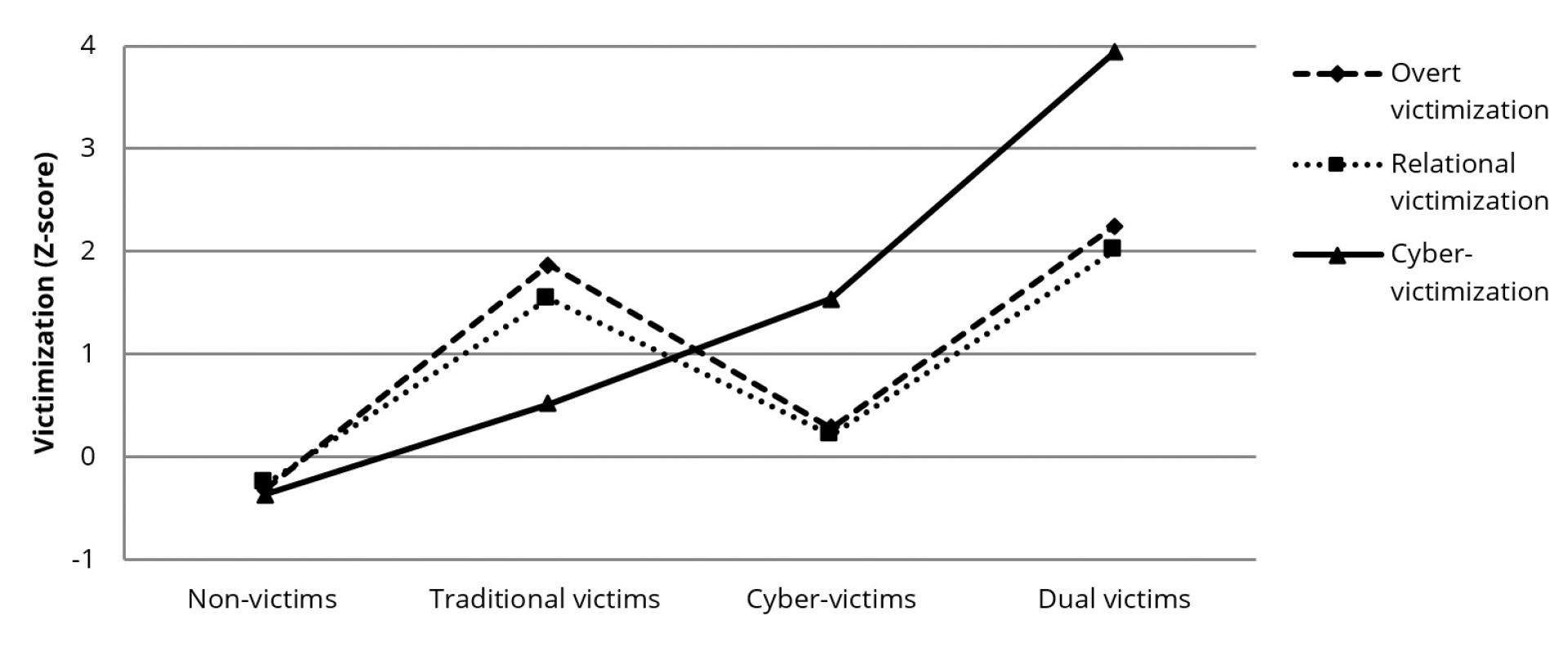
Based on the characteristics of the profiles (see Fig. 1) and previous research, we labeled the classes as (i) “non-victims”, (ii) “traditional victims”, (iii) “cyber-victims”, (iv) “dual victims”. Non-victims (N = 1096, 79.6% of the sample) had the lowest scores in both traditional and cyber-victimization, with all standardized scores below the sample mean. Traditional victims (N = 127, 9.2% of the sample) reported scores above 1 SD for overt and relational victimization, and lower scores close to the sample mean for cyber-victimization. Conversely, cyber-victims (N = 125, 9.1% of the sample) scored much higher on cyber-victimization than on traditional victimization. Finally, the smallest group included so-called dual victims (N = 29, 2.1% of the total sample), that is, adolescents who had the highest scores (> 2 SD) in all types of victimization.
Once these classes were selected, given the literature on possible gender differences in types of victimization, gender was included as a covariate in the model (i.e., regressing class membership on gender) to check whether it influenced class identification. Results indicated that adding gender to the model did not change the patterns of the classes, further confirming the stability of the classes (Lubke & Muthén, 2007). Specifically, the overall distribution of participants across the classes did not change as a result of including gender. Similarly, the predicted probabilities resulting from the models did not change as a result of the inclusion of this covariate.
Figure 1. Victimization scores by latent class.
Analysis of Between-Class Differences
First, we tested whether the four classes differed by gender composition and mean age. For gender, logistic regression analysis was performed with the non-victims class as the reference group. Only the cyber-victim group differed from non-victims: The odds of belonging to the cyber-victim class compared to the non-victim class was lower for girls (OR = 0.50, SE = 0.25, p = .041). The first row of Table 2 reports the proportion of girls who belong to each victimization group. Regarding age differences, the omnibus Wald test was significant, indicating significant between-group differences in mean age. Results of the pairwise comparisons across the latent victimization classes revealed that cyber-victims were older than students in the other groups, but this difference was very small in magnitude.
Table 2. Variable Means (and Standard Errors) by Different Victim Profiles.
|
Variable |
Non-victims |
Traditional victims |
Cyber-victims |
Dual victims |
Wald χ2 |
p value |
|
Demographics |
|
|
|
|
|
|
|
Gender (% females) |
51.4 |
45.7 |
38.4 |
44.8 |
/ |
/ |
|
Age |
16.08 (.04) c |
16.14 (.13) c |
16.54 (.12) n, t, d |
15.78 (.23) c |
15.21 |
.002 |
|
Problematic Internet Use |
2.19 (.02) t, c, d |
2.62 (.09) n, d |
2.63 (.09) n, d |
3.24 (.17) n, t, c |
78.43 |
< .001 |
|
Motives for using Internet |
|
|
|
|
|
|
|
Coping |
1.85 (.03) t, c, d |
2.24 (.11) n, d |
2.13 (.10) n, d |
2.85 (.23) n, t, c |
38.77 |
< .001 |
|
Conformity |
1.37 (.02) t, c, d |
1.79 (.08) n, c, d |
1.55 (.07) n, t, d |
2.62 (.21) n, t, c |
69.96 |
< .001 |
|
Enhancement |
1.89 (.02) t, c, d |
2.10 (.08) n |
2.17 (.09) n |
2.50 (.21) n |
23.98 |
< .001 |
|
Social |
2.89 (.03) d |
2.94 (.11) d |
3.09 (.10) d |
3.83 (.17) n, t, c |
33.09 |
< .001 |
|
Ethical media use |
2.86 (.01) c, d |
2.79 (.04) c |
2.66 (.04) n, t |
2.58 (.10) n |
28.96 |
< .001 |
|
Online activities |
|
|
|
|
|
|
|
Chatting |
4.32 (.03) c |
4.35 (.09) c |
4.60 (.08) n, t |
4.41 (.17) |
10.87 |
.012 |
|
Using Facebook |
2.46 (.04) c |
2.61 (.15) |
2.98 (.16) n |
3.04 (.31) |
13.96 |
.003 |
|
Ability games |
1.62 (.03) |
1.62 (.10) |
1.81 (.12) |
2.04 (.19) |
7.01 |
.07 |
|
Role-playing games |
1.87 (.04) c, d |
2.13 (.14) d |
2.27 (.15) n |
2.85 (.29) n, t |
19.38 |
< .001 |
|
Visiting adult sites |
1.69 (.03) c, d |
1.88 (.13) c, d |
2.38 (.13) n, t |
2.49 (.25) n, t |
34.86 |
< .001 |
|
Notes. N = 1377; ^ motives for using Internet; initials of group name as subscript letters in the same row indicate significant between-group differences (below the p < 0.05 level) according to pairwise Wald χ2 test of mean equality. |
||||||
Table 2 also reports mean scores and omnibus Wald tests for all the other variables related to Internet usage, which we synthesize in this last section. First, the analysis confirmed that dual victims had the highest level, and non-victims the lowest level, of problematic Internet use. Dual victims also reported the highest levels of coping, conformity, and social motives compared to all the other groups, and higher levels of enhancement motives compared to non-victims. Interestingly, traditional victims were the adolescents with more coping and conformity motives compared to non-victims and, in the latter case, also to cyber-victims. Dual victims also reported a lower level of ethical media use compared to non-victims, while cyber-victims had a lower level of ethical media use than both non-victims and traditional victims.
As far as the frequency of online activities, chatting was the most frequent activity reported by adolescents in all groups, but cyber-victims reported significantly more frequent chatting than both non-victims and traditional victims. Cyber-victims reported to use Facebook more frequently than non-victims. Even though dual victims had the highest mean value for using Facebook, the pairwise comparisons were not statistically significant due to the high standard error. Dual victims also reported significantly higher involvement in role-playing games and visiting adult sites compared to both non-victims and traditional victims. Moreover, cyber-victims played role-playing games more frequently than non-victims and reported to visit adult sites more often that both non-victims and traditional victims. Finally, the omnibus Wald test for ability games was not statistically significant and, therefore, pairwise comparisons were not conducted.
Discussion
The aim of the current study was to analyze the differences in Internet use and online behavior of adolescents who suffer different forms of peer victimization compared to their non-victimized peers. To this end, we adopted a person-centered approach to distinguish adolescents who are more (or solely) victimized online and to compare them to peers who are victimized offline. In support of cumulative risk models (Finkelhor et al., 2007), our main findings indicated that dual victims, that is, youth who reported the highest frequency of both traditional and cyber-victimization, showed the most problematic use of information and communication technologies. Moreover, different patterns of Internet use emerged between cyber-victims and traditional victims.
First, as hypothesized, frequency of engagement in online activities was associated with experiences of online victimization. Interestingly, not all types of online activities were significantly different across victims’ groups. While, overall, chatting was the most frequent activity reported by our participants, adolescents who reported to suffer mainly from cyber-victimization also reported that they usually chat online (e.g., on WhatsApp, Skype, etc.) more intensively than both non-victims and traditional victims. Moreover, cyber-victims also reported to play role-playing games (e.g., multiplayer adventure games) more frequently than non-victims, and to visit adult sites more often that both non-victims and traditional victims, thus sustaining the idea that cyber-victims are more likely to engage in several online activities in order to escape from negative feelings (Boniel-Nissim & Sasson, 2018). However, these findings could also suggest the possibility that involvement in risky online activities may increase chances of victimization. Because this is a cross-sectional study, this possibility cannot be ruled out in our sample. Also, dual victims reported significantly higher involvement in role-playing games and visiting adult sites compared to both non-victims and traditional victims. Lack of differences in frequency of Facebook use between victim groups is consistent with a recent Spanish study by Beltrán-Catalán, Zych, Ortega-Ruiz and Llorent (2018), who did not find a significant difference between traditional victims and dual victims (who they called “mixed” victims) in their frequency of social networking sites use. In that study, however, victims were not compared with non-victimized peers, which we did, finding a significant difference between cyber-victims and non-victims. Adolescents reporting more online victimization also reported to use Facebook more frequently (see Giménez et al., 2015; Navarro et al., 2013).
Results of the other comparisons confirmed that quality of Internet use (that is, what adolescents do online and how they use ICT) can be more informative than just amount of time spent online (Marino, 2018). Indeed, in our sample dual victims had the highest level, and non-victims the lowest level, of problematic Internet use. This result complement previous evidences that so-called dual victims may show the worst adjustment in both offline and online life (Brown et al., 2017; Wachs et al., 2018). However, results about the dual victim group should be interpreted cautiously because in our sample this group was quite small in size. Replications and expansions of the analysis of patterns of Internet use in dual victims in other samples are certainly warranted. Moreover, traditional victims and cyber-victims reported higher levels of problematic Internet use than non-victims, and lower levels compared to dual victims. These findings are consistent with the recent conceptualization of problematic Internet use as a (maladaptive) strategy that victimized youth may use to cope with their negative experience (Boniel-Nissim & Sasson, 2018). Even though the current findings are cross-sectional, as most of the previous evidences about this relationship, a short-term longitudinal study (Gámez-Guadix et al., 2013) has found support to the hypothesis that adolescents who are victims of cyberbullying are more likely to develop problematic Internet use, rather than vice versa.
Importantly, this study was the first to analyze the motives for using Internet as reported by adolescents belonging to different victim profiles. Dual victims reported the highest levels of coping, conformity, and social motives compared to all the other groups, and higher levels of enhancement motives compared to non-victims, thus suggesting their attempt to satisfy several needs by engaging in different online activities. Interestingly, beyond dual victims, traditional victims were the adolescents with more coping and conformity motives compared to non-victims and, in the latter case, also to cyber-victims. Coping motives refer to using Internet to forget about problems and to cheer oneself up when in bad mood, while conformity motives refer to Internet use to be liked by others and not being excluded (Bischof-Kastner et al., 2014). The fact that traditional victims reported to favor these kind of motives further supports the hypothesis that youth who are target of peer victimization in their offline life may tend to use the Internet to escape from their negative face-to-face experiences and related distress, on the one hand, and to try to fit in, enhance their social status, and feel accepted in a peer group, on the other one (Nesi, Choukas-Bradley, & Prinstein, 2018). It remains unclear whether these victims are actually able to satisfy these specific needs in their online life or, conversely, continue to encounter problems in relationships with peers and, in the most negative cases, begin to suffer also from cyber-victimization becoming dual victims. To answer this question multi-wave longitudinal studies that follow youth for some years or intensive longitudinal studies (Espinoza, Gonzales, & Fuligni, 2013) that assess adolescents’ daily experience in short periods of time are required.
Finally, dual victims also reported a lower level of ethical media use compared to non-victims; moreover, lower levels of ethical media use were found for cyber-victims compared to both non-victims and traditional victims. In other terms, our findings confirmed that ethical media use is negatively associated not only with online aggressive behavior but also with experiencing forms of cyber-victimization (Müller et al., 2014; Park et al., 2014). We may speculate that some cyber-victims might behave less ethically online because they may tend to “copy” examples of misbehavior in Internet communication as a result of observational learning (Bandura, 1978). On the other hand, adolescents who use ICT in a more responsible and competent way may be less likely to encounter risks and to suffer cyber-attacks because, for example, they might disclose less personal information or show less provocative online behavior. Similarly, it has been shown that raising students’ awareness about privacy issues helps to reduce cyber-victimization (Ortega-Ruiz, Del Rey, & Casas, 2012). This finding is coherent with the broader idea that cyber-victimization tends to be associated with a variety of risky online behaviors, some of which may depend on the diligence with which youth—and Internet users in general—use ICT.
Limitations
This study has limitations that warrant consideration. First, as already discussed above, the study utilized a cross-sectional design. As such, conclusions regarding the directionality of associations cannot be made. In particular, it would be interesting to analyze over the adolescent years whether specific patterns of Internet use, motives or risky online behaviors increase the risk that traditional victims became dual victims. In addition, information was collected only from adolescents themselves through self-reports. The individual is often the best informant for his/her thoughts (e.g., motives) and own life experiences, such as peer victimization (especially in adolescence, when covert forms of victimization are quite common); moreover, so far reliable alternatives to self-reports to measure cyber-victimization are lacking in the literature. Nonetheless, future studies should see whether the current findings are replicated with alternative measures. Moreover, reliability coefficient of the overt victimization scores was less than optimal, probably due to the fact that this type of peer victimization is less common during adolescence. Also related to the measures used, we did not collect information about participants’ own (cyber)bullying behavior, therefore we were unable to control for the fact that some of the students classified as victims in any of the victim profile were indeed bully/victims, a role that is prevalent especially in cyber-bullying/victimization. Finally, another limitation of the current study deals with the generalizability of the findings to other cultural contexts. The fact that the present data were collected in a European country is a strength, because the study expands the limited number of person-centered studies about different types of victimization conducted outside the United States. At the same time, it remains to be established whether similar findings could be replicated in other populations.
Conclusions
These limitations notwithstanding, the current findings begin to shed light on the online life and behavior of adolescents’ victims. Such preliminary findings are certainly not enough to drive strong conclusions about how victimized youth use ICT and what specific pattern of online behavior characterizes different profiles of adolescent victims. Replications and extensions of this study in other samples, other cultural contexts, and with the analyses of additional Internet-related cognitions and online risky behavior are warranted. However, this study begins to shed light on how different peer victimization experiences intertwine with adolescent Internet use and online lives, confirming that both frequency and quality of Internet use are associated with youth peer victimization.
Concerning practical implications of the results, especially the group of dual victims deserves attention, because experiencing victimization online and offline is related to adverse psycho-social outcomes (Cross, Lester, & Barnes, 2015; Gradinger, Strohmeier, & Spiel, 2009; Waasdorp & Bradshaw, 2015). As this group shows the highest problematic Internet use and coping and conformity motives for Internet use as well as – together with cyber-victims – the most frequent use of adult sites and the lowest ethical media use, prevention efforts to enhance media literacy and a positive online communication among youth seem highly relevant. Evidence-based intervention programs implemented in different countries have showed that disclosing personal information in a reflected way, treating others online in a fair and ethical manner and supporting victims as bystanders can help to reduce cyber-victimization (Cross et al., 2016; Ortega-Ruiz et al., 2012; Wölfer et al., 2014) and should be accompanied with prevention of traditional bullying as well. Furthermore, educational programs aimed at preventing problematic Internet use and teaching positive social media usage may help also preventing online victimization or, at least, reducing its negative impact on adolescents’ well-being (e.g., Ke & Wong, 2018).
Moreover, a novelty of this study was the analysis of the motives for using Internet associated with being victimized. Results of this study, if replicated, may contribute to inform the development of prevention and intervention programs for adolescents. More broadly, it has been shown that targeting the motives for a given behavior can be an effective strategy to prevent people’s engagement in problematic behaviors (Király et al., 2015). For example, some studies reported the efficacy of evidence-based interventions tailored to specific motives to prevent alcohol abuse and to reduce problematic gambling among adolescents and young adults (Canale et al., 2016; Disperati et al., 2015). In our context, developing interventions that explicitly include reflections and activities about the specific motives that are associated with victimization experiences might be of value.

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
Copyright © 2019 Gianluca Gini, Claudia Marino, Jia-Yan Xie, Jan Pfetsch, Tiziana Pozzoli



